Cyberattacks targeting operational technology (OT) systems, such as power grids, have evolved into highly sophisticated threats. In the last two decades, state-sponsored adversaries have increasingly weaponised protocol-compliant attacks, as was the case in the Industroyer malware that masquerades attack using a legitimate protocol format. These attacks exploit trusted communication frameworks, such as the IEC 61850-manufacturing message specification (MMS), to compromise intelligent electronic devices (IEDs) and destabilise grid operations. MMS is a cornerstone of communication in a smart grid and can be exploited using its feature, remote control command execution on IEDs. This project addresses critical security vulnerabilities in the MMS protocol. Its core innovation lies in tackling the scarcity of MMS attack datasets by training machine-learning models to learn a baseline of normal operational behavior. The system detects sophisticated anomalies, including zero-day malware and replay attacks, by monitoring MMS message patterns such as read, write, and service support options for signs of malicious intent.
Architecture overview
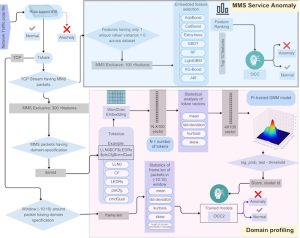
The architecture has three main components.
1. Rule-based IDS: Signature-based rules for known attack patterns and protocol violations.
2. MMS service anomaly detection: To define the one-class classification (OCC) model’s boundary, a supervised attack detection is performed to pinpoint the most critical features of the MMS application layer, which are used to tighten the decision boundary for enhanced anomaly detection.
3. Domain profiling: This method employs Word2Vec to learn semantic embeddings from IED domain specifications, which allows the precise identification of targeted virtual manufacturing device (VMD) objects in MMS messages. Subsequently, the cluster assignments from these embeddings, along with other message features, are leveraged to define the boundary for the OCC model.
A key achievement of the project is the identification of important features of the MMS application layer and advanced preprocessing of domain-specific features, which are essential for accurately modelling the MMS communication behaviour of IEDs and their VMDs. This approach enables highly effective and reliable threat alerts, contributing to the resilience of modern smart-grid infrastructures.
Publications
1. Kishan Baranwal and Haresh Dagale, ‘A Survey of Machine Learning Resources for IEC 61850 in Power Grid Security’ [accepted at 11th IEEE International Conference on intelligent data and security (IDS) 2025; New York, United States]
2. Kishan Baranwal, Haresh Dagale, and Vikas Bishnoi, ‘Critical IEC 61850 MMS Feature Selection for ML-Driven IDS’ [accepted at 11th ACM Cyber-Physical System Security Workshop (CPSS) 2025; Hanoi, Vietnam]
3. Kishan Baranwal and Haresh Dagale, ‘Domain-Aware Machine Learning for IEC 61850 MMS Intrusion Detection’ [accepted at IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm) 2025; Toronto, Canada]
Faculty: Haresh Dagale