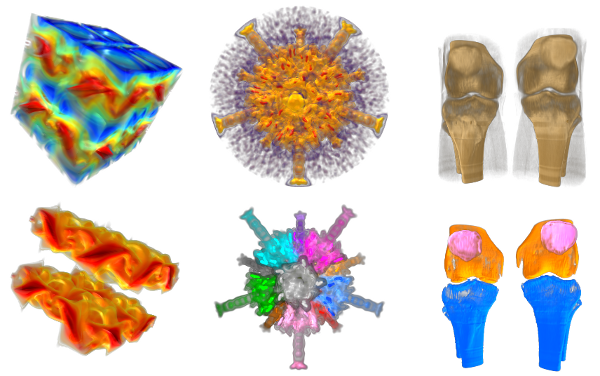
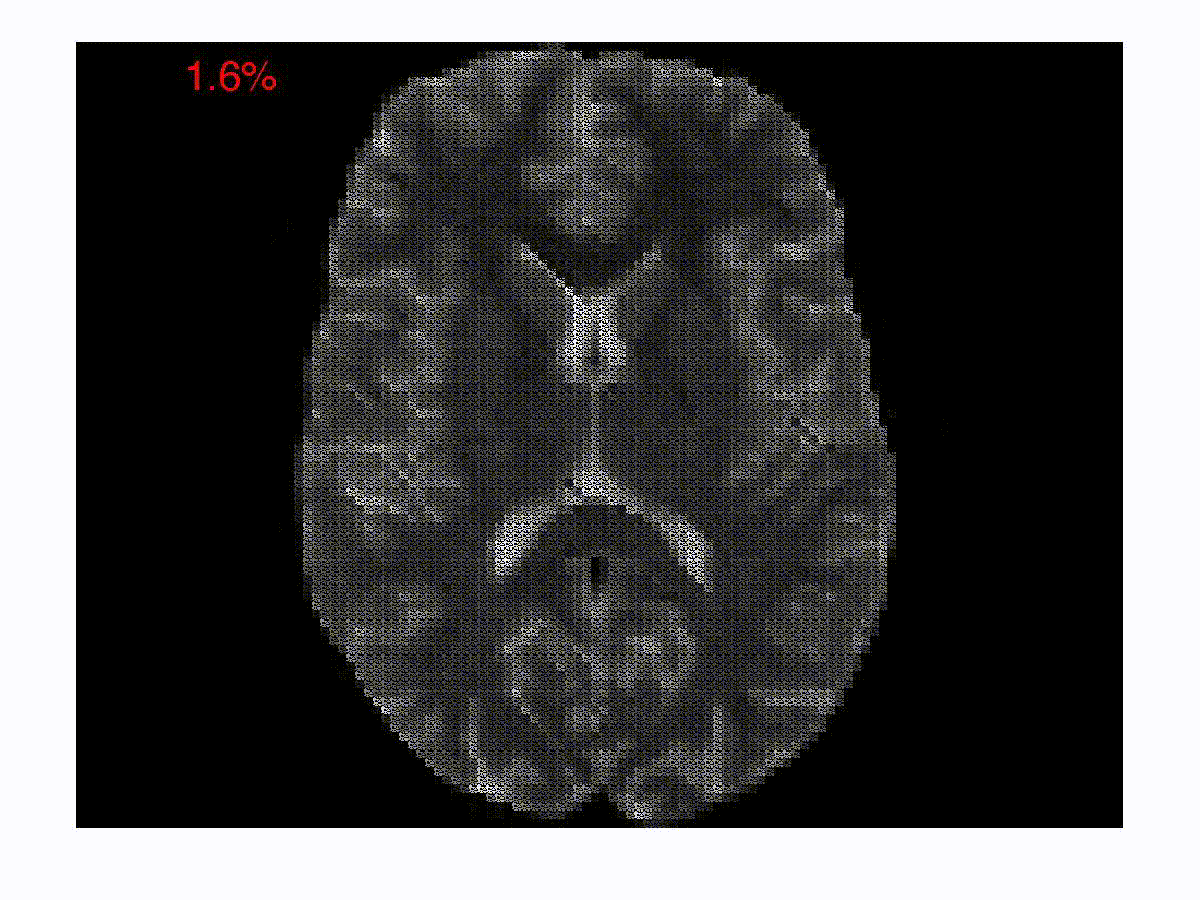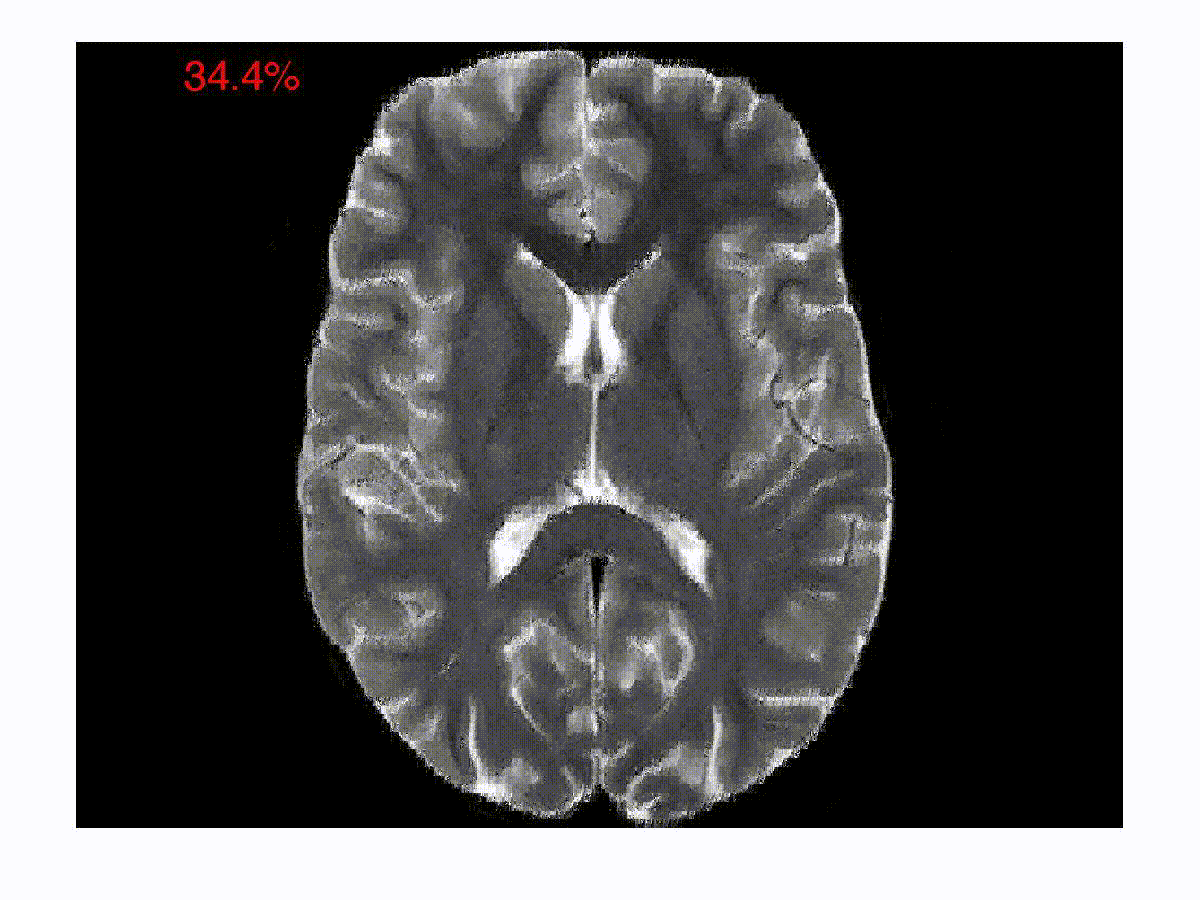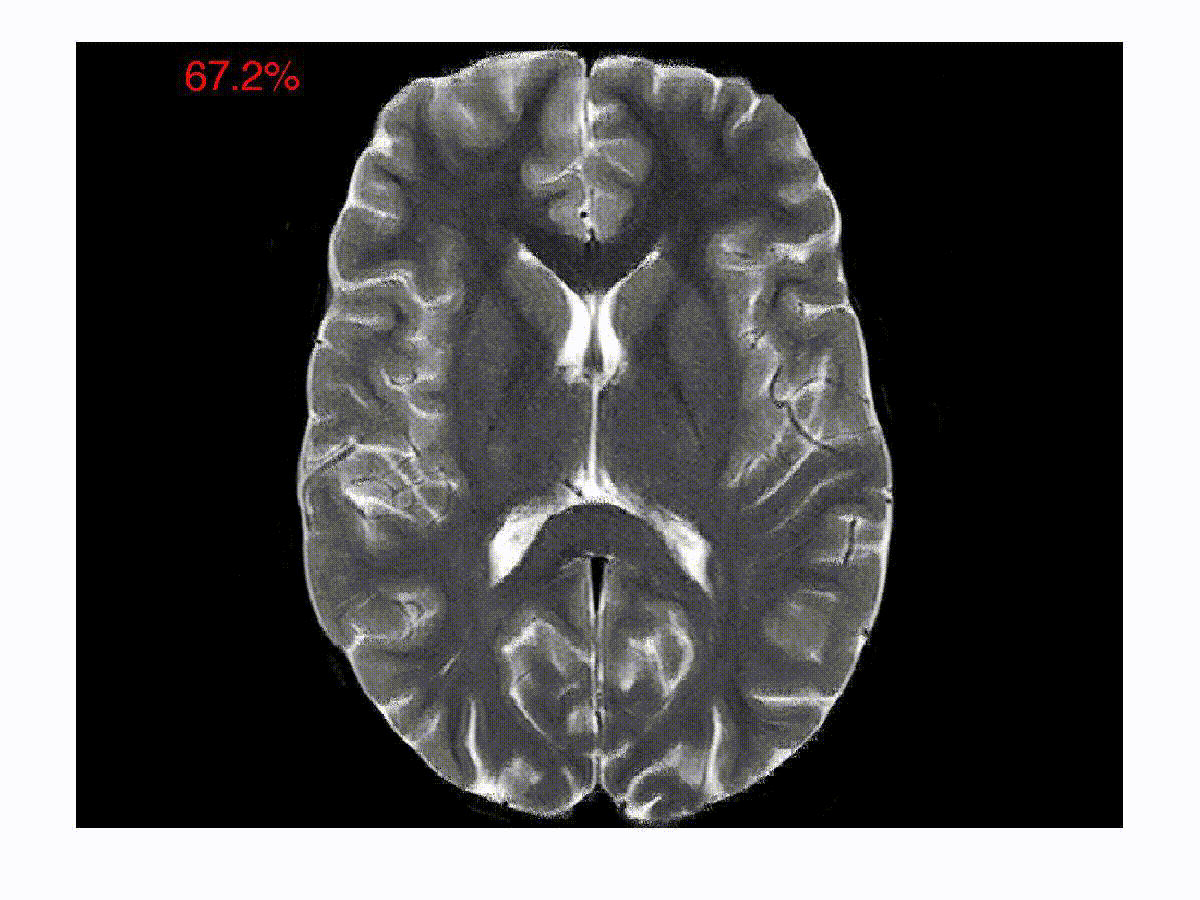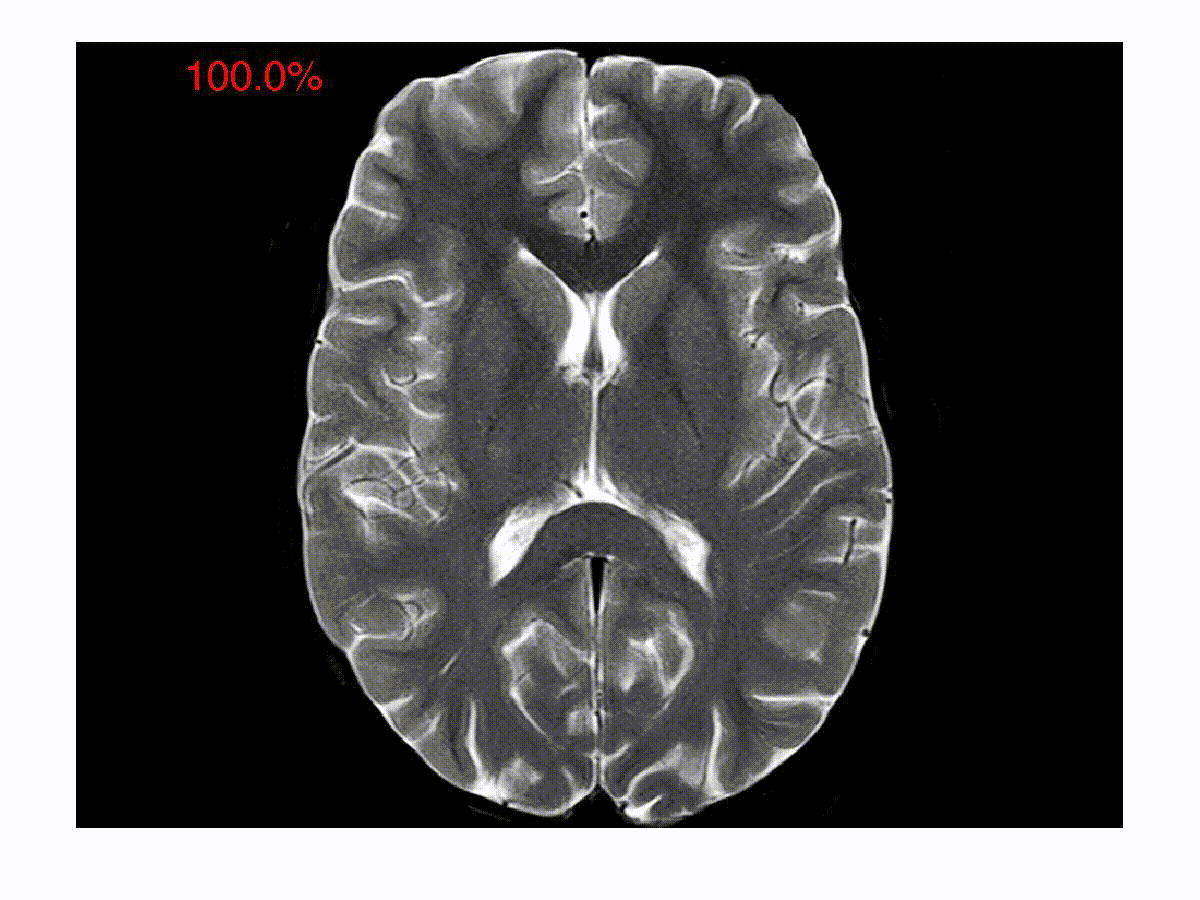
Symmetry in Scalar Fields
Automatic detection of symmetry is a challenging problem because both...
read more...
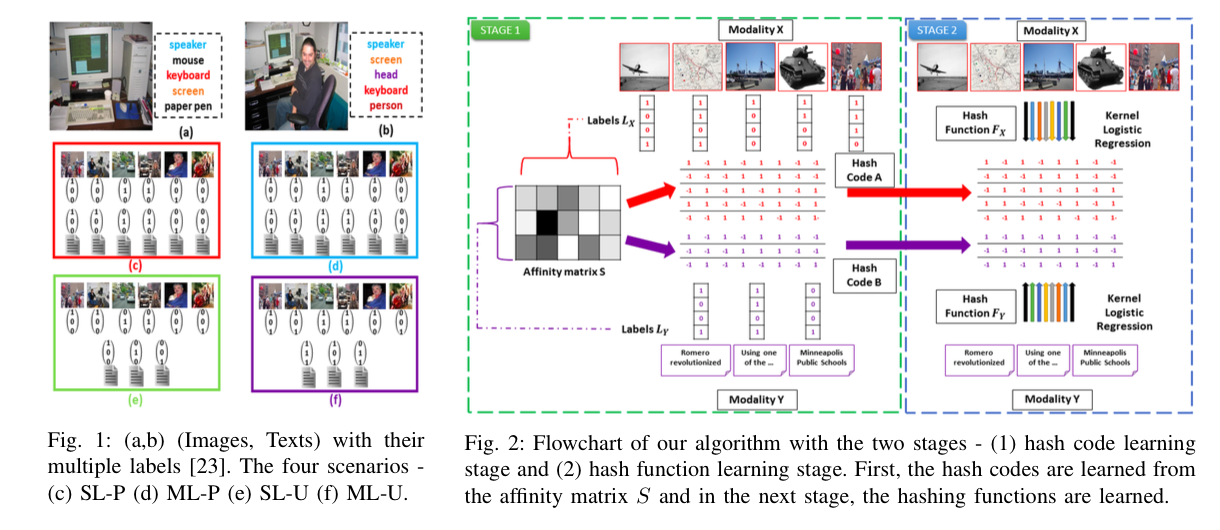
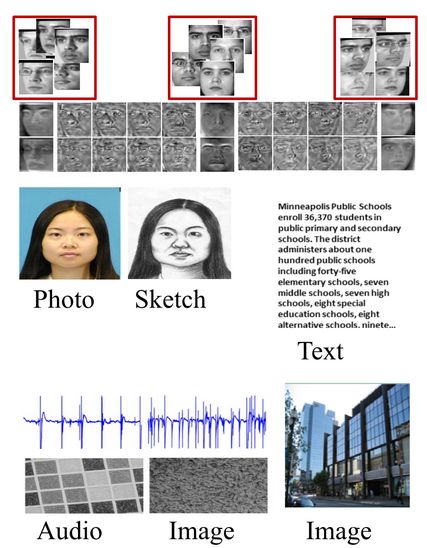
Cross-Modal Retrieval
Due to increase in the number of sources of data,...
read more...
Using Statistical Mechanics to understand depth in Deep Networks
Understanding the representational power of Restricted Boltzmann Machines (RBMs) with...
read more...
Neural programming and program analysis
Automatically synthesising programs and analysing their behaviour is considered a...
read more...
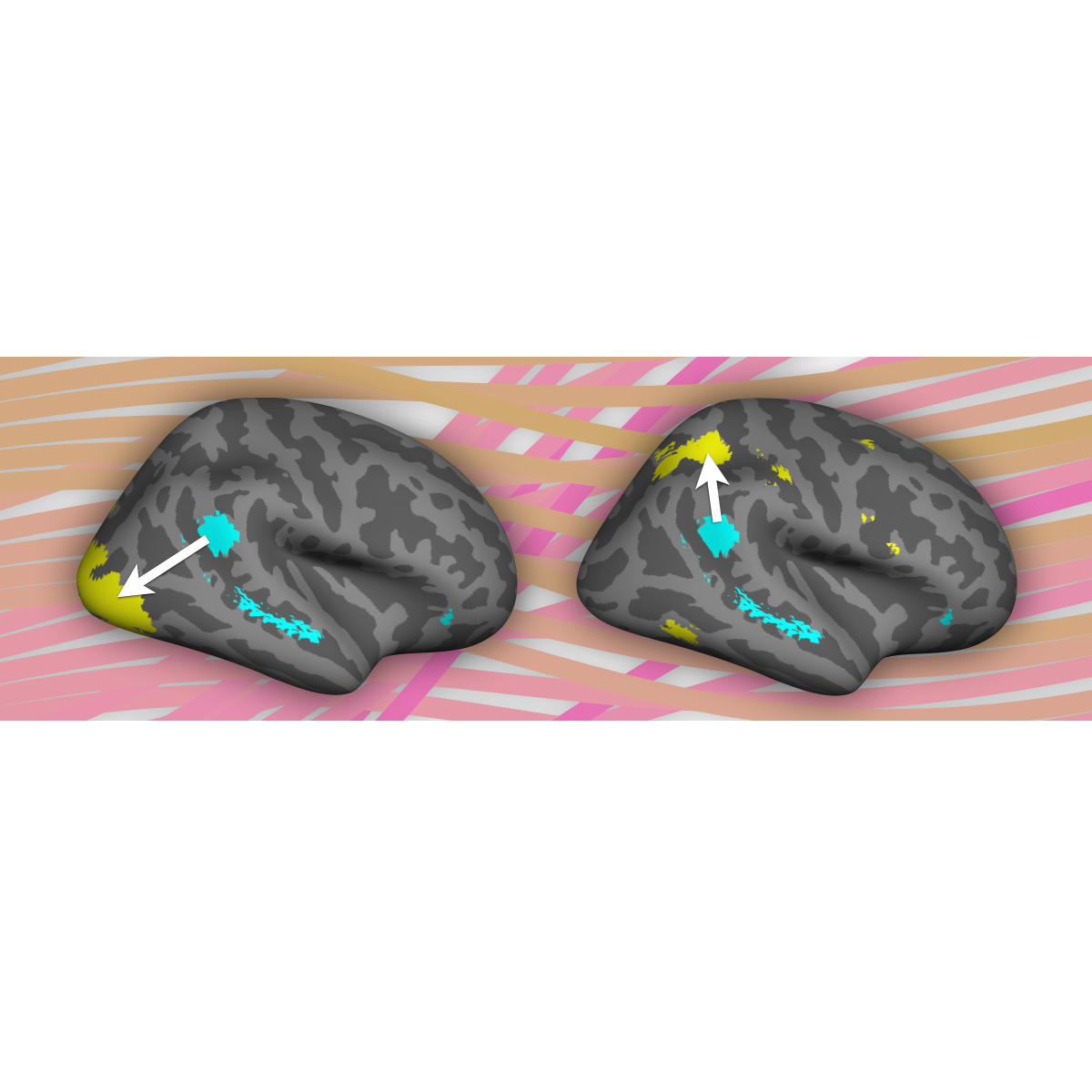
Neural computations underlying cognition
How does our brain enable us to pay attention selectively...
read more...
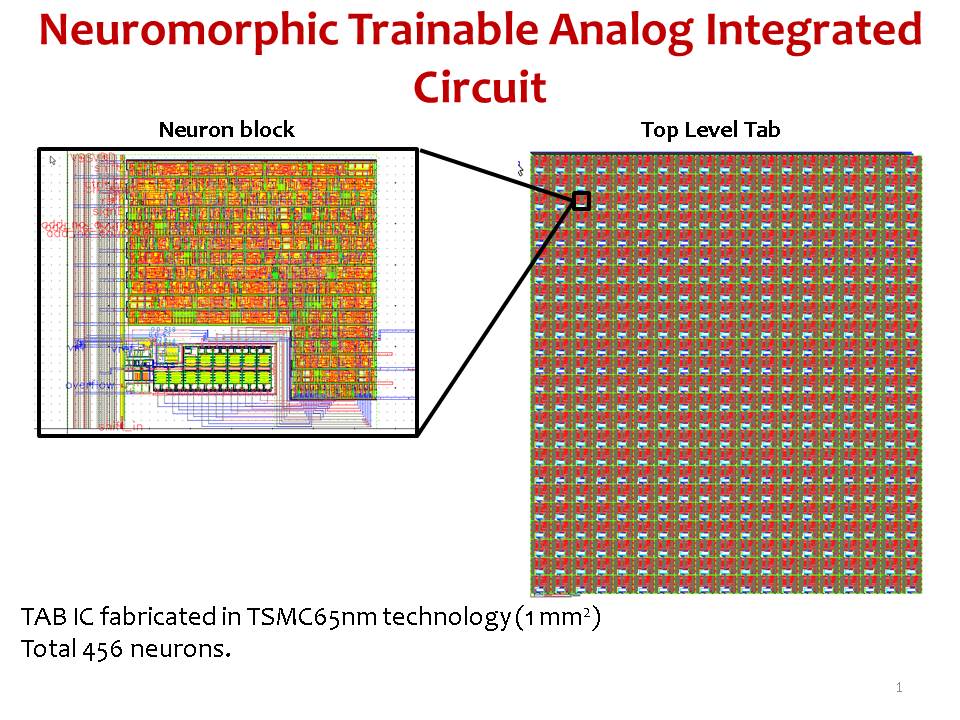
An analog neuromorphic co-processor that utilizes device mismatch for learning applications
As the integrated circuit (IC) technology advances into smaller nanometre...
read more...
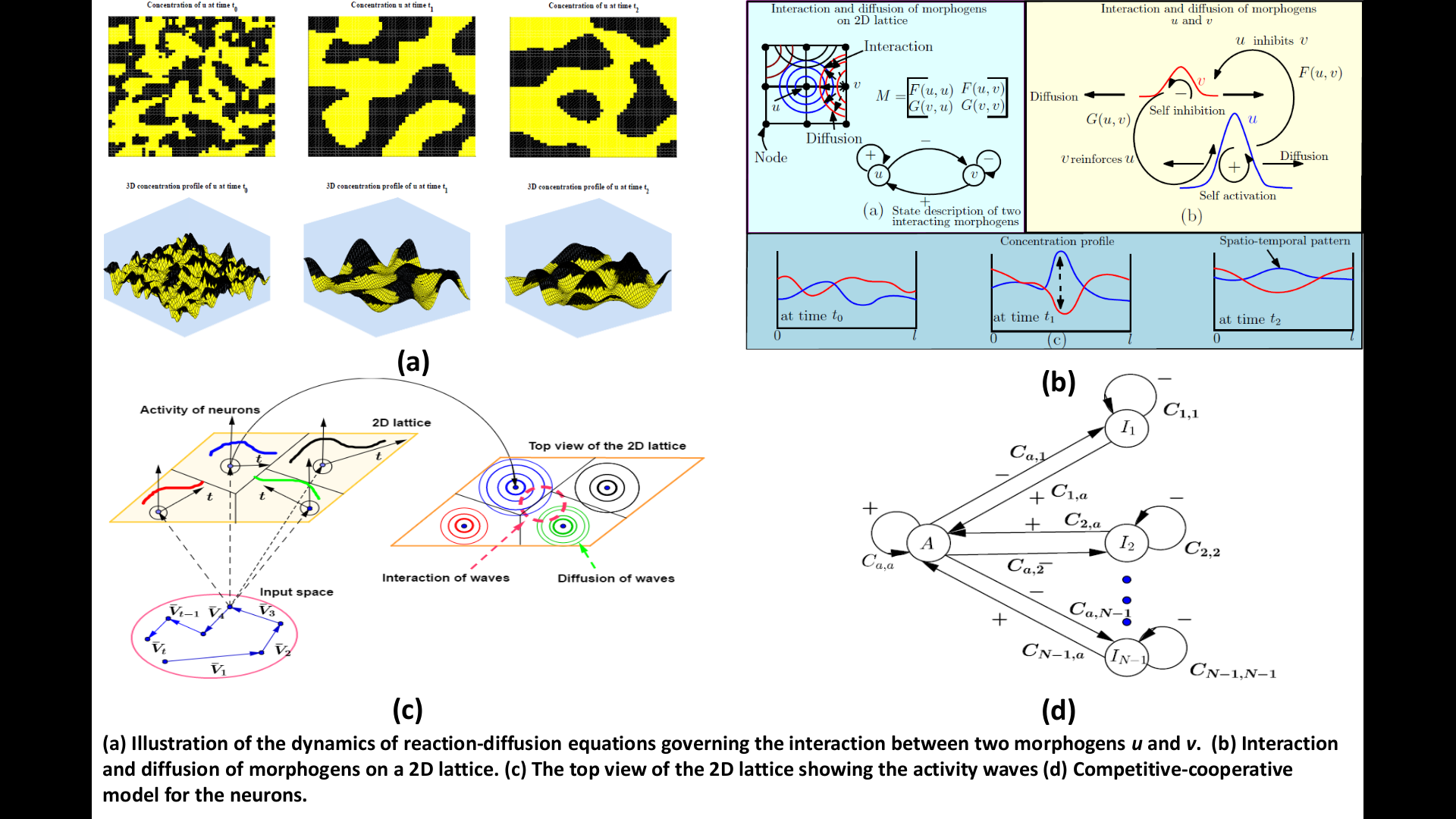
Temporal Self-Organization: A Reaction-Diffusion Framework for Spatiotemporal Memories
Self-organizing maps find numerous applications in learning, clustering and recalling...
read more...
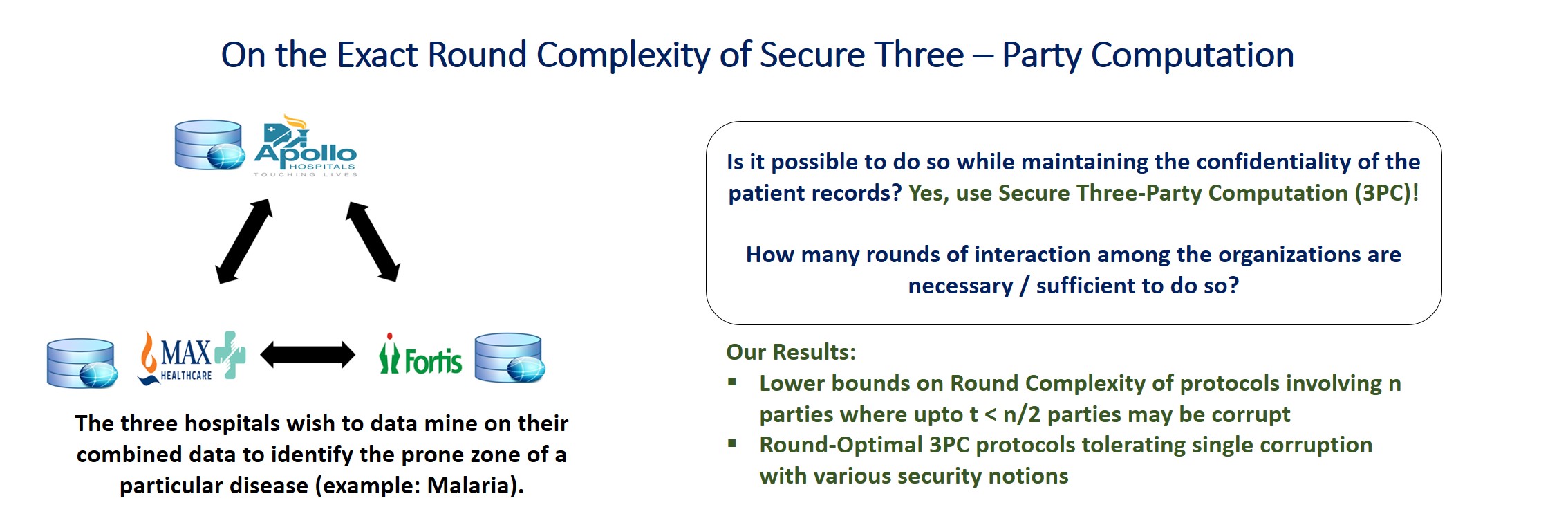
On the exact round complexity of secure three party computation
This work was done by Prof. Arpita Patra and Divya...
read more...
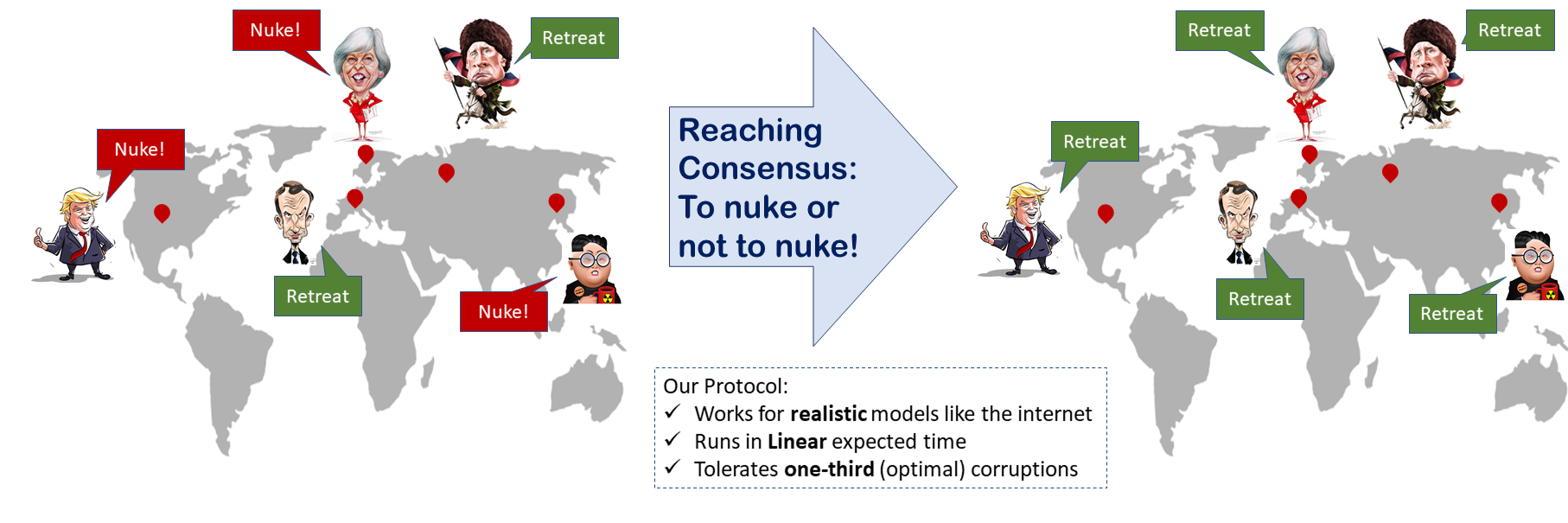
Almost-Surely Terminating Asynchronous Byzantine Agreement
This work was done by Laasya Bangalore, Ashish Choudhury, and...
read more...
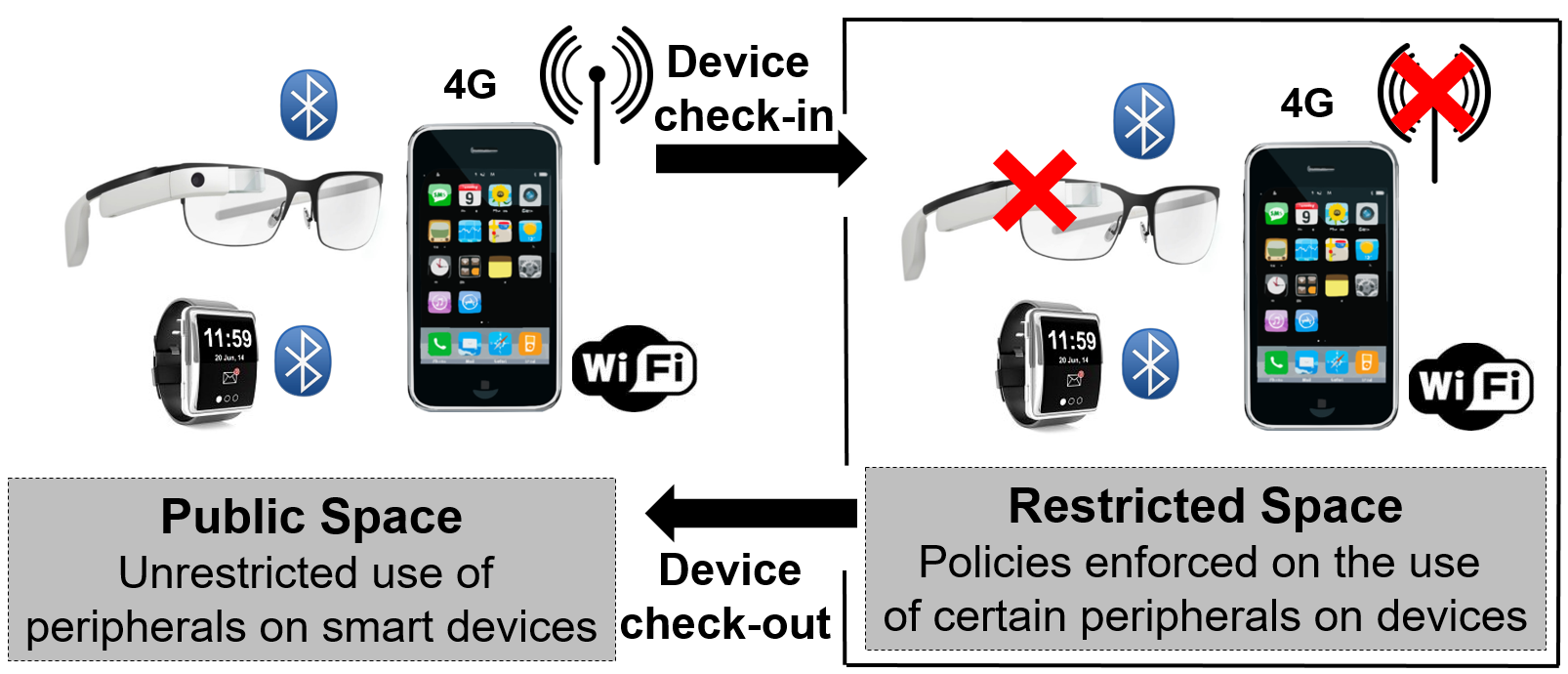
Regulating Smart Devices in Restricted Spaces
This work appears in the 2016 ACM International Conference on...
read more...
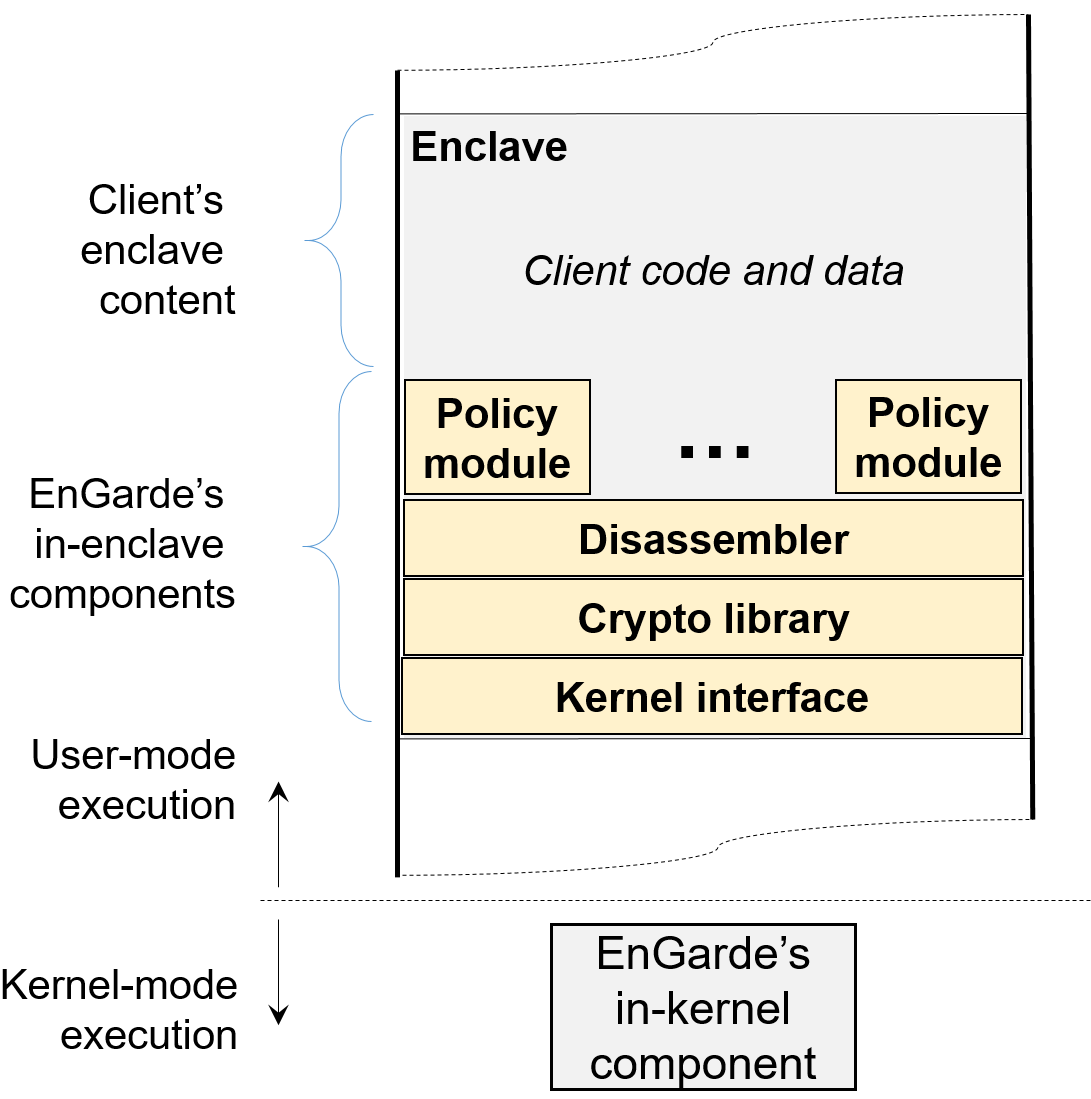
Secure and Private Cloud Computing with Trusted Hardware
This work appears in the 2017 International Conference on Distributed...
read more...
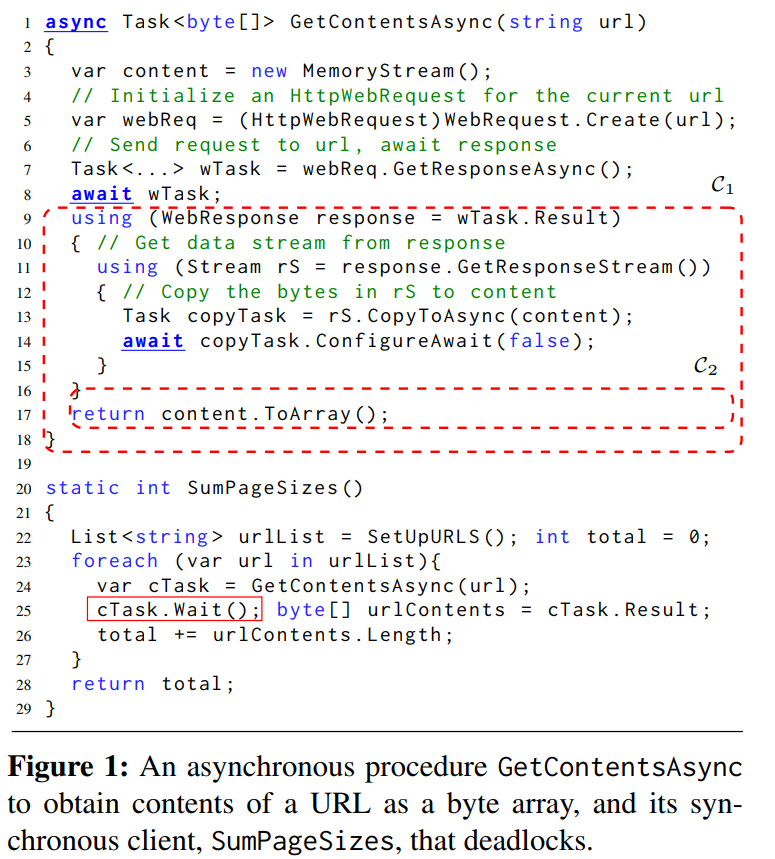
Analysis of Concurrent Software
Event-driven concurrent programming is central in many software domains such...
read more...
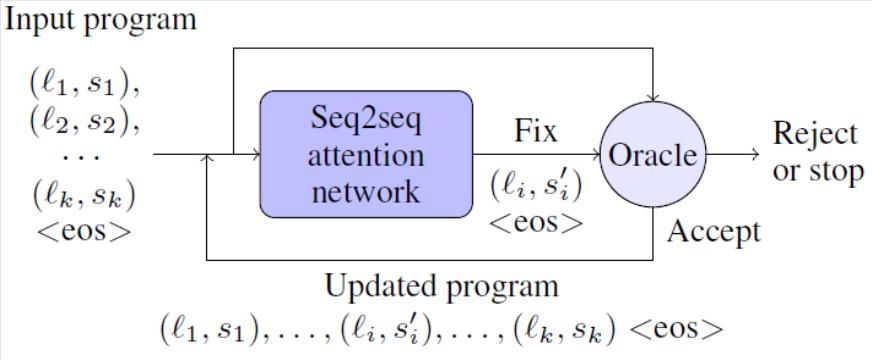
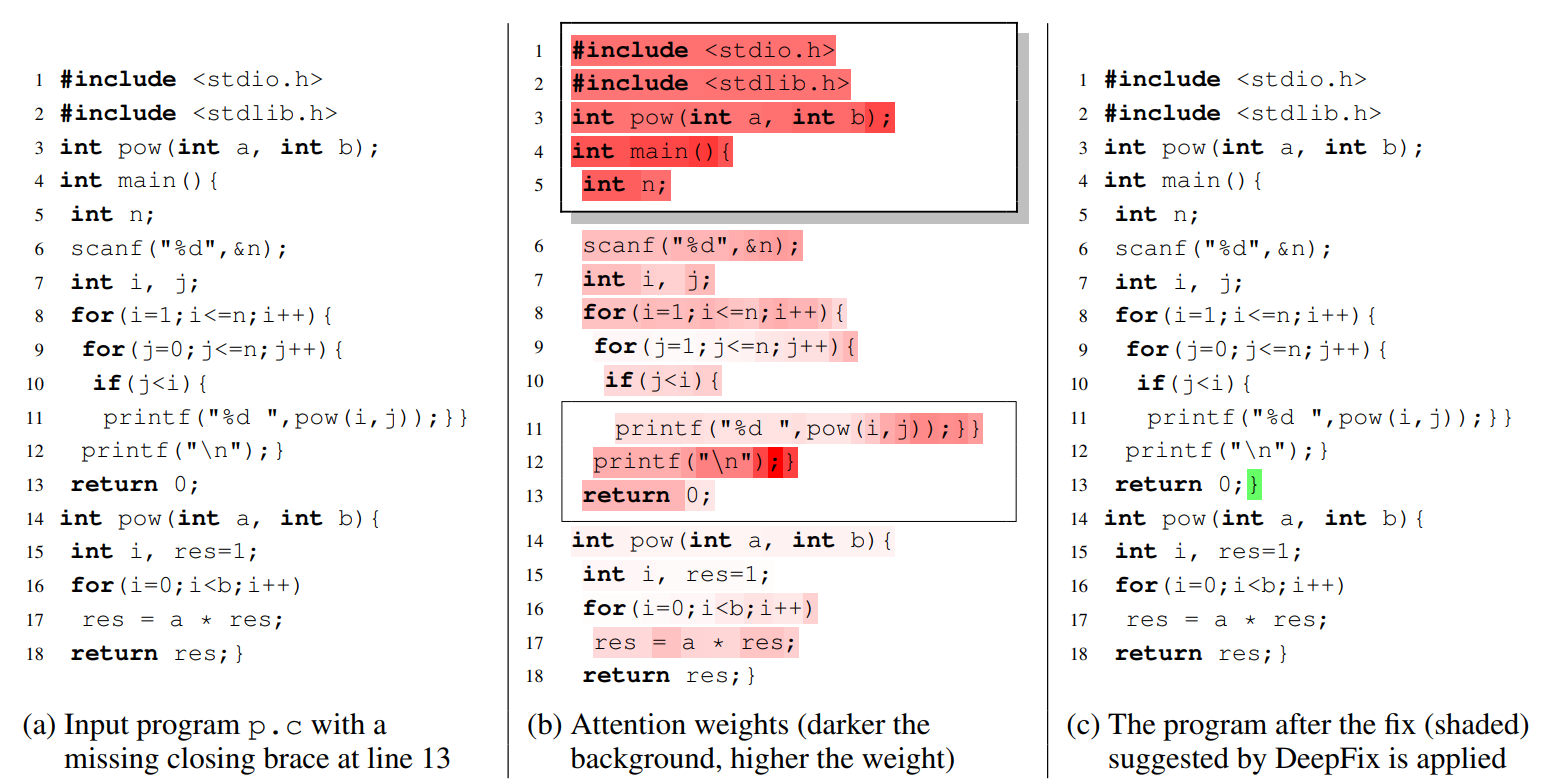
Automatic Bug-Fixing in Programs
Software developers spend enormous time in finding and fixing bugs....
read more...
Statistical Inference under Privacy Constraints
Independent samples from an unknown probability distribution p on a...
read more...
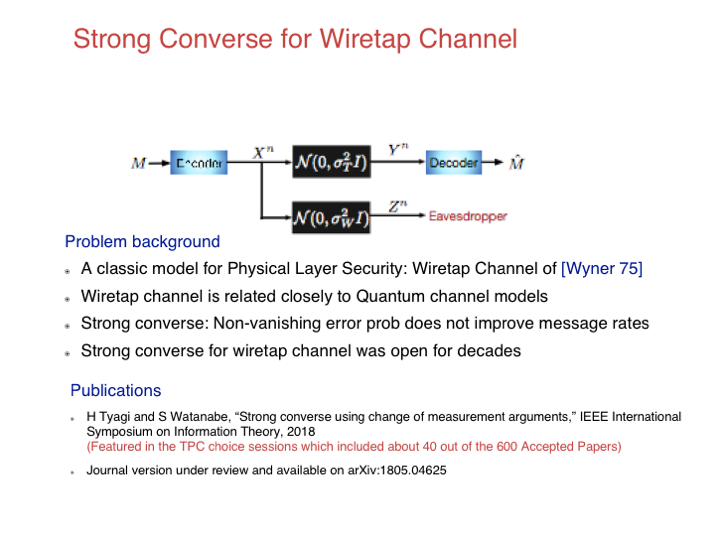
Strong Converse for Wiretap Channel
The strong converse for a coding theorem shows that the...
read more...
Universal Multiparty Secret Key Agreement
Multiple parties observing correlated data seek to recover each other’s...
read more...
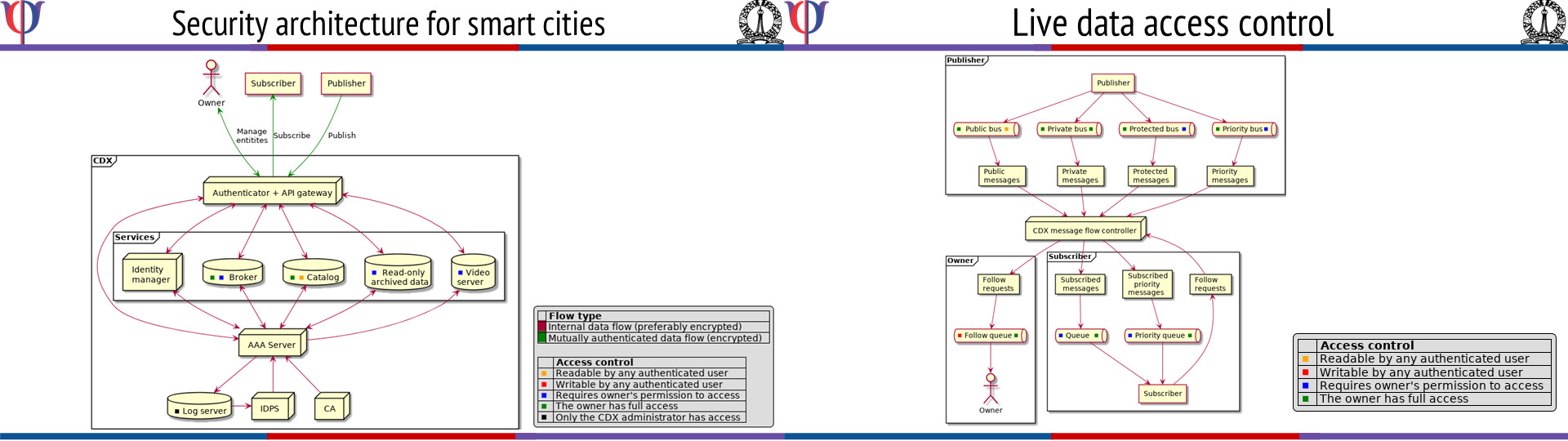
Security for Smart Cities
[Text borrowed from http://www.rbccps.org/smart-city/] The Indian Government has identified Smart...
read more...
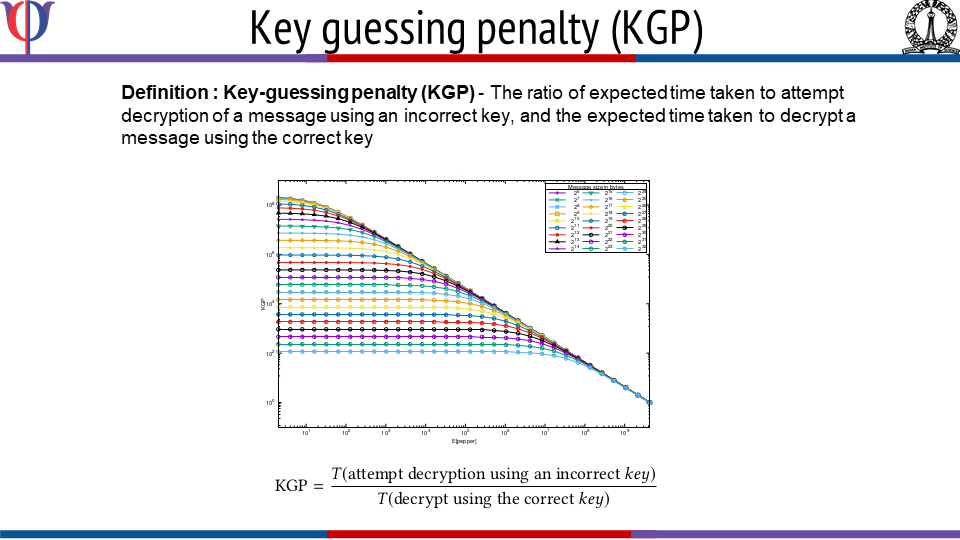
FreeStyle: Customizable, Randomized, and Variable Round Version of Chacha Cipher to Resist Offline Key-guessing
This work introduces Freestyle, a highly customizable, randomized, and variable...
read more...
Differentially-Private Algorithms for Consensus and Convex Optimization
Privacy, and the related issue of security, in CPS is...
read more...
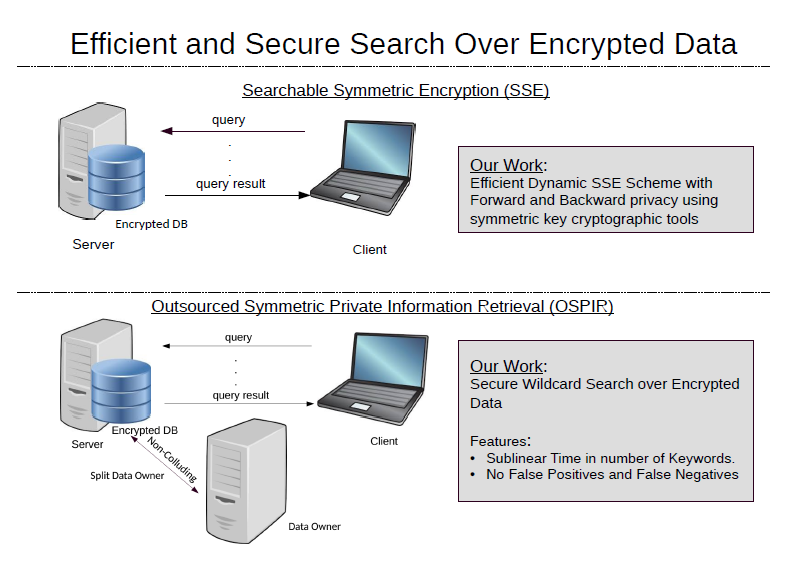
Efficient and Secure Search over Encrypted Data
Due to a variety of crucial benefits, enterprises outsource their...
read more...
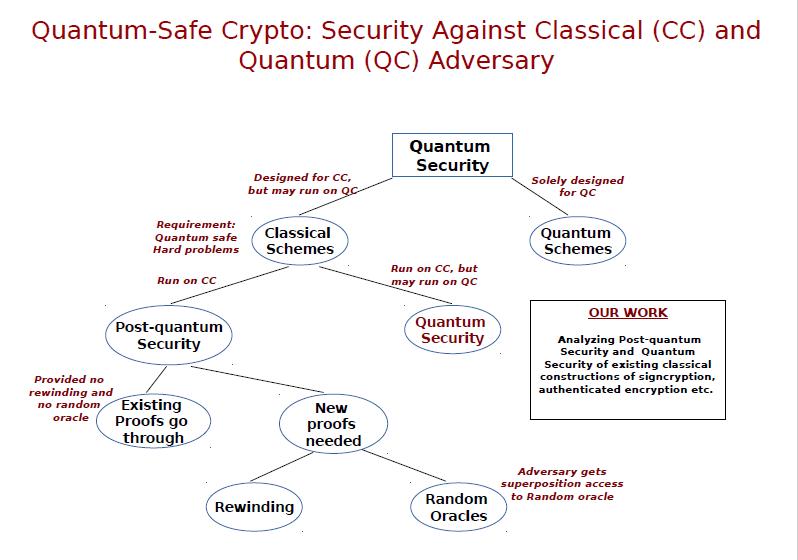
Quantum-safe Cryptography
The possible advent of quantum computers in the foreseeable future...
read more...
Deep Neural Networks for Superresolution of Document and Natural Images
a). Document Image Quality Enhancement Using Deep Neural Network: In...
read more...
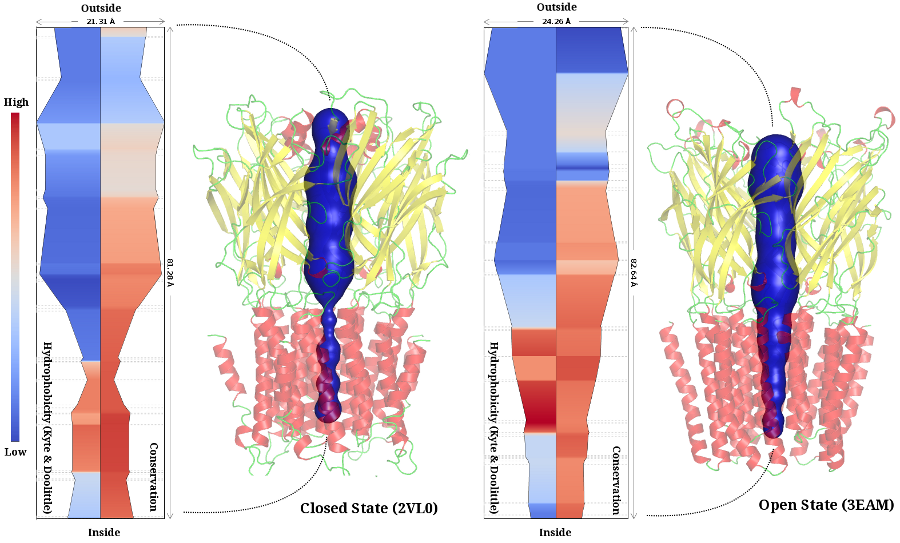
ChExVis: a tool for molecular channel extraction and visualization
A channel is a pathway through empty space within the...
read more...
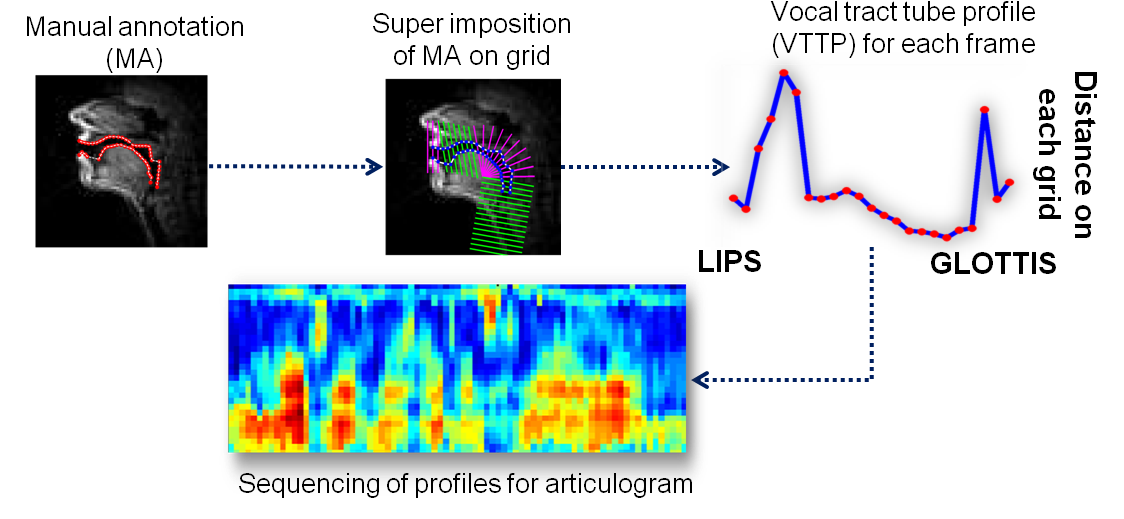
Articulogram for characterizing speaker specific articulation
Speech articulation varies across speakers for producing a speech sound...
read more...
Surveillance Face Recognition and Cross-Modal Retrieval
In the IACV lab, we are looking at different problems...
read more...
Fast Algorithms for Kernel Based Filtering
Smoothing is a fundamental task in low-level image processing that...
read more...
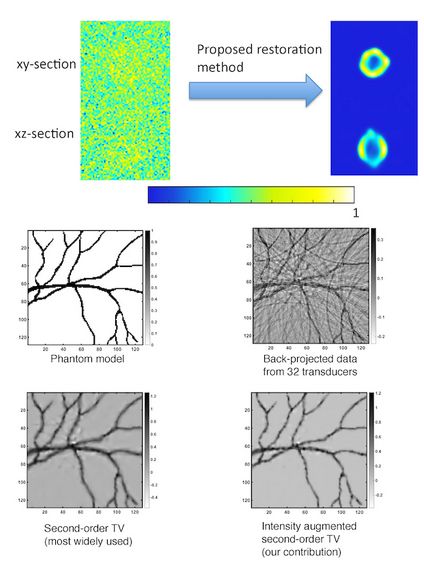
Regularization in Fluorescence Microscopy and Photoacoustic Imaging
Structures imaged by fluorescence microscopy and photo-acoustic imaging (PAT) have...
read more...
Virtual Reality, Image/Video Quality Assessment and Enhancement and Streaming Video
Virtual Reality: We work on several aspects of quantifying user...
read more...
Online Reconstruction Algorithms for Compressed Imaging
One of the focus areas of the Spectrum Lab is...
read more...
Deep Learning Techniques for Solving Inverse Problems
We address the problem of sparse spike deconvolution from noisy...
read more...
Artificial Intelligence for Healthcare Applications
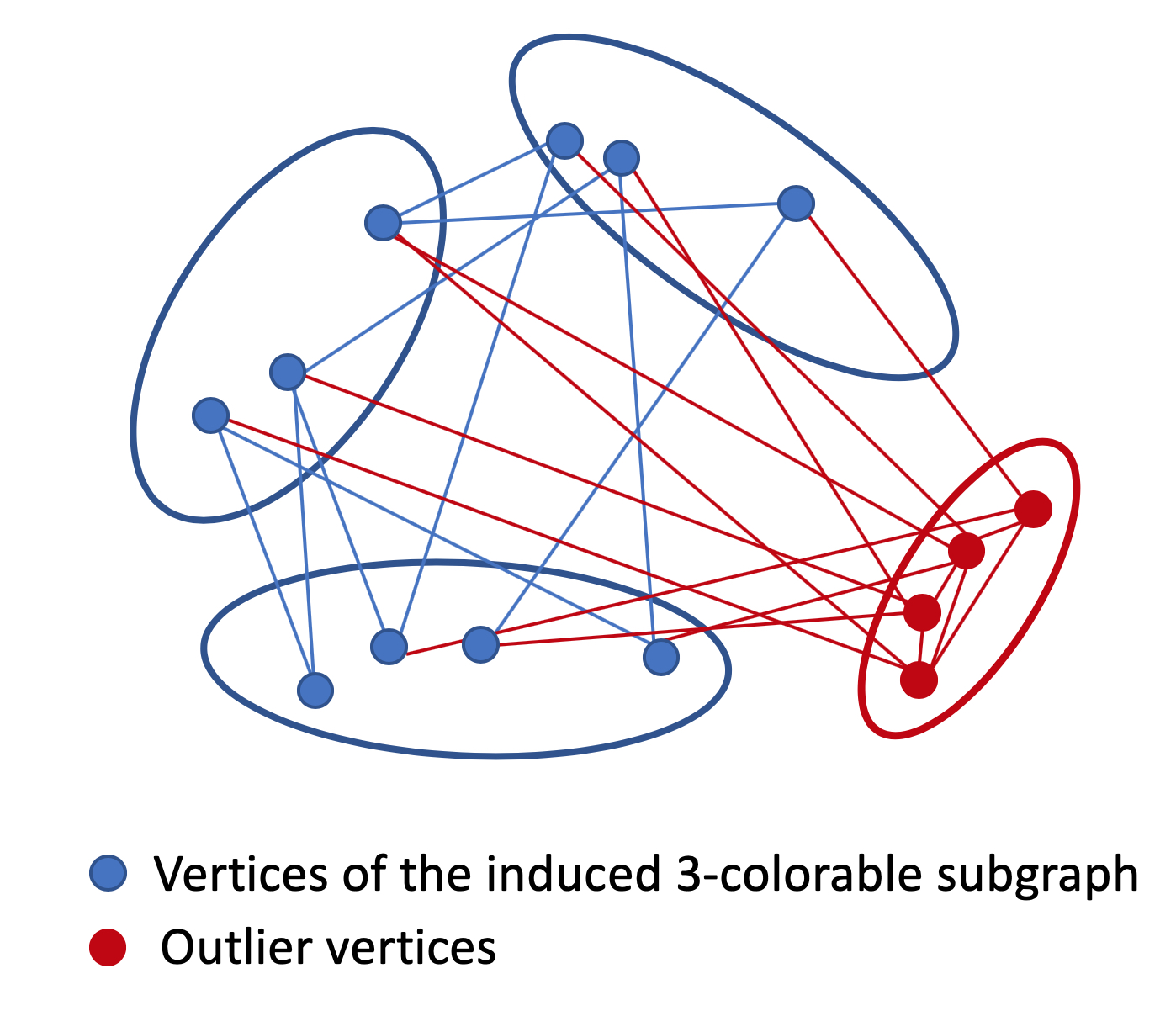
Approximation Algorithms for Partially Colorable Graphs
Graph coloring is a fundamental NP-hard problem in the study...
read more...
Scroll Up