Fairness in an Algorithmic World
Siddharth’s recent work considers fairness from a computation lens. For...
read more...
A Vapnik’s Imperative to Unsupervised Domain Adaptation
The success of deep neural networks, in the advancement of...
read more...
Best Fit Bin Packing with Random Order Revisited
The bin packing problem is a fundamental problem in combinatorial...
read more...
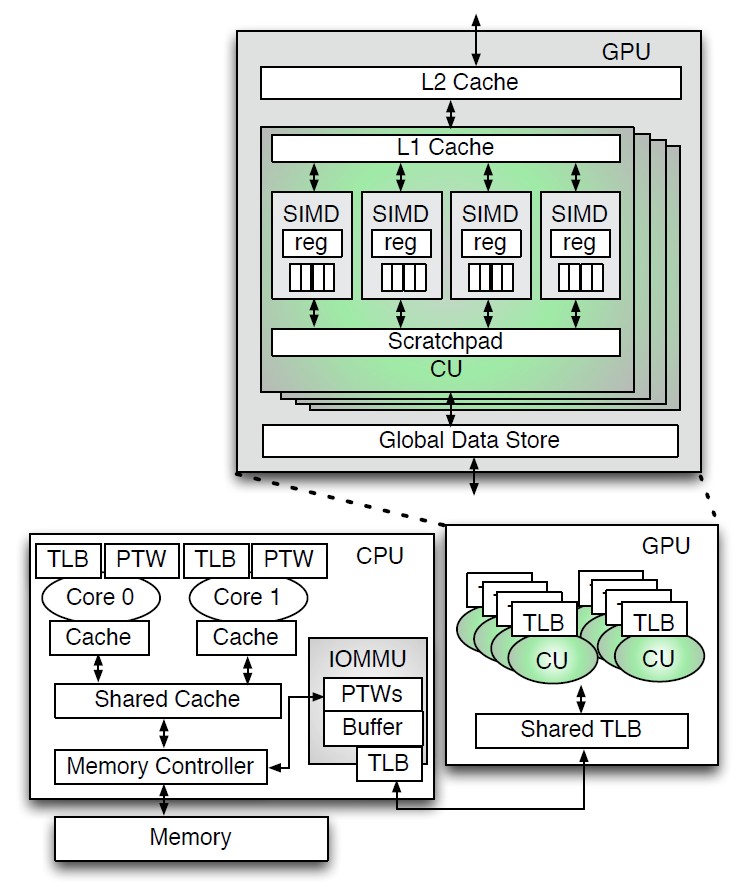
Hardware-software co-design for easily programmable GPUs
Traditionally, the Central Processing Unit or CPU has been the...
read more...
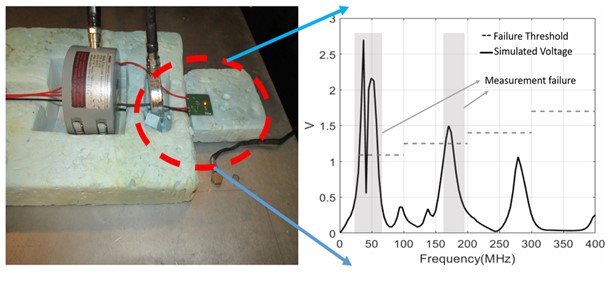
Model-based Simulation Methodology for EMI/EMC
Electromagnetic Interference (EMI) and Electromagnetic Compatibility (EMC) contribute to a...
read more...
Novel Thru-Wall Radar-on-chip Technology
Dr. Gaurab Banerjee and his research group at the ECE...
read more...
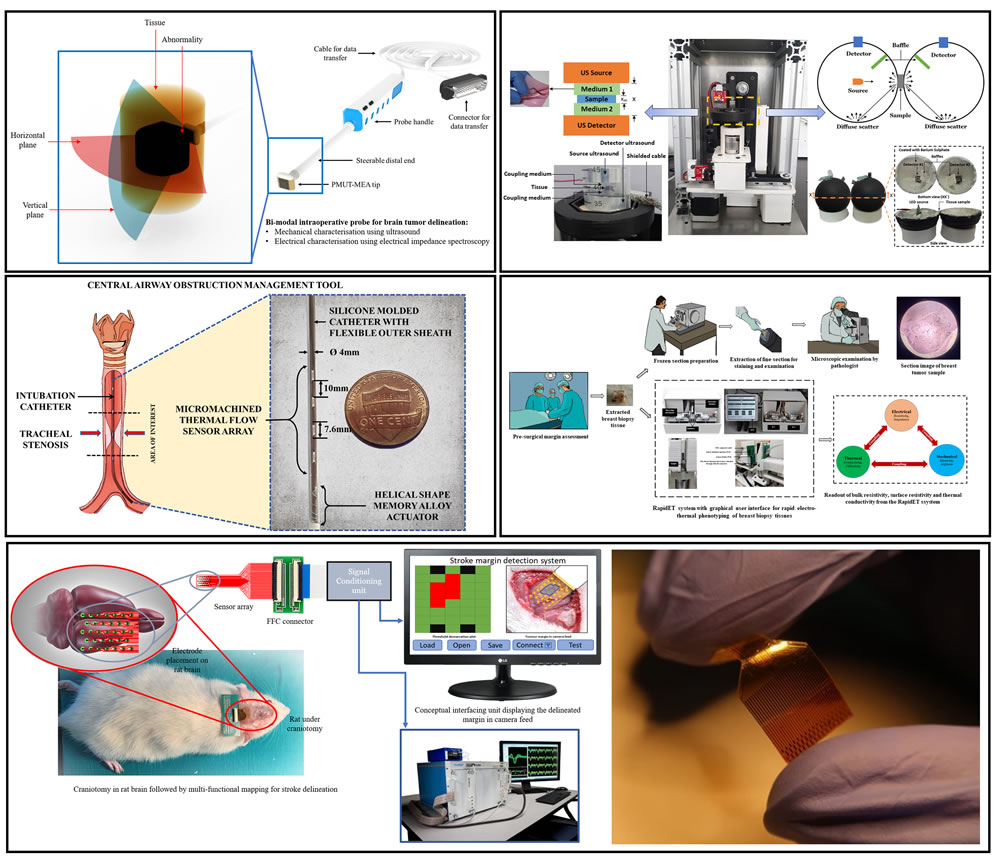
Advanced Healthcare Technologies
The research group at BEES Lab, DESE, is developing advanced...
read more...
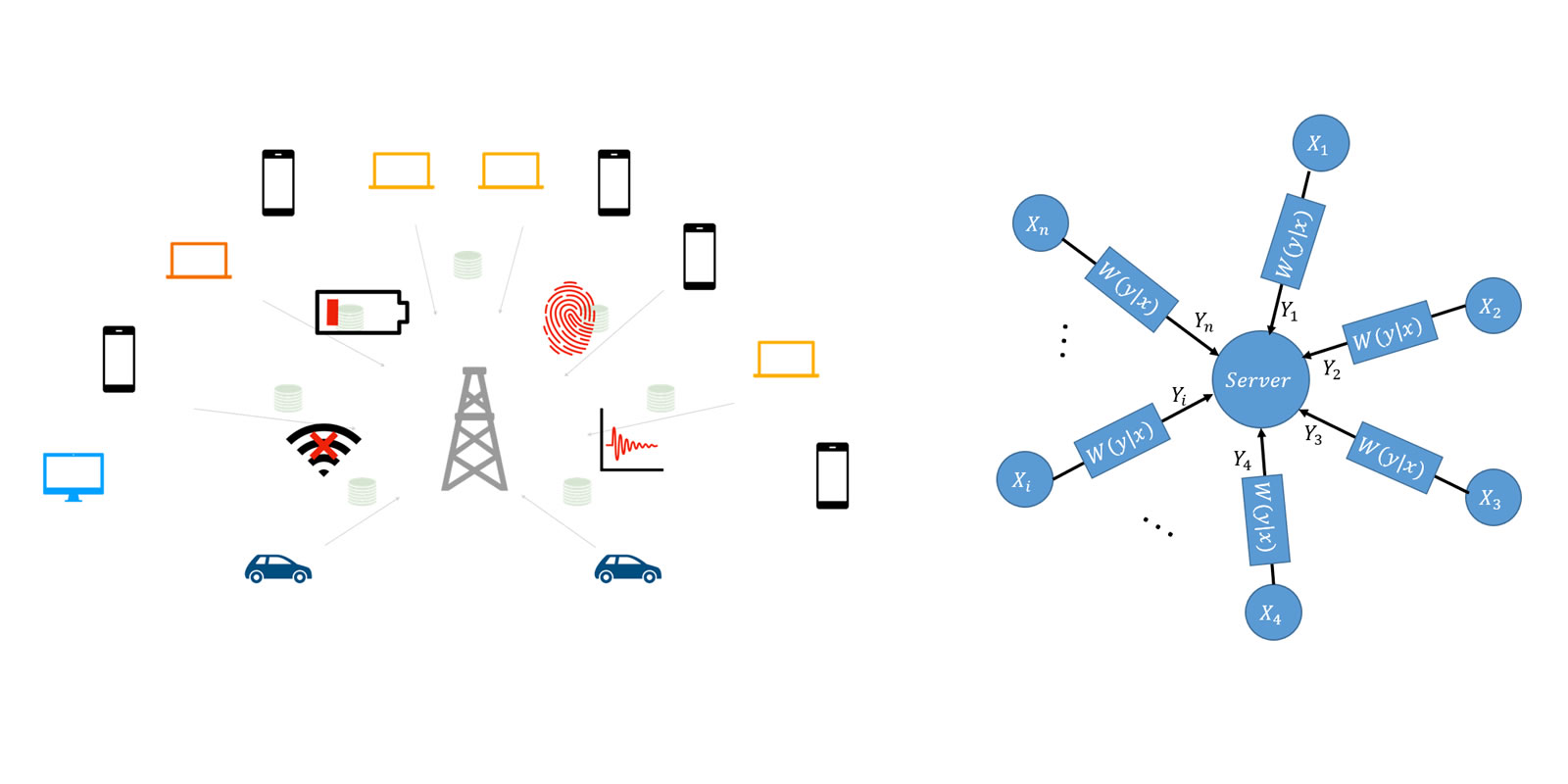
Optimal Algorithms for Statistical Inference and Learning under Information Constraints
Classical statistics assumes that data samples are available in their...
read more...
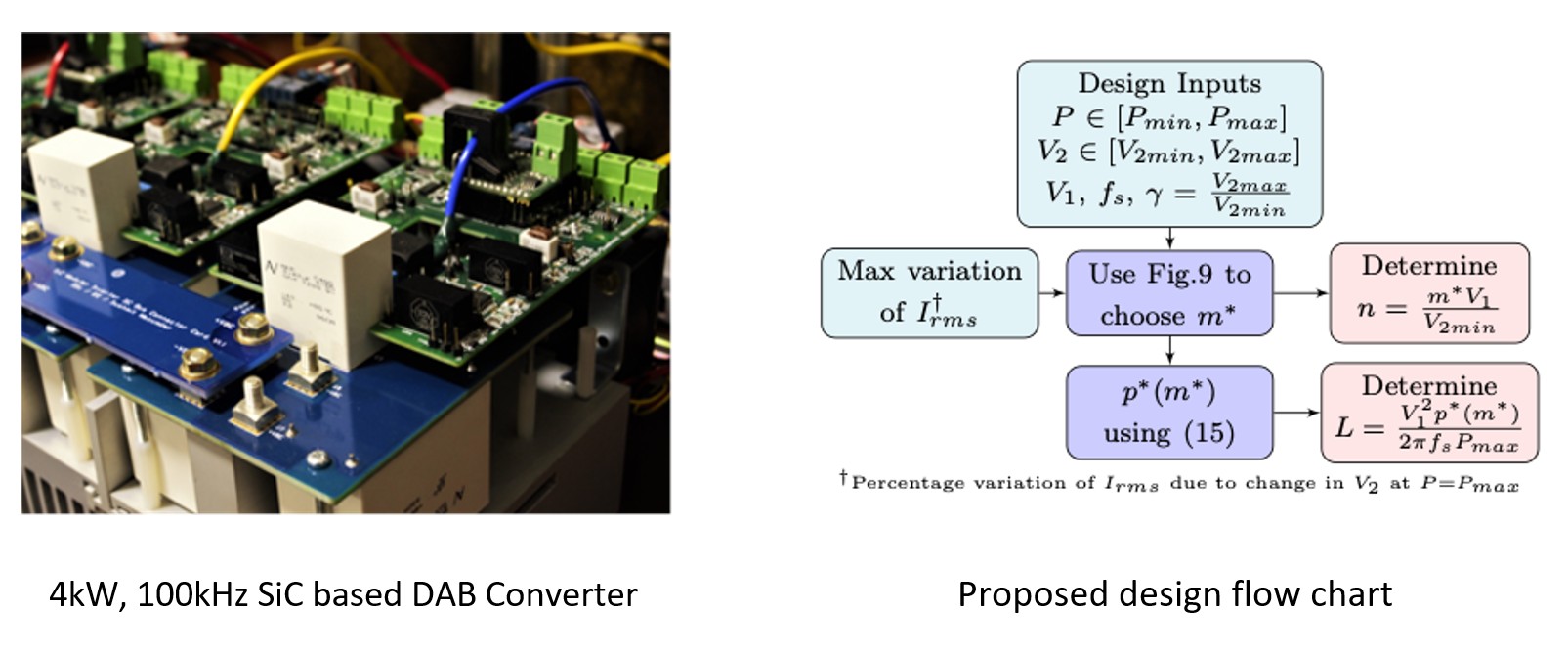
Optimal Design and Control of Dual Active Bridge DC-DC Converters
Dual active bridge isolated DC-DC converters are now widely used...
read more...
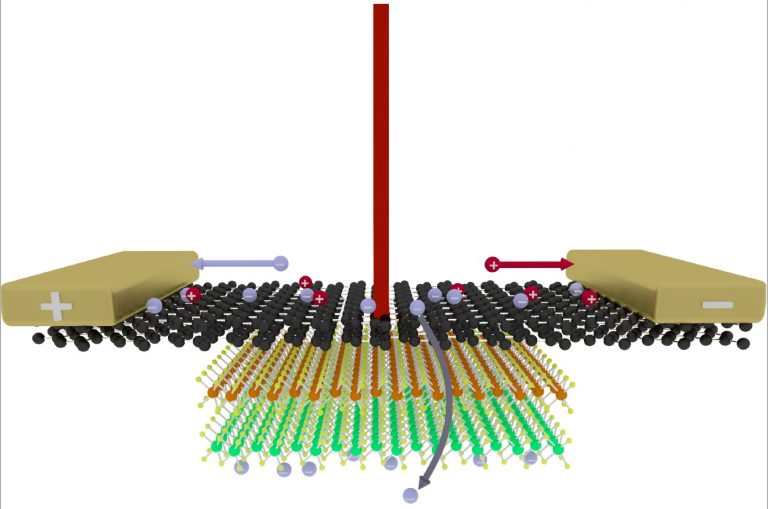
Ultrafast Charge and Energy Transfer Across van der Waals Heterojunctions
Two-dimensional layered semiconductors, for example, the monolayer transition metal dichalcogenides,...
read more...
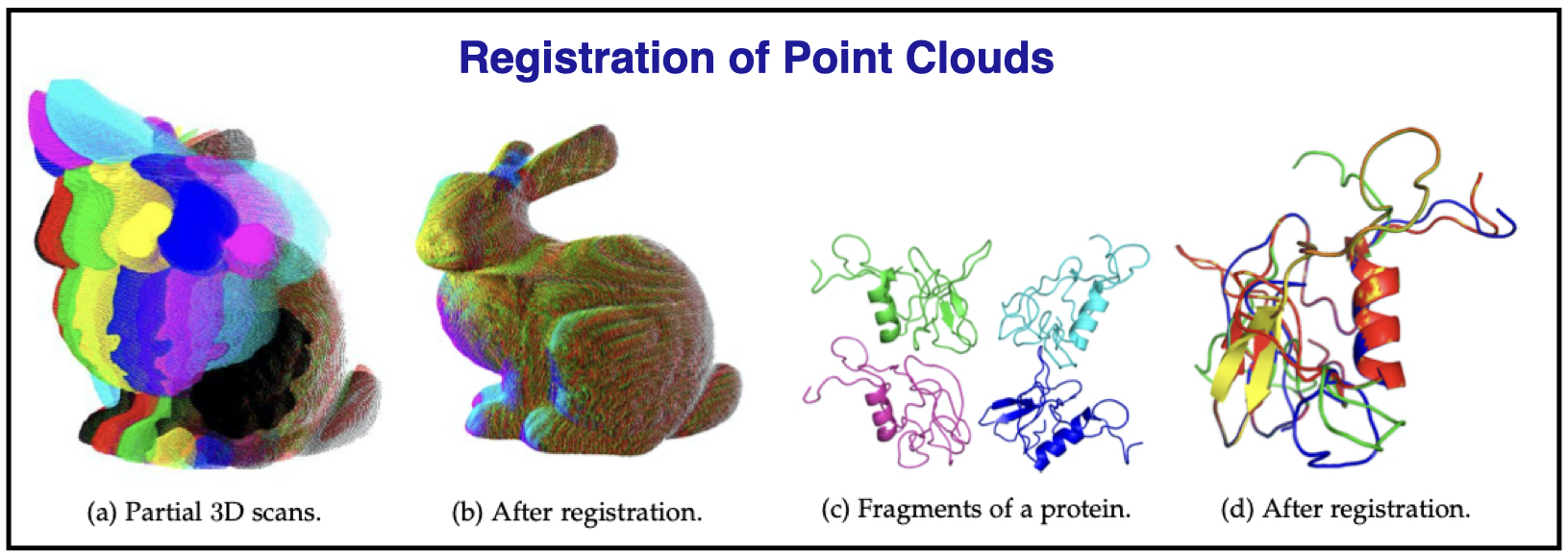
Uniqueness of rigid point-cloud registration
A necessary and sufficient condition for uniquely registering a system...
read more...
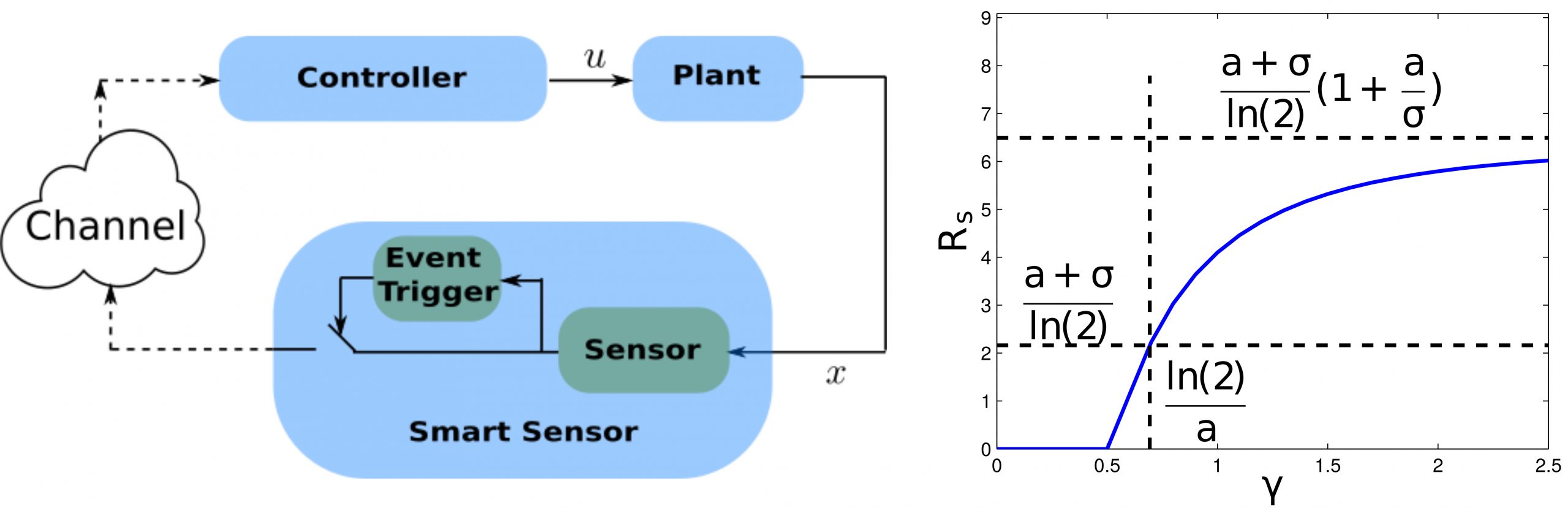
The value of timing information in event-triggered control
This work demonstrates that in event-triggered control, the timing of...
read more...
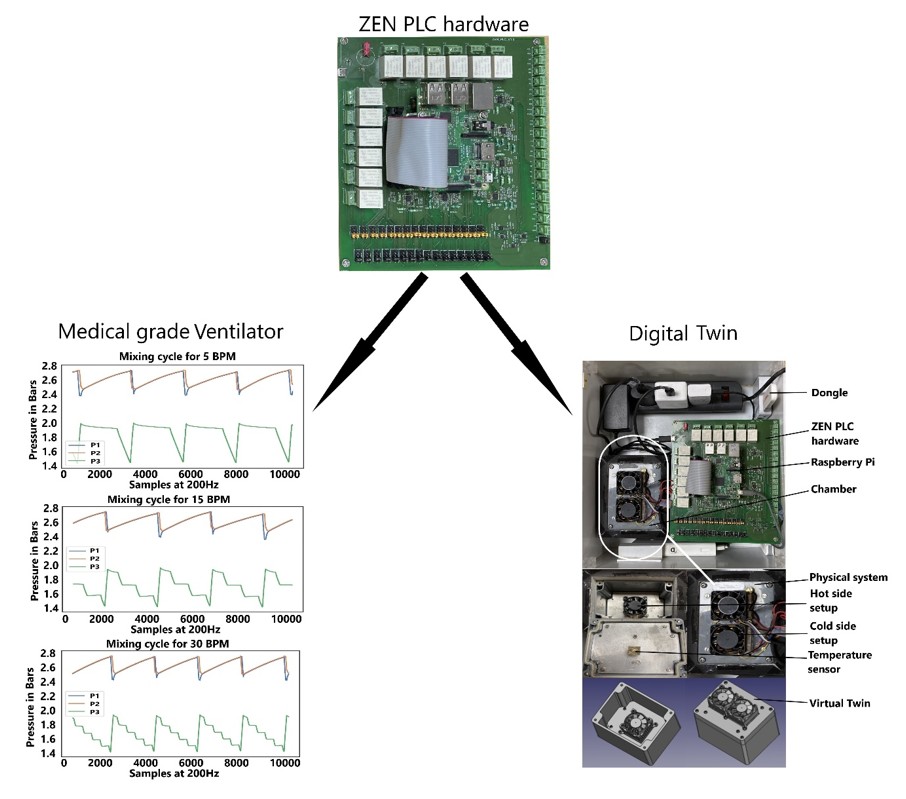
Next generation Programmable Logic Controller (PLC) platform hardware
Zero Energy Networks (ZEN) laboratory has designed and developed a...
read more...
Phonon limited anisotropic quantum transport in phosphorene field effect transistors
We develop a computer code, which elucidates the intricate electron-phonon coupling...
read more...
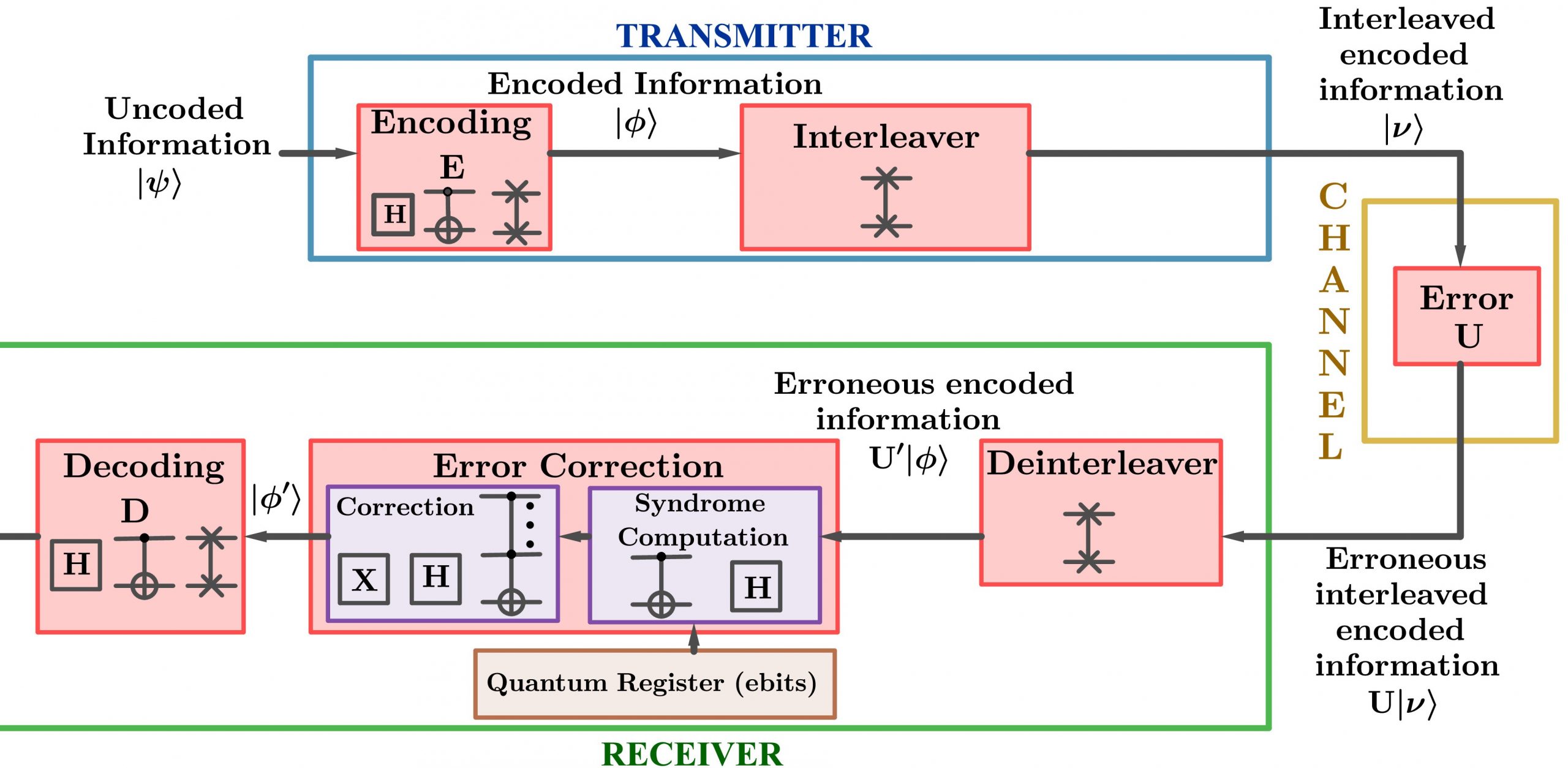
Coding Analog of Superadditivity using Quantum Tensor Product Codes
Researchers at PNSI lab led by Prof. Garani are actively...
read more...
Rate-optimal Coded Quantum Networks
Rate-optimal Coded Quantum Networks, Eavesdropping and more: We encode k...
read more...
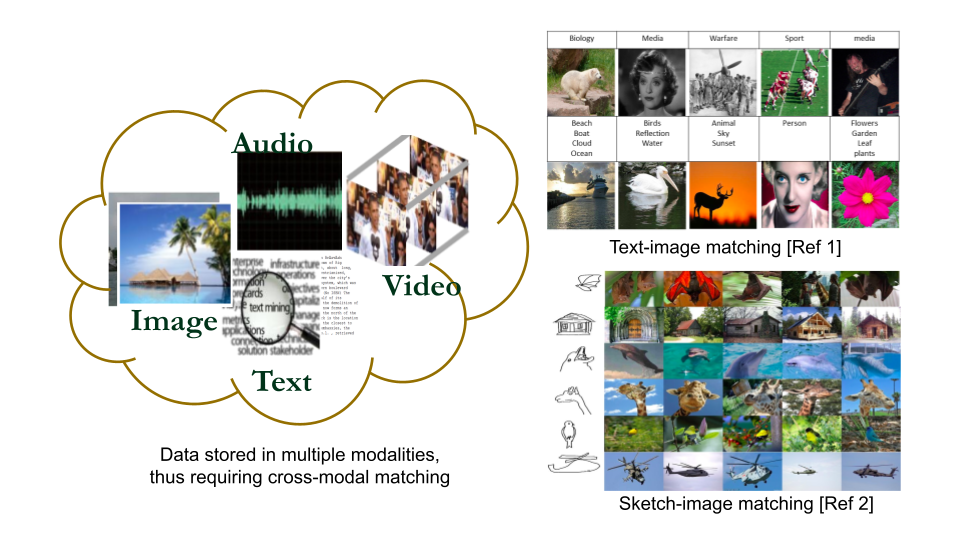
Semi-Supervised Cross-Modal Retrieval With Label Prediction
Cross-modal retrieval with image-text, sketch-image, etc. are gaining increasing importance...
read more...
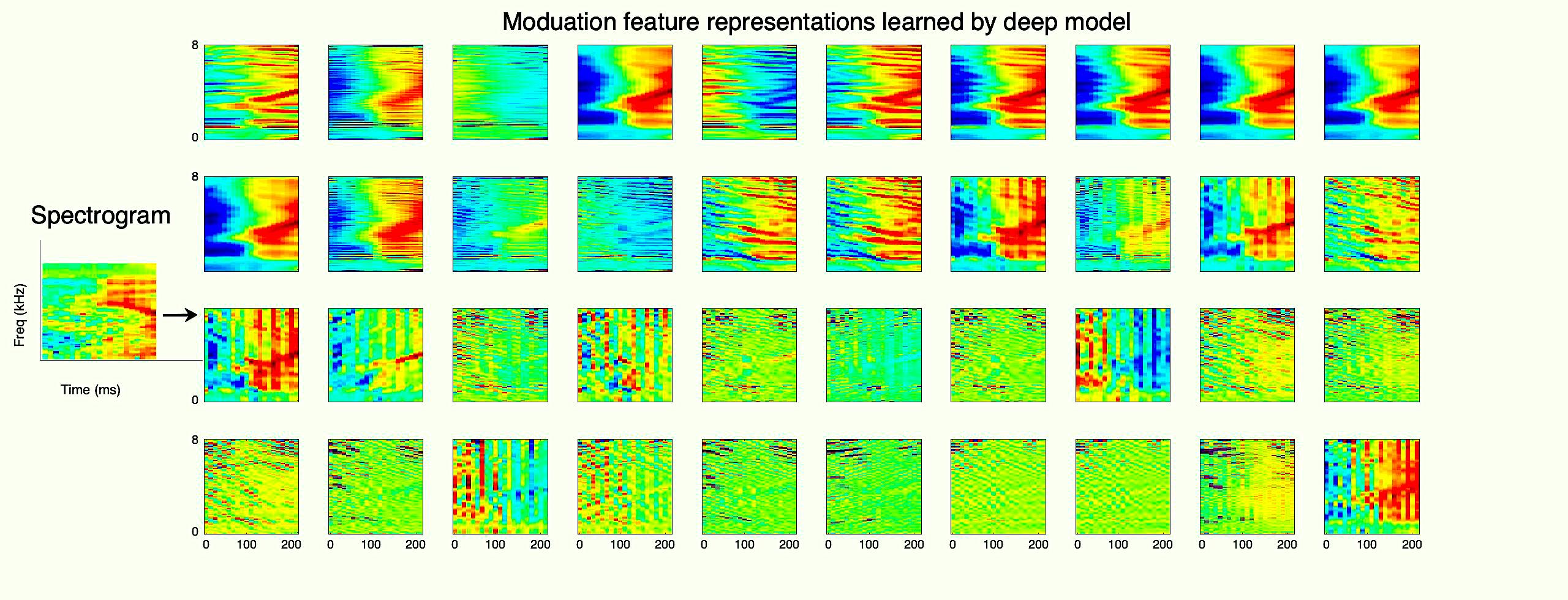
Deep Unsupervised Speech Representation Learning
The performance of speech systems is degraded in the presence...
read more...
Open-source modular and reusable compiler infrastructure for MLAI computations
The highlight has been the creation of an open-source modular...
read more...
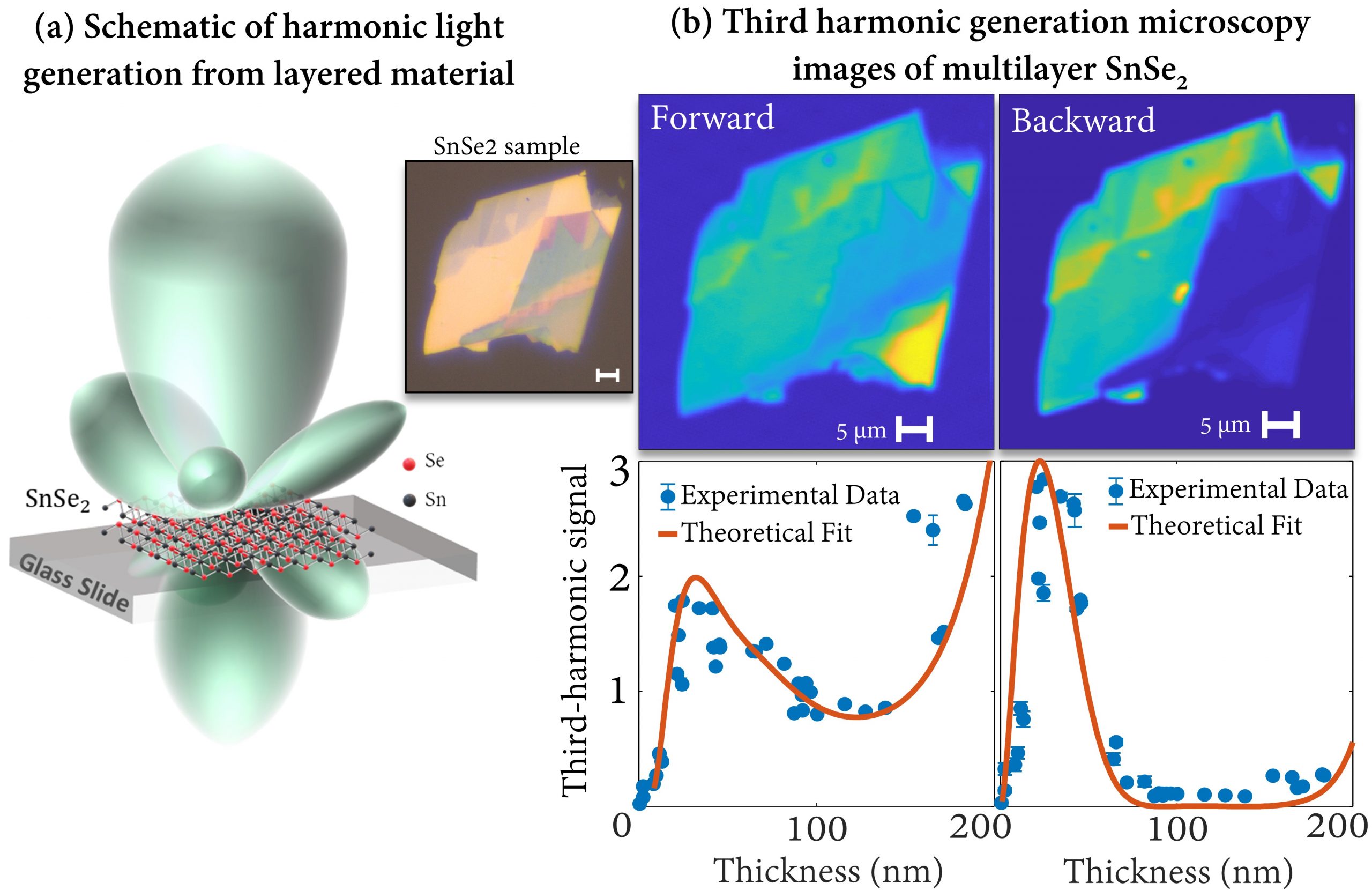
Nonlinear optics with emerging two-dimensional materials
Nonlinear optical study of emerging two-dimensional (2D) materials is interesting...
read more...
Streaming Codes for Low-Latency Communication
Ensuring reliable communication with low latency, is key to next-generation...
read more...
Privaros: A framework for privacy-compliant delivery drones
E-commerce companies are poised to use delivery drones to revolutionize...
read more...
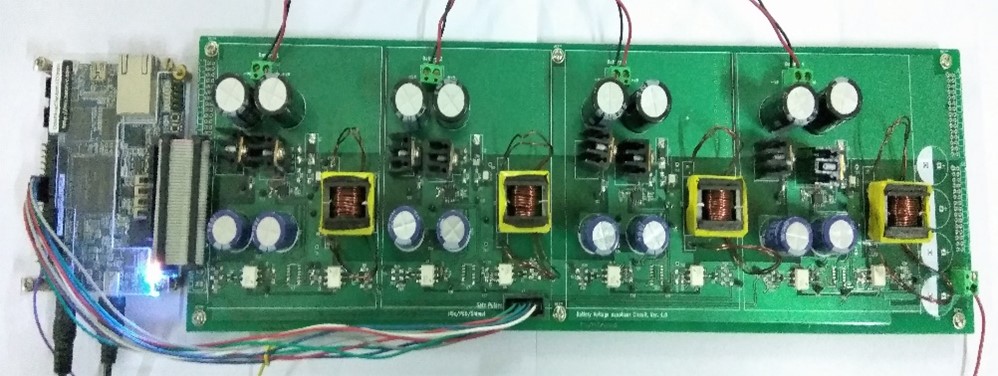
Voltage Equalizer for Electrochemical Energy Storages
A voltage equalizer ensures uniform voltage distribution in a series-connected...
read more...
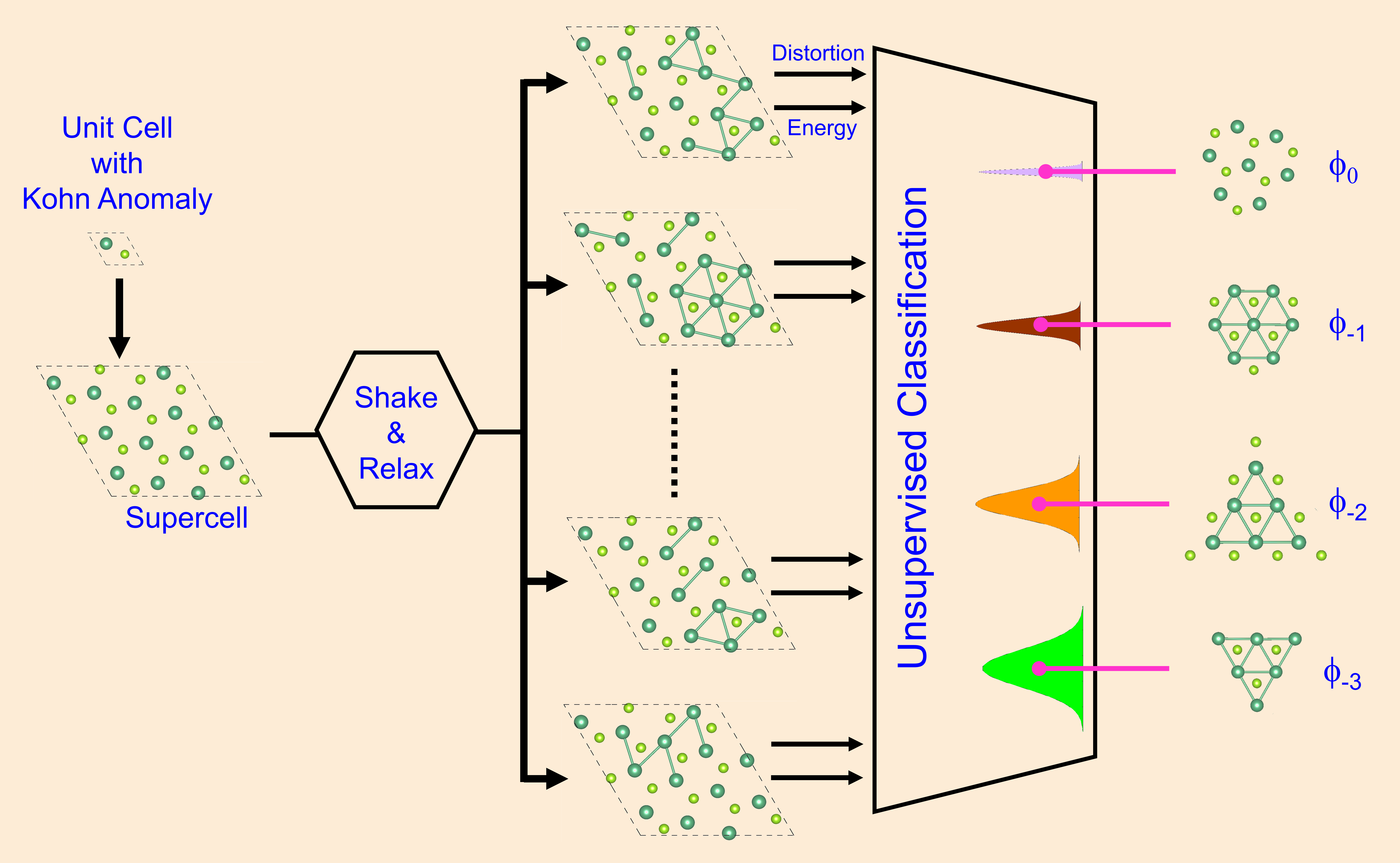
Can a Machine Learn Charge Density Waves?
Charge density wave (CDW) is a quantum mechanical phenomenon, which...
read more...
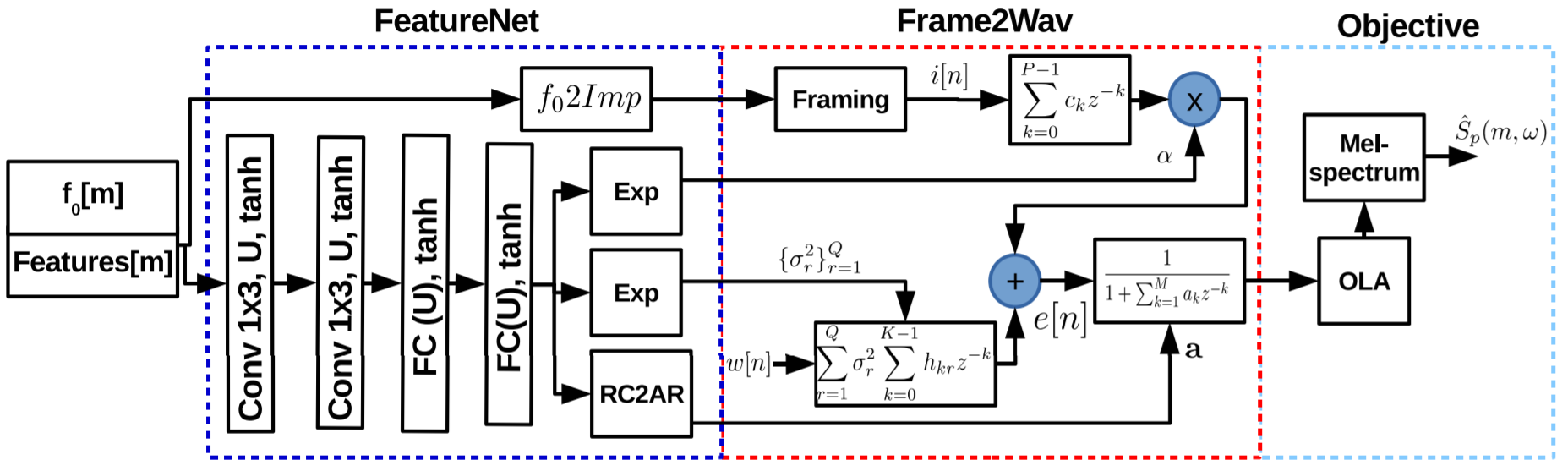
SFNet: A Computationally Efficient Source Filter Model Based Neural Speech Synthesis
A reduced-complexity speech synthesizer is developed by reformulating the source-filter...
read more...
Fast Local Page-Tables for Virtualized NUMA Servers with vMitosis
Increasing memory heterogeneity mandates careful data placement to hide the non-uniform...
read more...
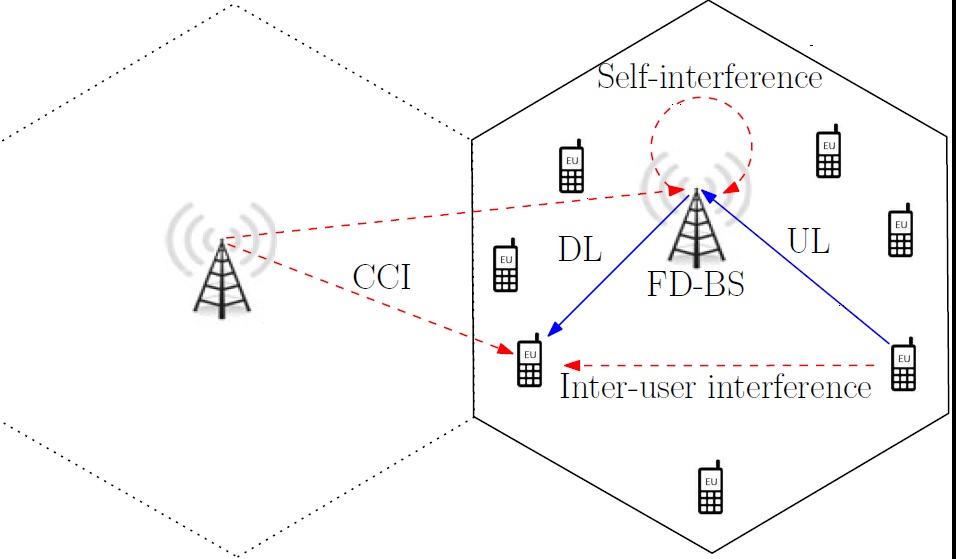
Resource Allocation with Reduced Feedback and Distributed Multiple Access in Full-Duplex Cellular and WiFi Systems
Full-duplex promises to double the data rates by enabling simultaneous...
read more...
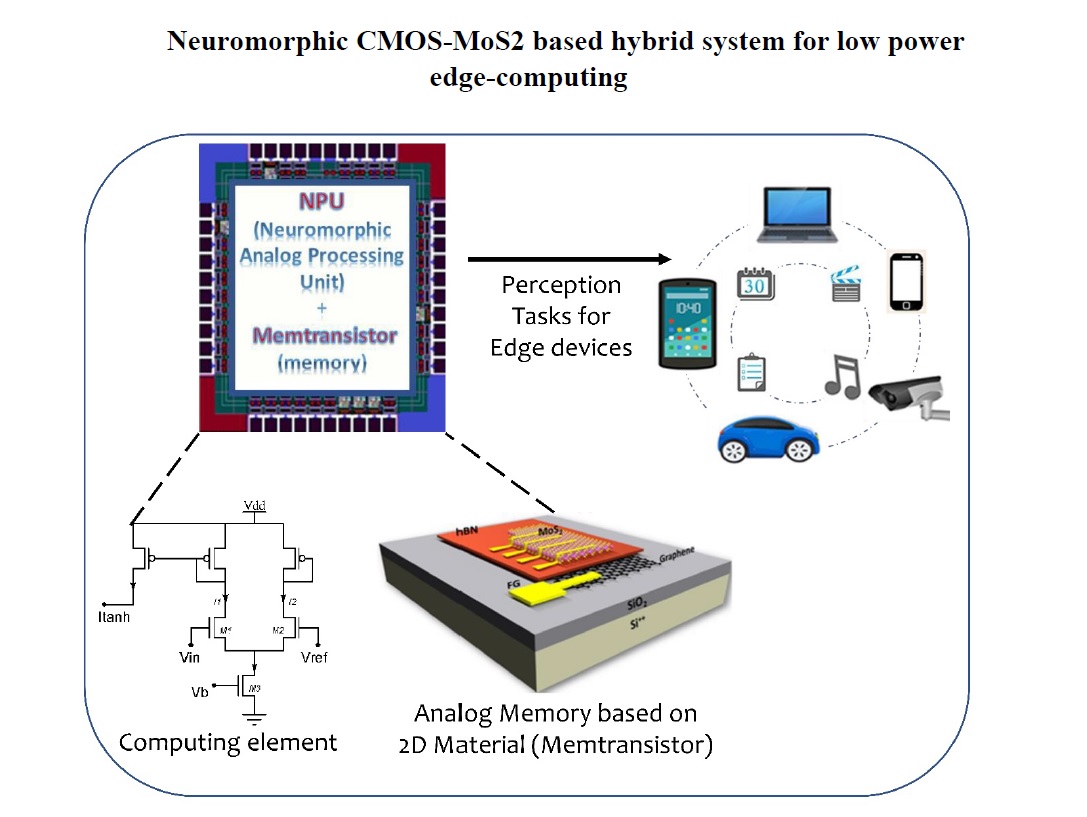
Neuromorphic CMOS-MoS2 based hybrid system for low power edge-computing
The brain is an ideal template for next-generation computing architectures....
read more...
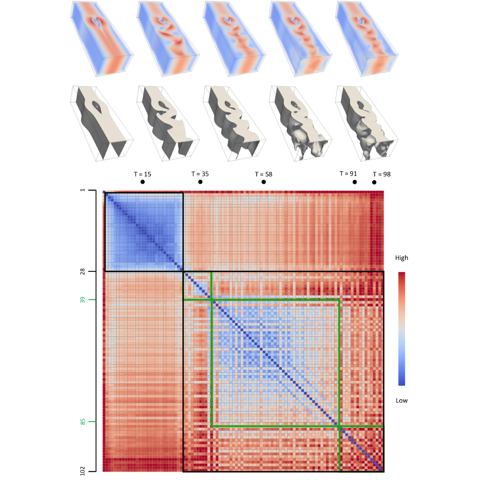
Edit Distance between Merge Trees
Physical phenomena are often modeled as scalar functions. A merge...
read more...
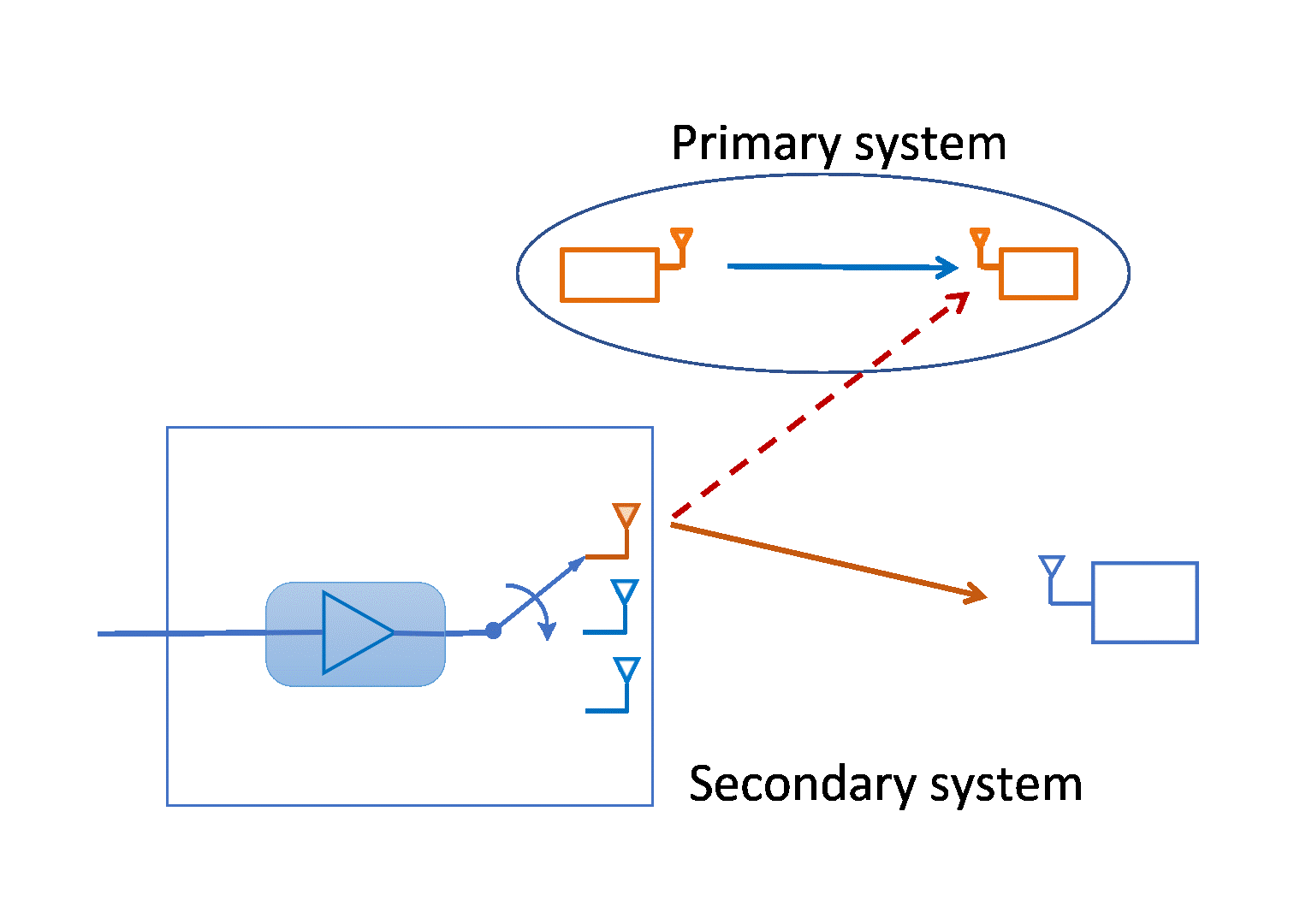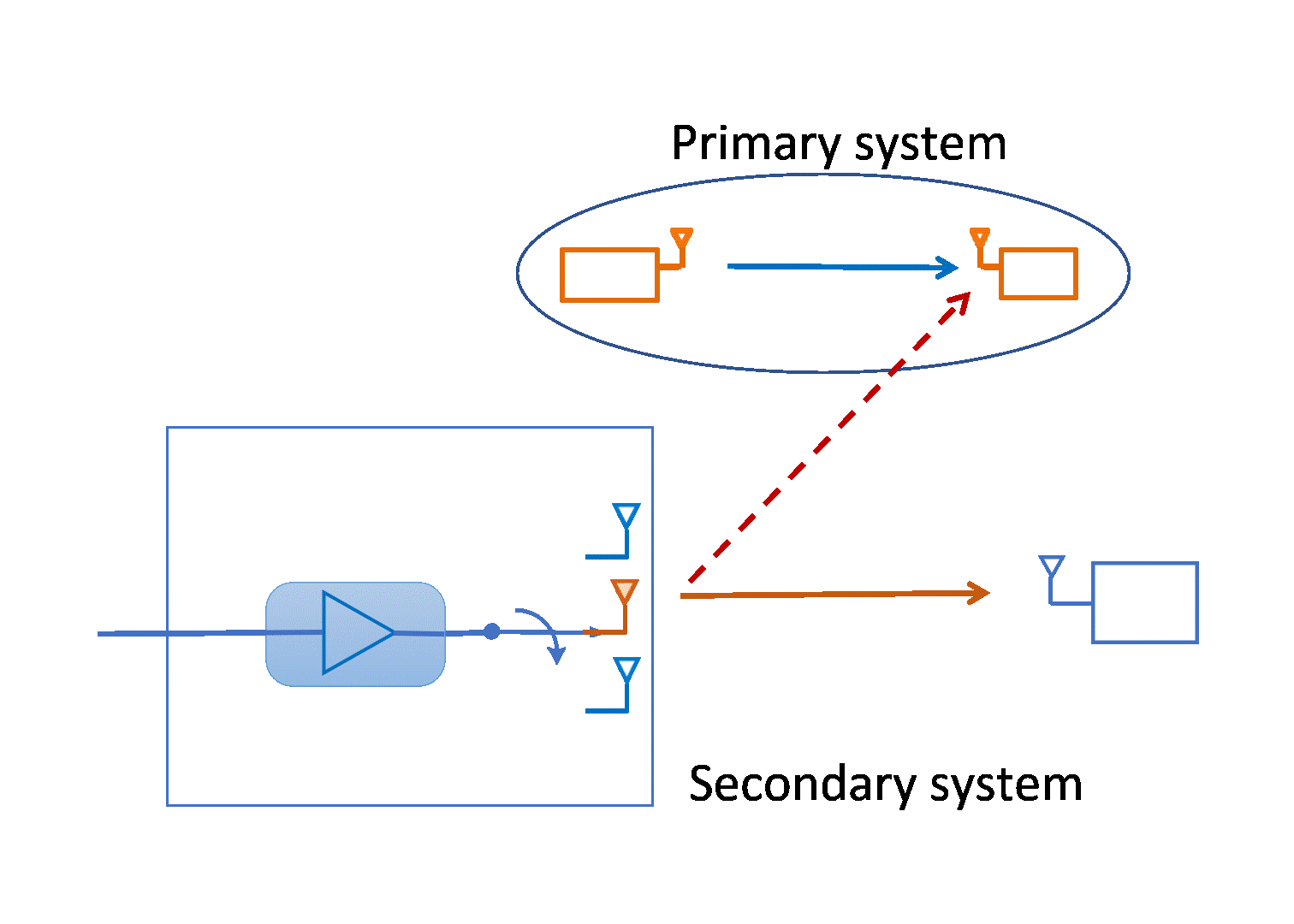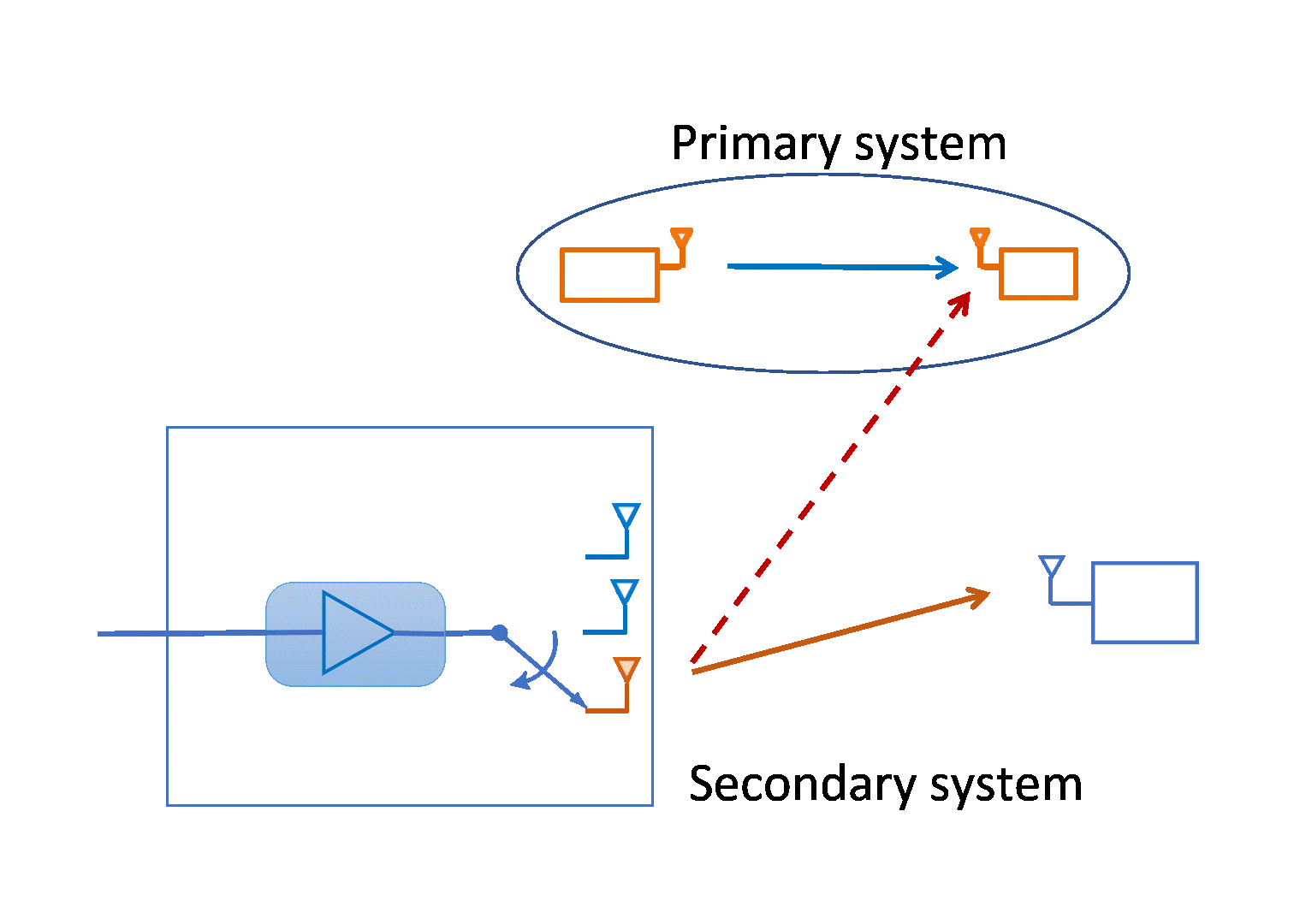
Optimal Transmit Antenna Selection in Underlay Spectrum Sharing
Spectrum sharing is essential to meet the ever-increasing demand of...
read more...
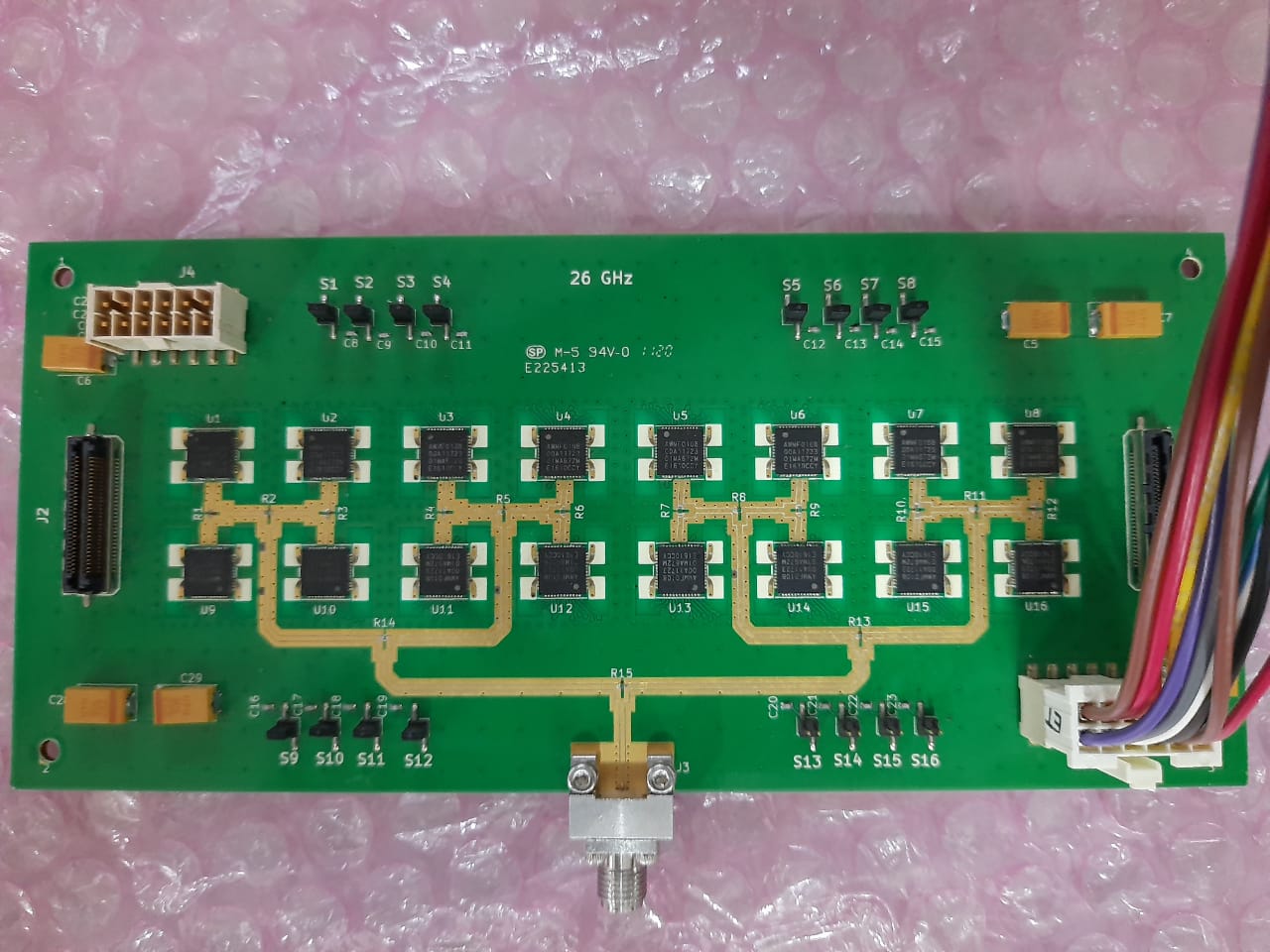
MM Wave 5G Beam steering Antenna Array
An active beam steering antenna array with 64 elements along...
read more...
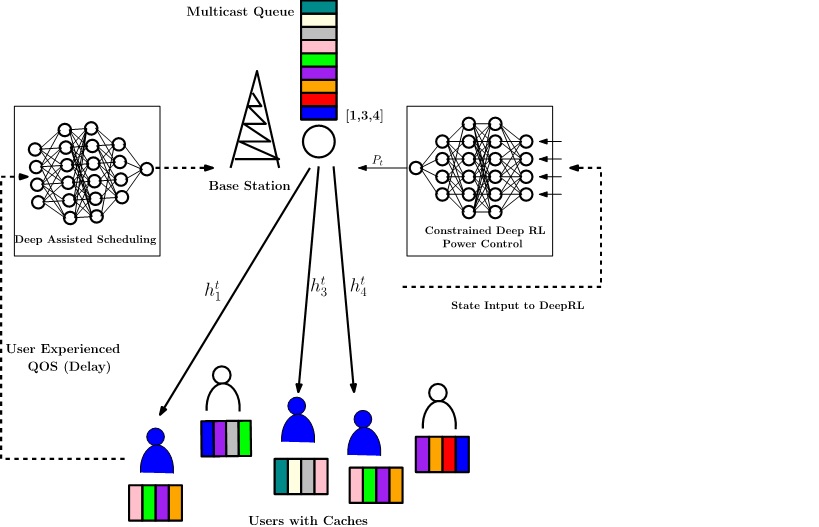
Combining queueing theory with deep reinforcement learning for scheduling and power control
We propose a novel Multicast queue for wireless content centric...
read more...
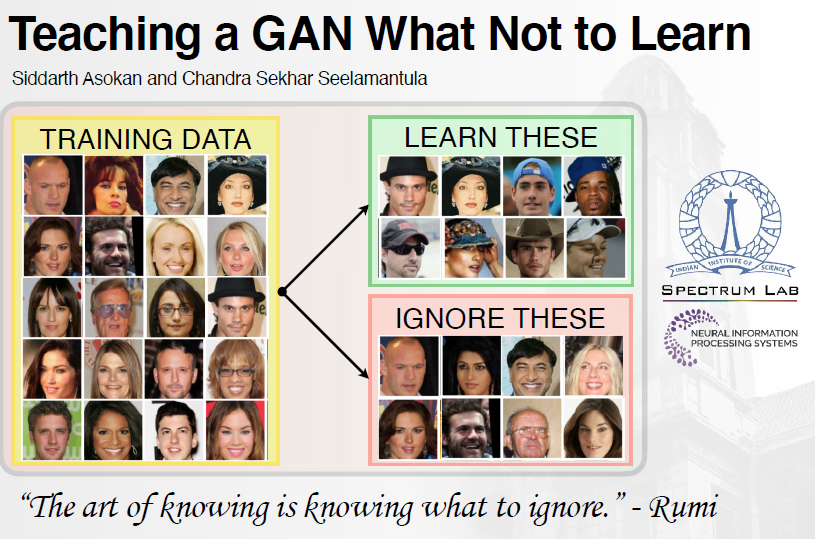
Teaching A GAN what not to learn
Semi-supervised generative adversarial networks (GANs) consist of neural networks tasked...
read more...
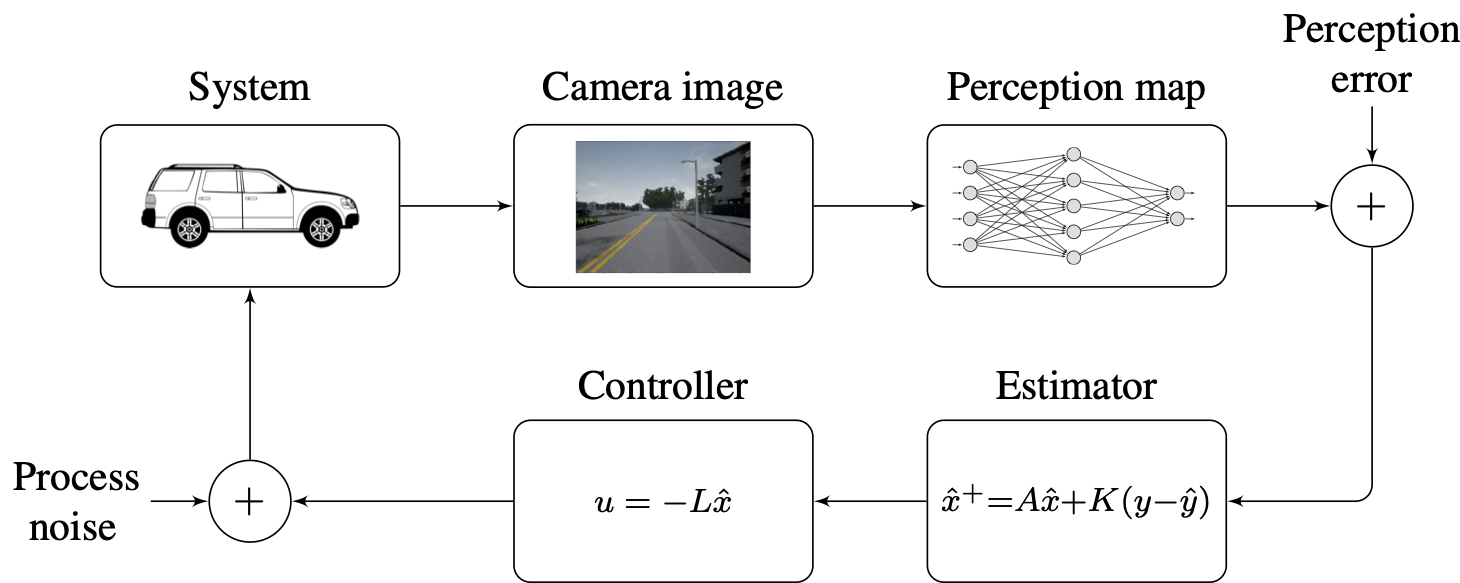
Accuracy-Robustness Trade-offs in Data-driven Control
Despite the widespread use of ML/data-driven algorithms, provable guarantees on...
read more...
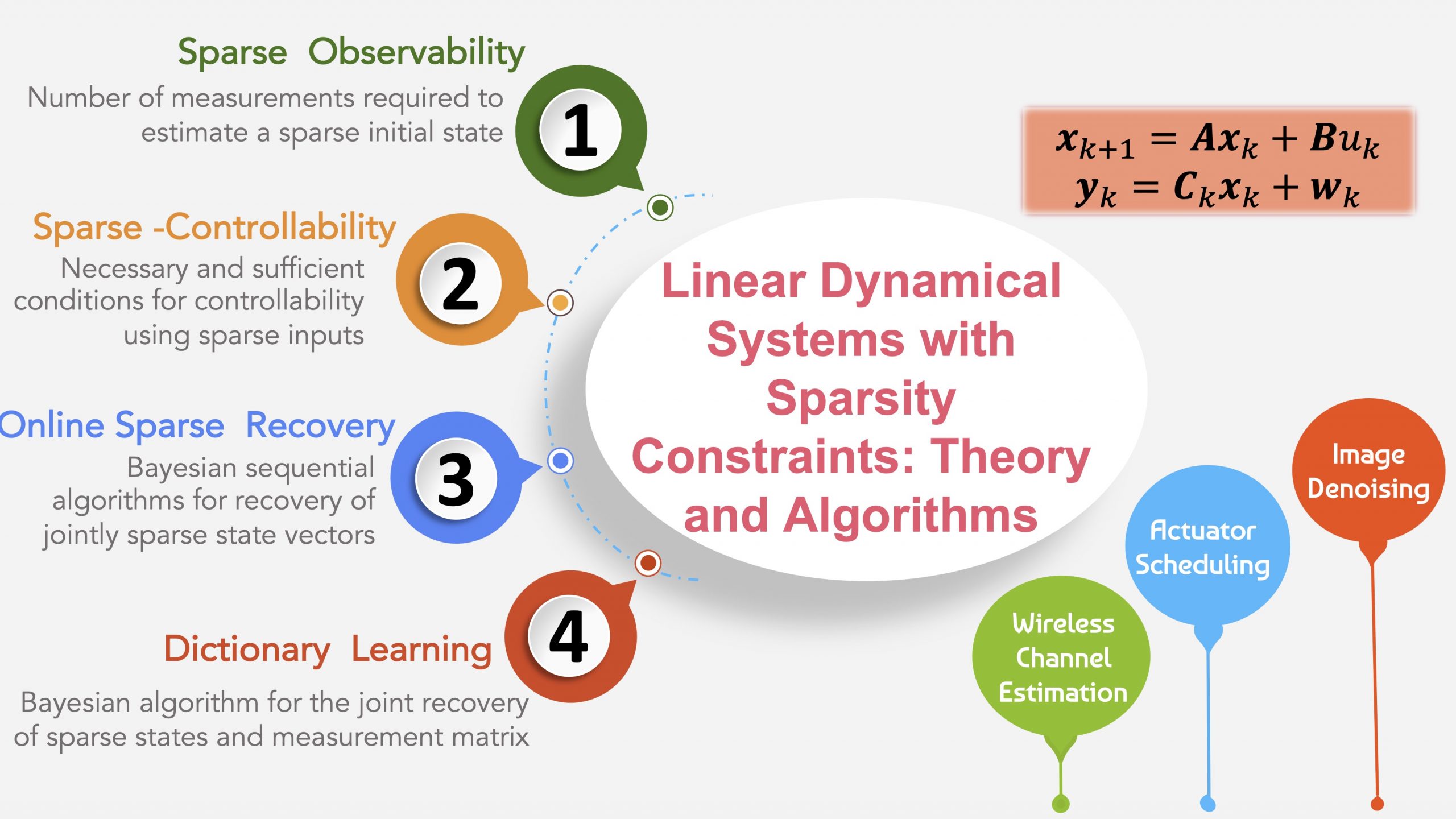
Linear Dynamical Systems with Sparsity Constraints
Consider a linear dynamical system with sparsity constraints on the...
read more...
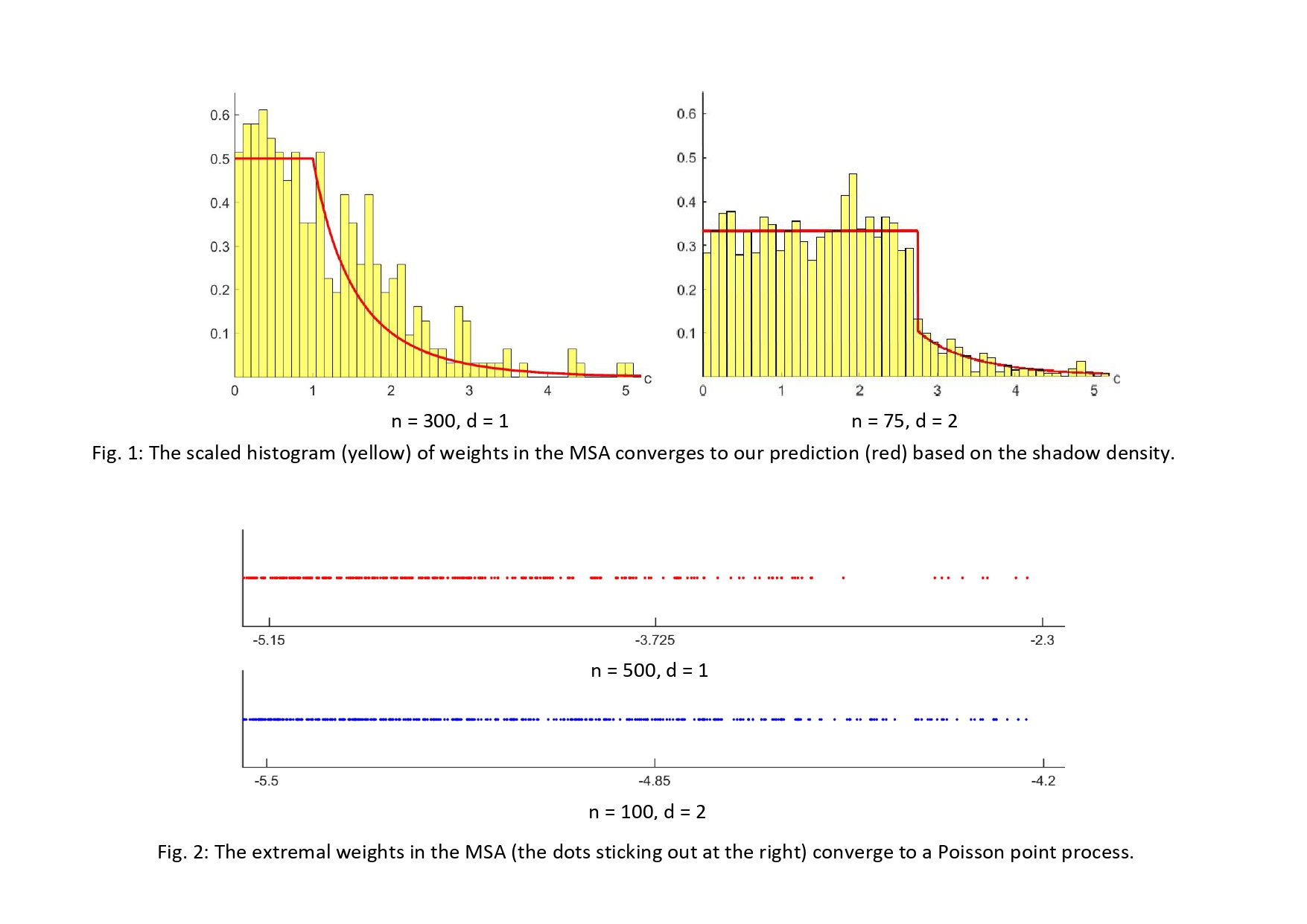
The Bulk and the Extremes of Minimal Spanning Acycles and Persistence Diagrams of Random Complexes
The expected weight of the Minimum Spanning Tree (MST) in...
read more...
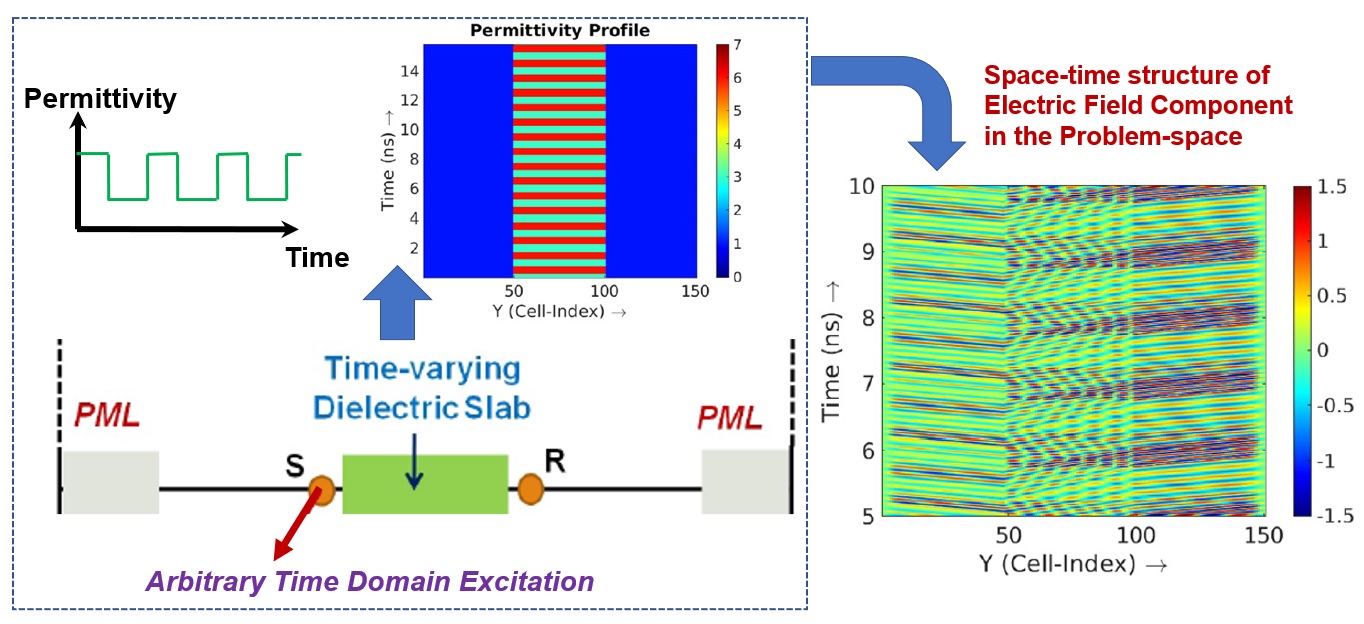
Interaction of Electromagnetic Wave with Dielectric Medium having Arbitrarily Time-modulated Permittivity: An FDTD Approach
The concept of time-varying media (temporal photonic crystals) is recently...
read more...
Reward Biased Maximum Likelihood Estimate Approach to Online Machine Learning
We revisit the Reward Biased Maximum Likelihood Estimate (RBMLE) algorithm...
read more...
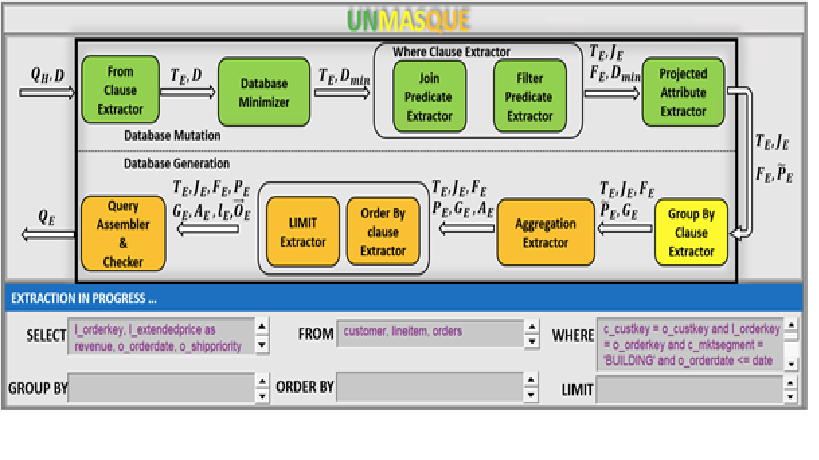
UNMASQUE: Shedding Light on Opaque Application Queries
We have defined a new reverse-engineering problem of unmasking SQL...
read more...
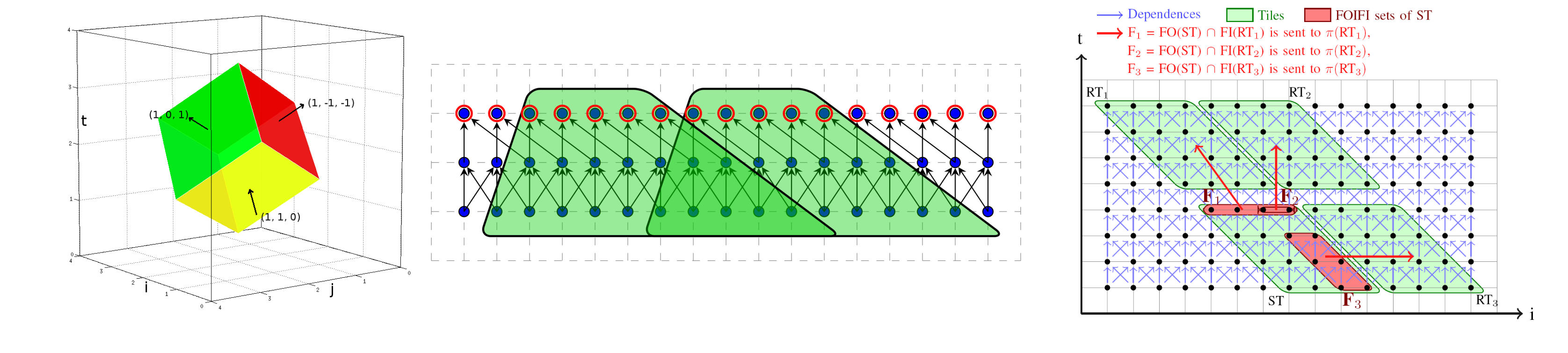
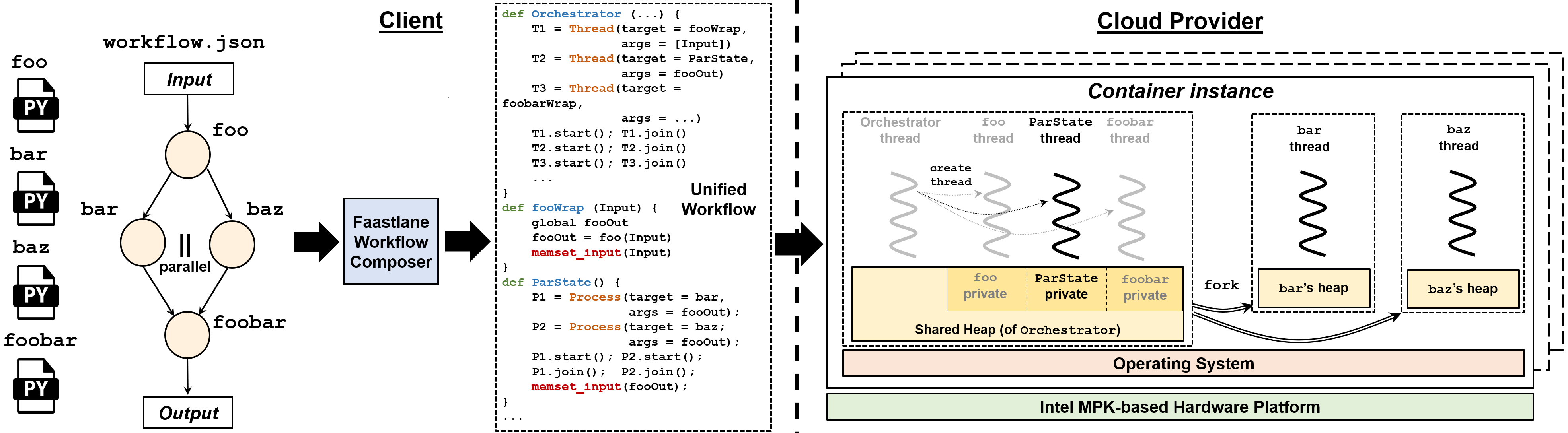
FaastLane: Accelerating Function-as-a-Service Workflows
Function-as-a-service (FaaS) workflows implement application logic by interacting and exchanging...
read more...
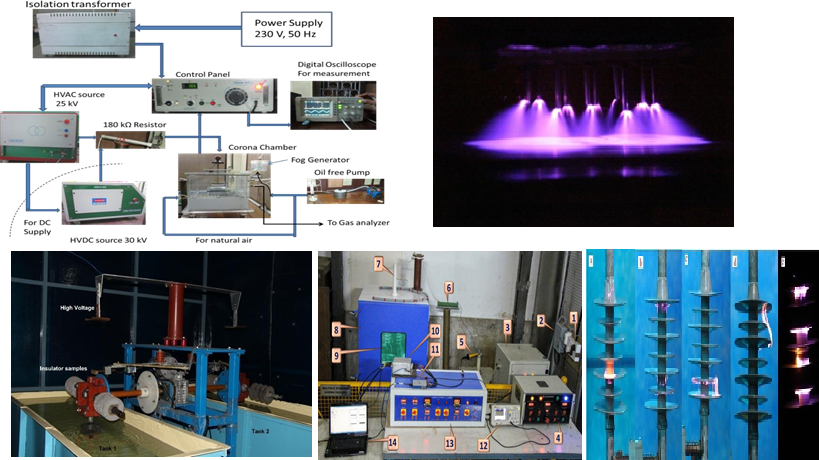
Accelerated Aging Studies on HVAC & HVDC Composite Insulators
Accelerated aging studies are performed to study the estimated and...
read more...
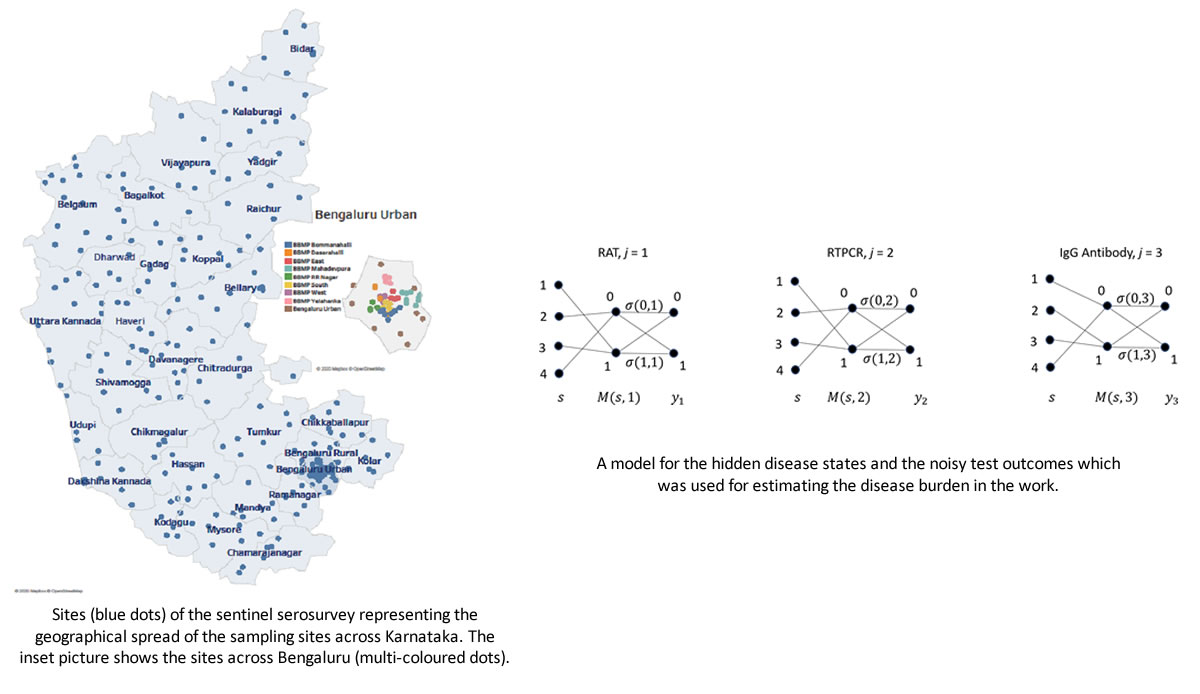
Estimating the COVID-19 burden in Karnataka
This work, a Karnataka-wide COVID-19 serological survey, provided a wealth...
read more...
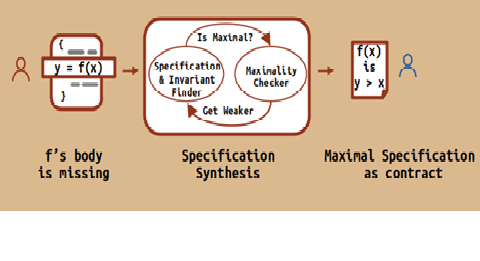
Giving your co-programmer maximum leeway
Programs are ubiquitous, be it the browser you are using...
read more...
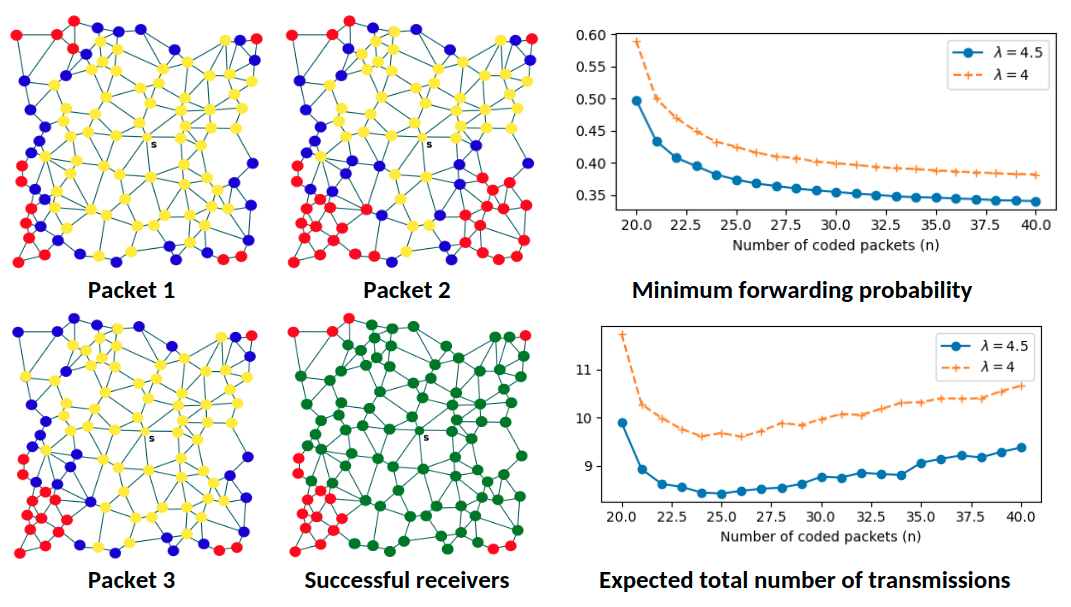
Information dissemination on ad-hoc networks
Probabilistic forwarding along with coding, as a broadcast mechanism for...
read more...
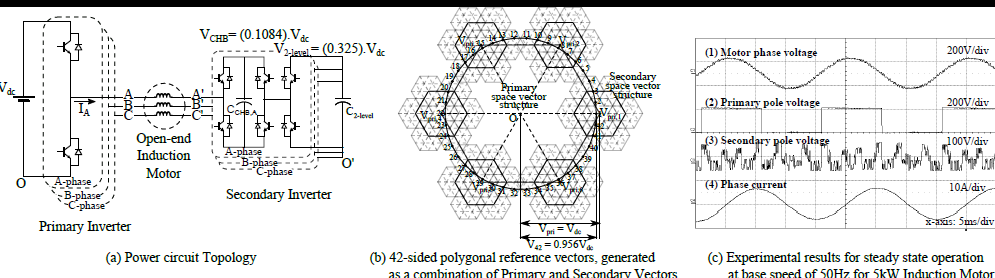
Suppression of lower order harmonics for a 42-sided voltage space vector structure
The research work proposes an inverter topology for the first...
read more...
Development of Microneedles for Painless Drug Delivery
The enormous potential offered by transdermal drug delivery can be...
read more...
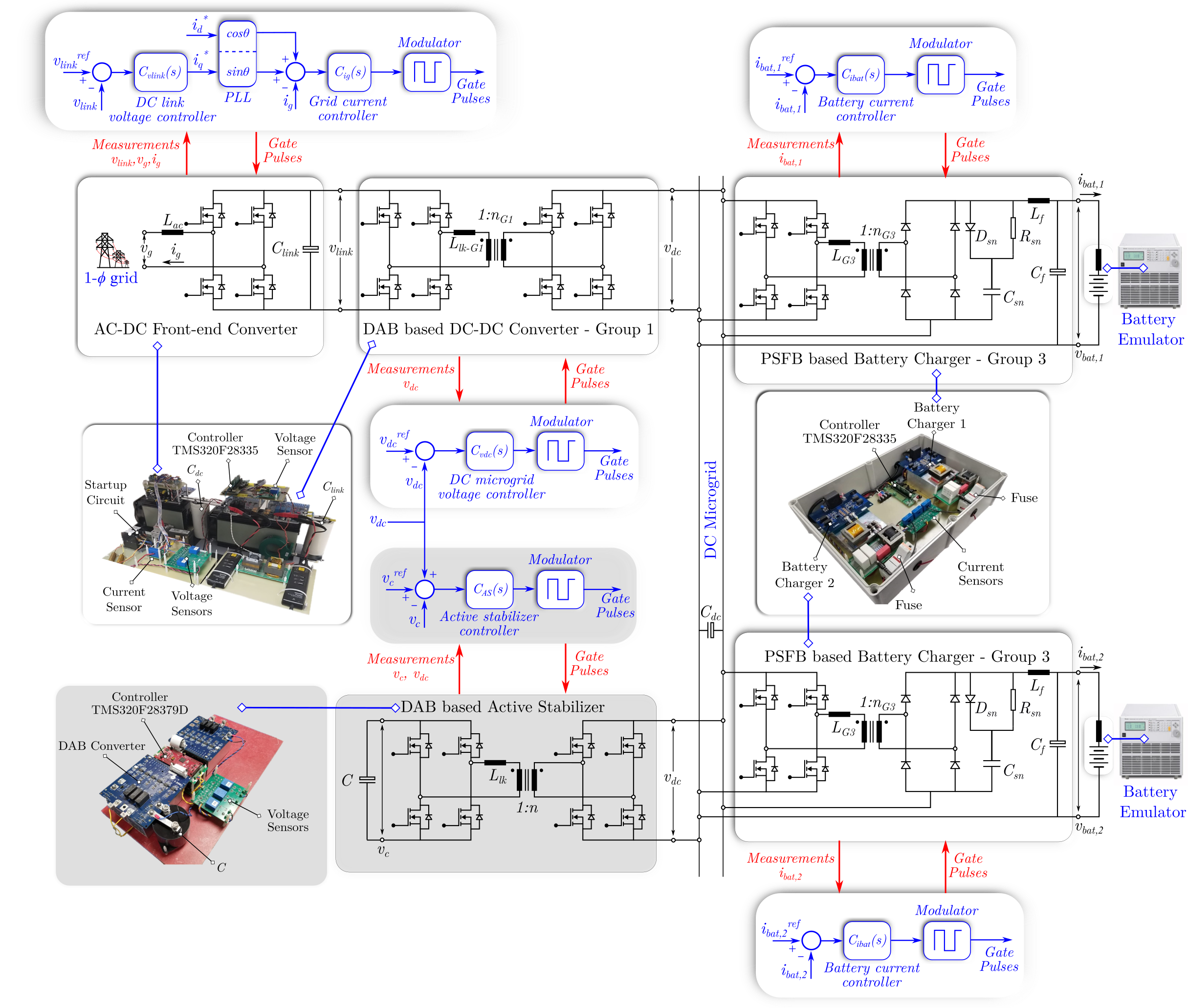
An Active Voltage Stabilizer for a DC Microgrid System
DC microgrids (MG) are becoming popular as they offer several...
read more...
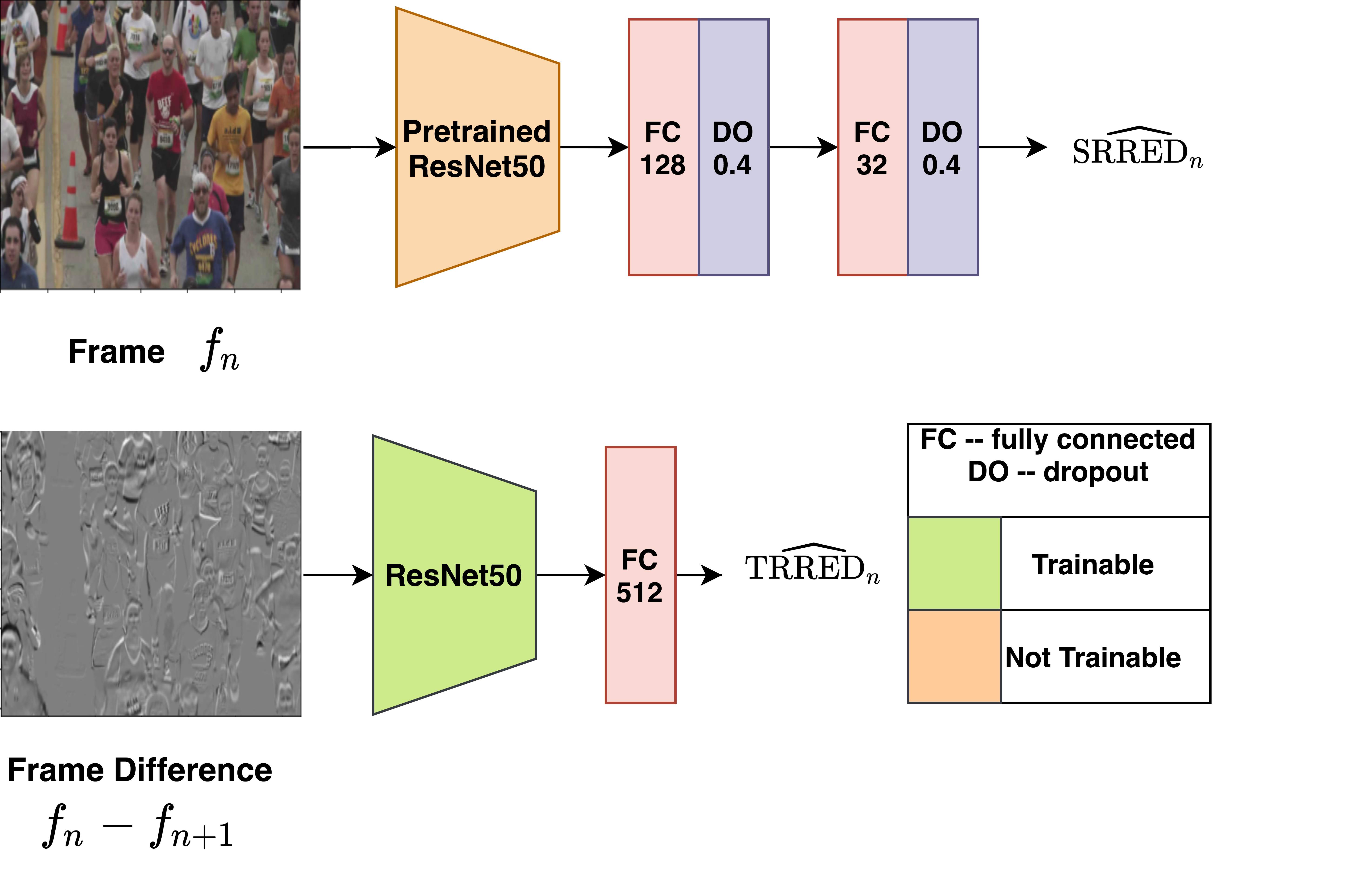
No reference video quality assessment
We consider the problem of robust no reference (NR) video...
read more...
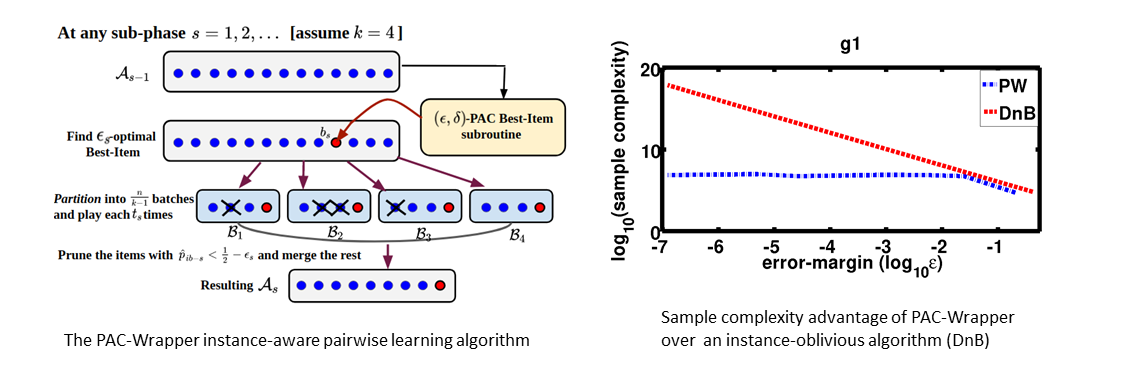
Ballooning Multi-Armed Bandits
Online platforms such as Q&A forums (e.g. StackExchange, Reddit) receive...
read more...
Machine Learning with Comparisons
Together with graduate student Aadirupa Saha at IISc, Aditya Gopalan’s...
read more...
Robust Quadrupedal Locomotion
In this work, with a view toward fast deployment of...
read more...
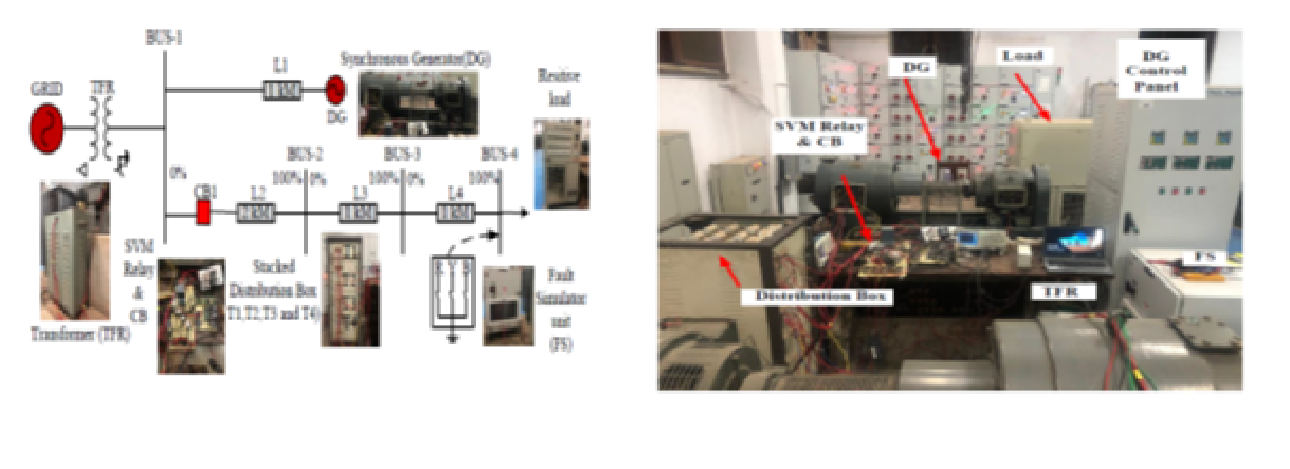
Multiclass- SVM Relay for Microgrid Protection
Our approach to microgrid protection in this paper uses a...
read more...
Transient Vector Estimator based Control Scheme for EVs
The drive control schemes for electric vehicles can be classified...
read more...
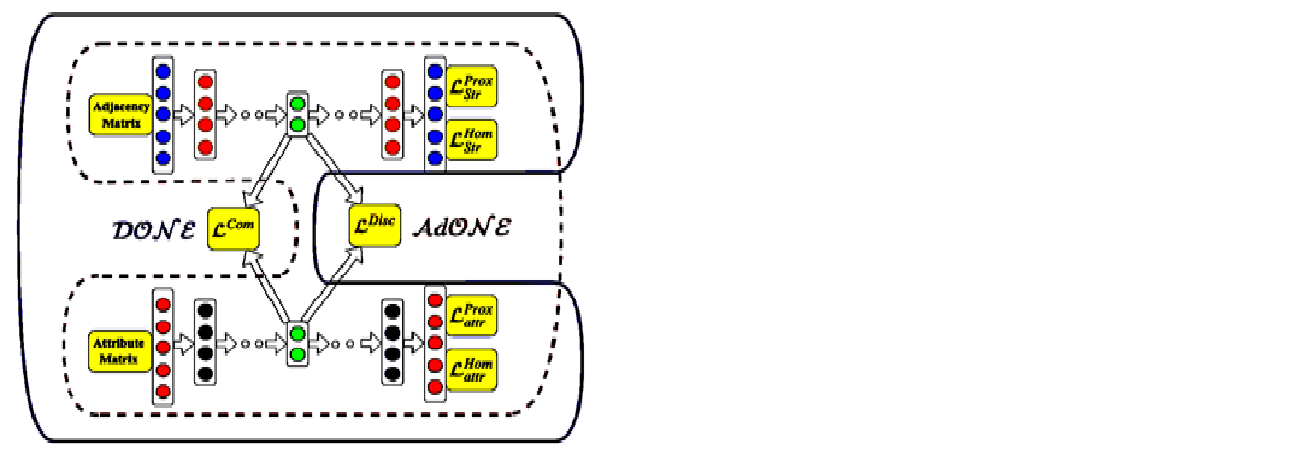
Unsupervised Deep Architectures for Attributed Network Embedding
Outliers can have an adverse effect on the embeddings of...
read more...
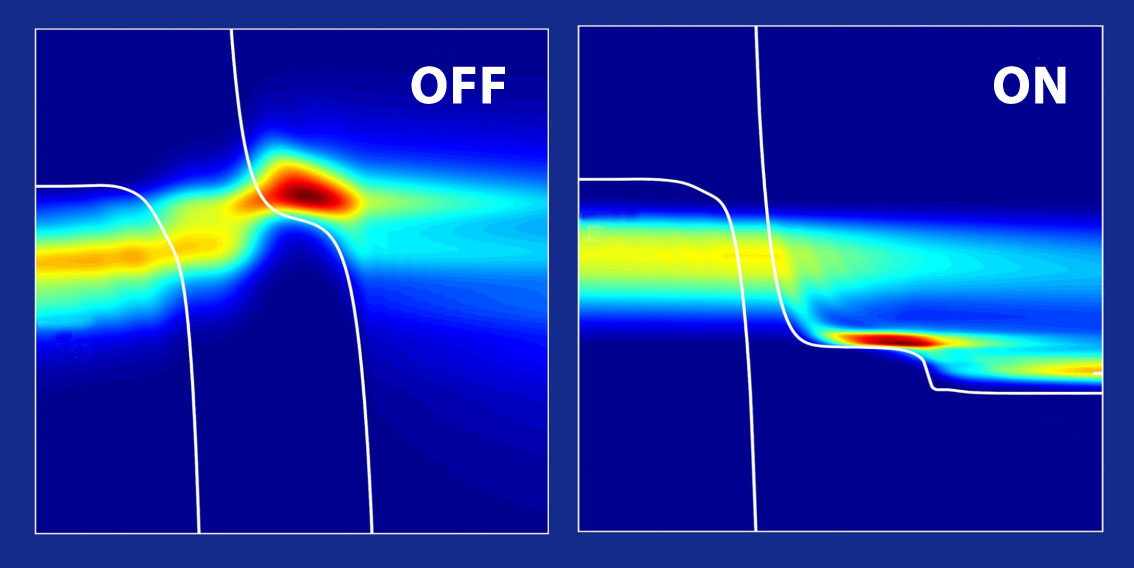
SiC Based Power Converter for High-Speed Switched Reluctance Machine
This work is motivated by the requirement of a high-speed...
read more...
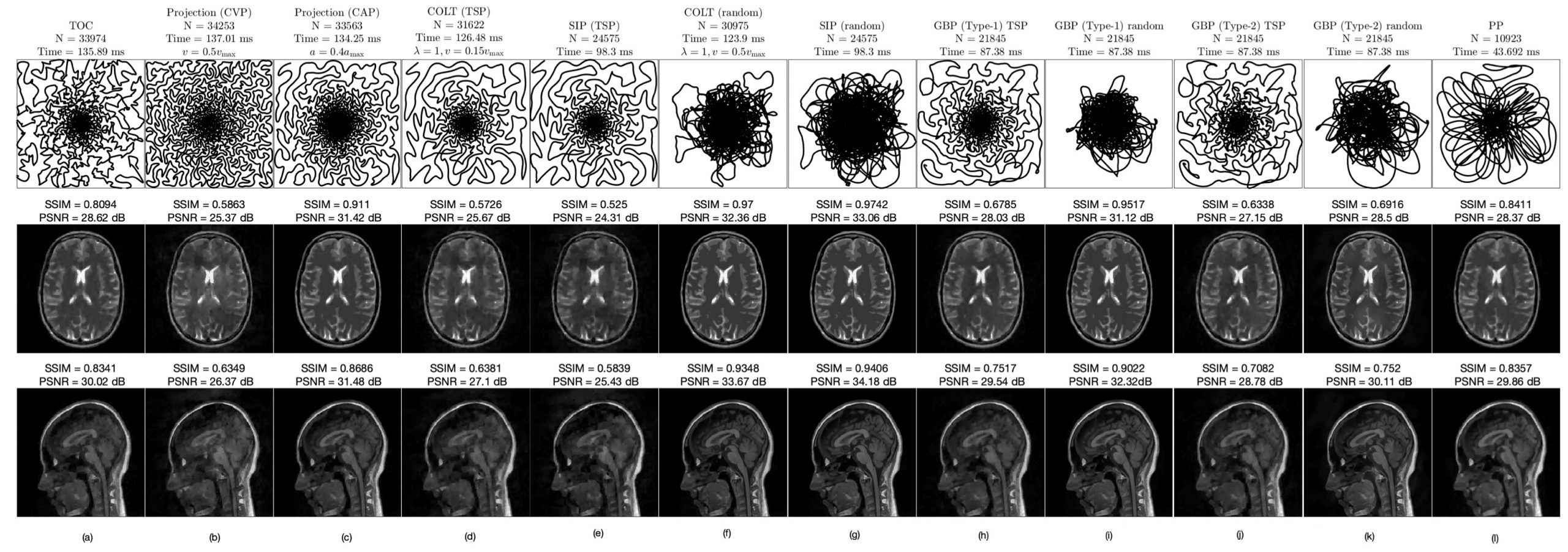
A generalized framework for projection-based methods for sampling in MRI systems
MRI collects samples in the Fourier domain, called as the...
read more...
Instructing Robots through gestures, text and speech
We are exploring the use of gestures and natural language...
read more...
Questions Related to Anti-Ramsey Numbers
The anti-Ramsey number, ar(G, H) is the minimum integer k...
read more...
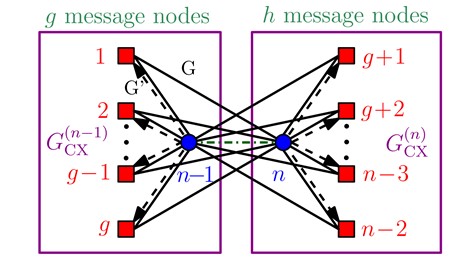
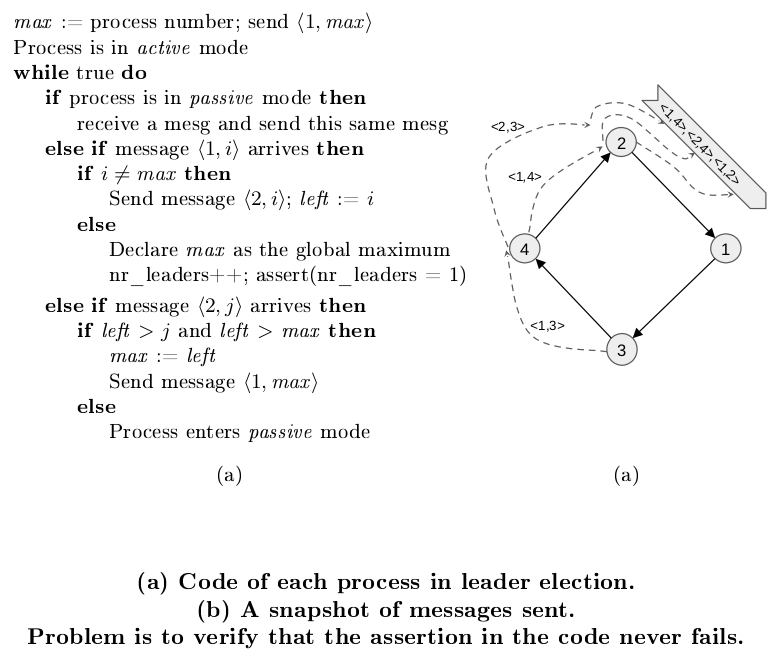
Functional verification of asynchronous systems and protocols
Asynchronous message-passing systems are employed frequently to implement distributed mechanisms,...
read more...
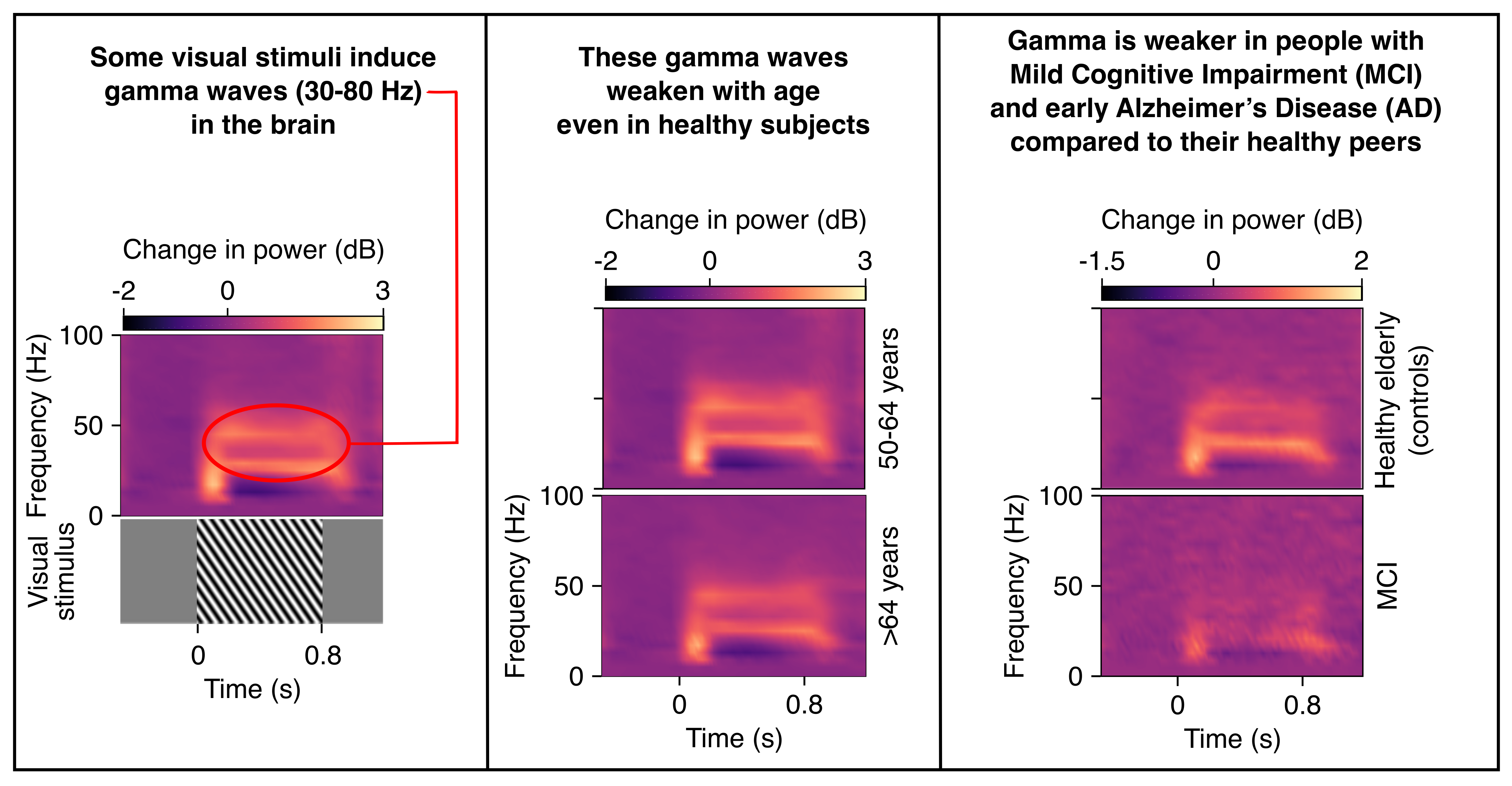
Gamma oscillations as a biomarker for early diagnosis of Alzheimer’s Disease (AD)
Electrical signals recorded from the brain often show fluctuations between...
read more...
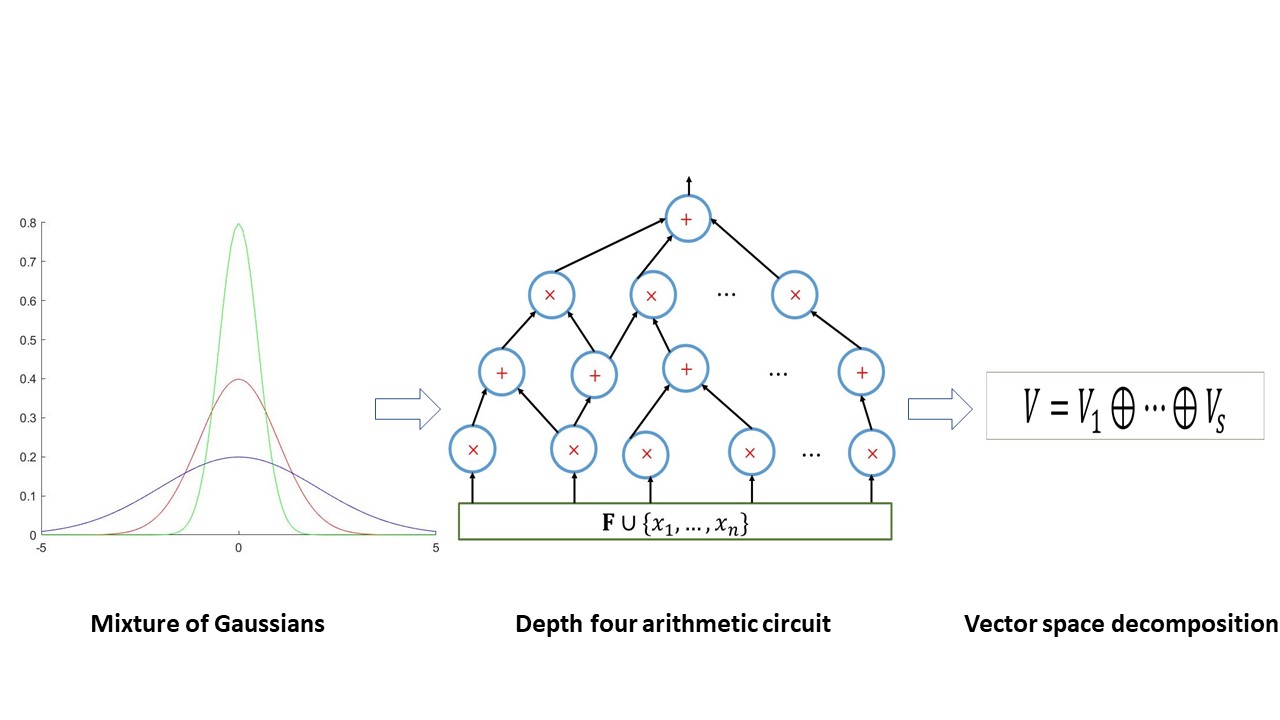
Learning Mixtures of Gaussians via Arithmetic Circuits
We give an efficient algorithm to solve the moment problem...
read more...
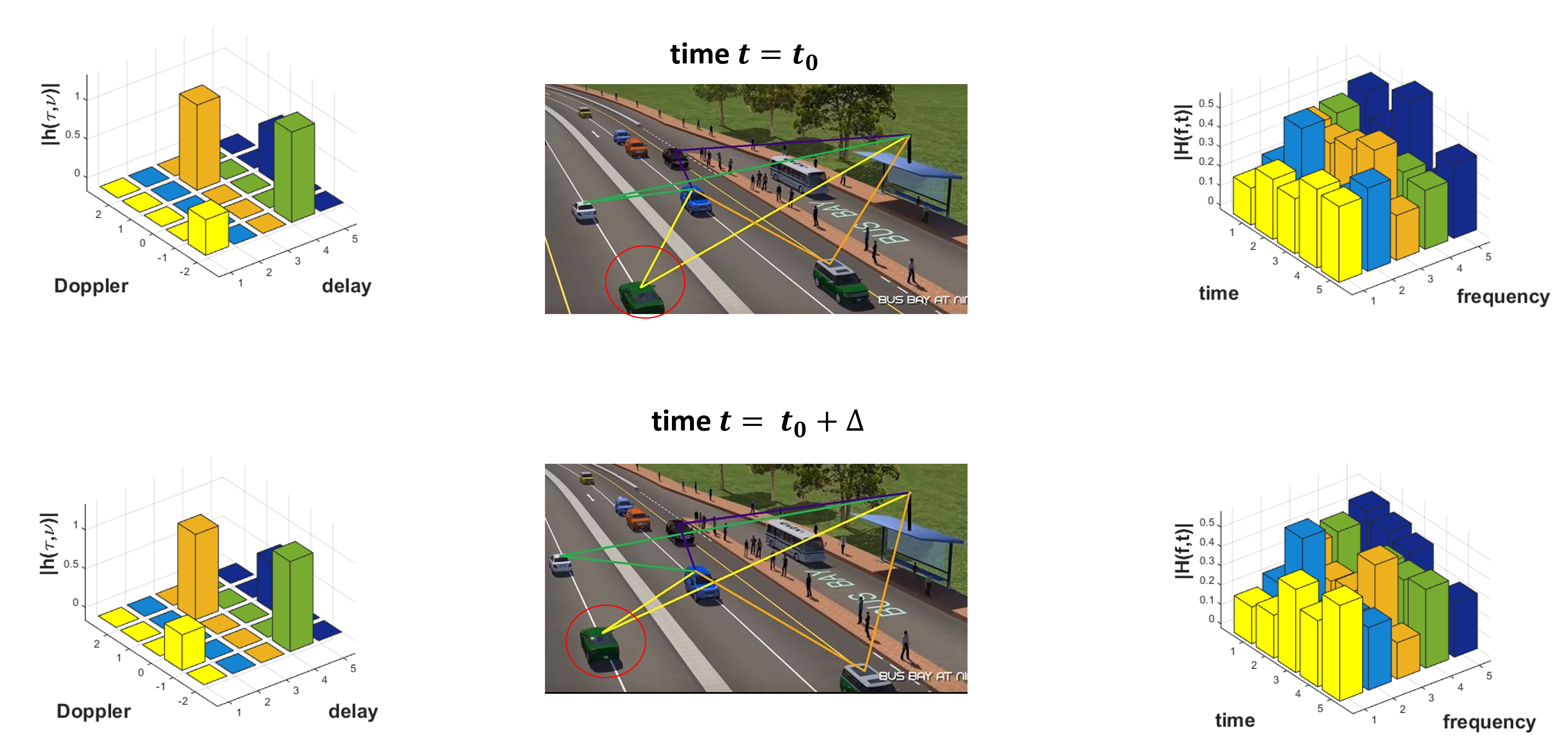
OTFS Modulation for 5G and Beyond
We have investigated a new modulation scheme called `Orthogonal Time...
read more...
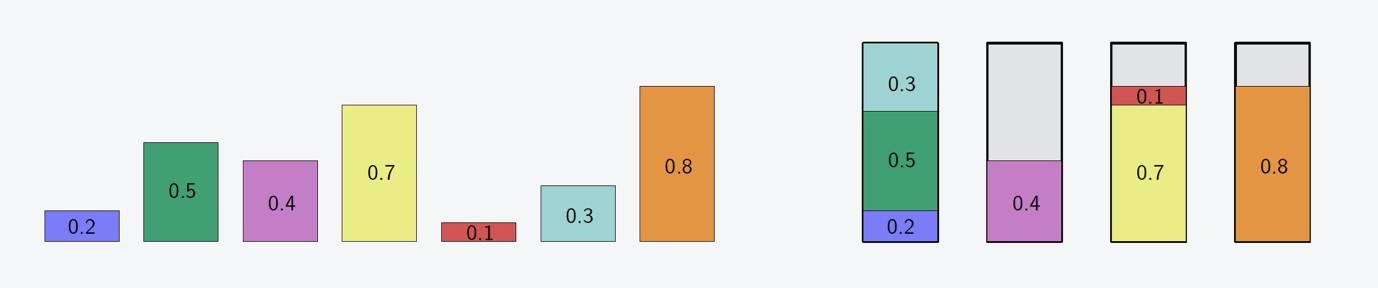
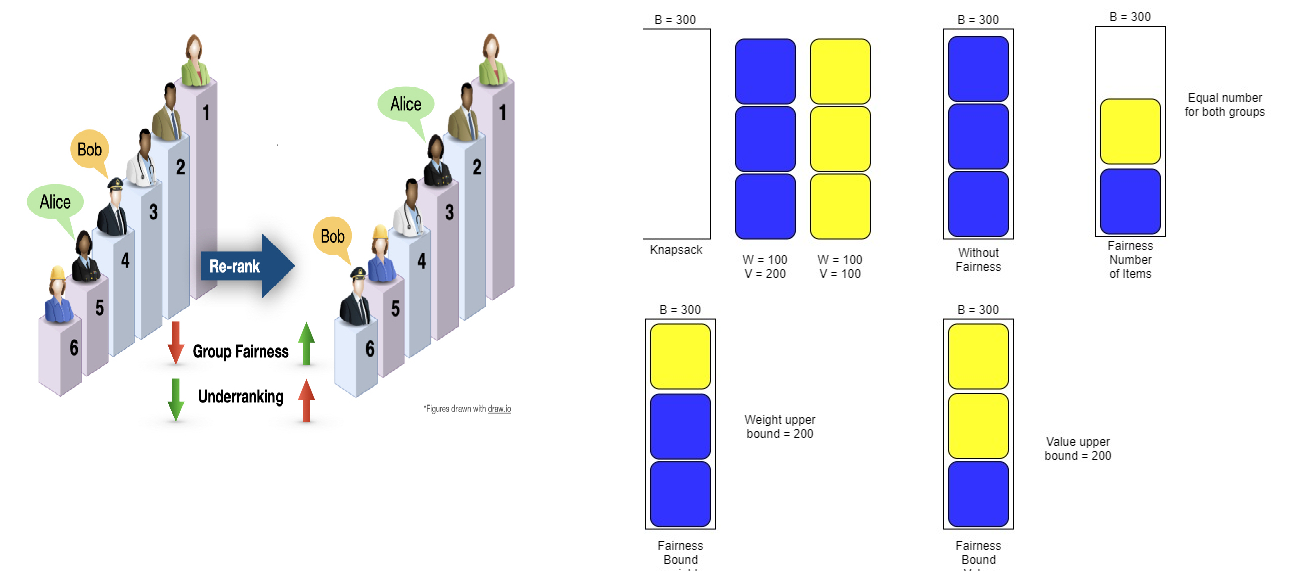
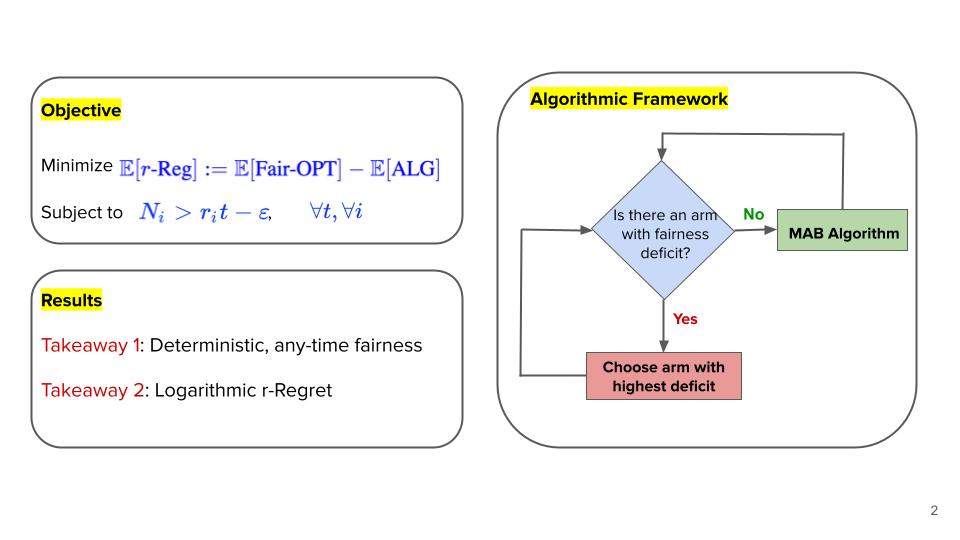
Algorithms with Fairness Guarantees
Humans are increasingly relying on algorithms to make decisions. Depending...
read more...
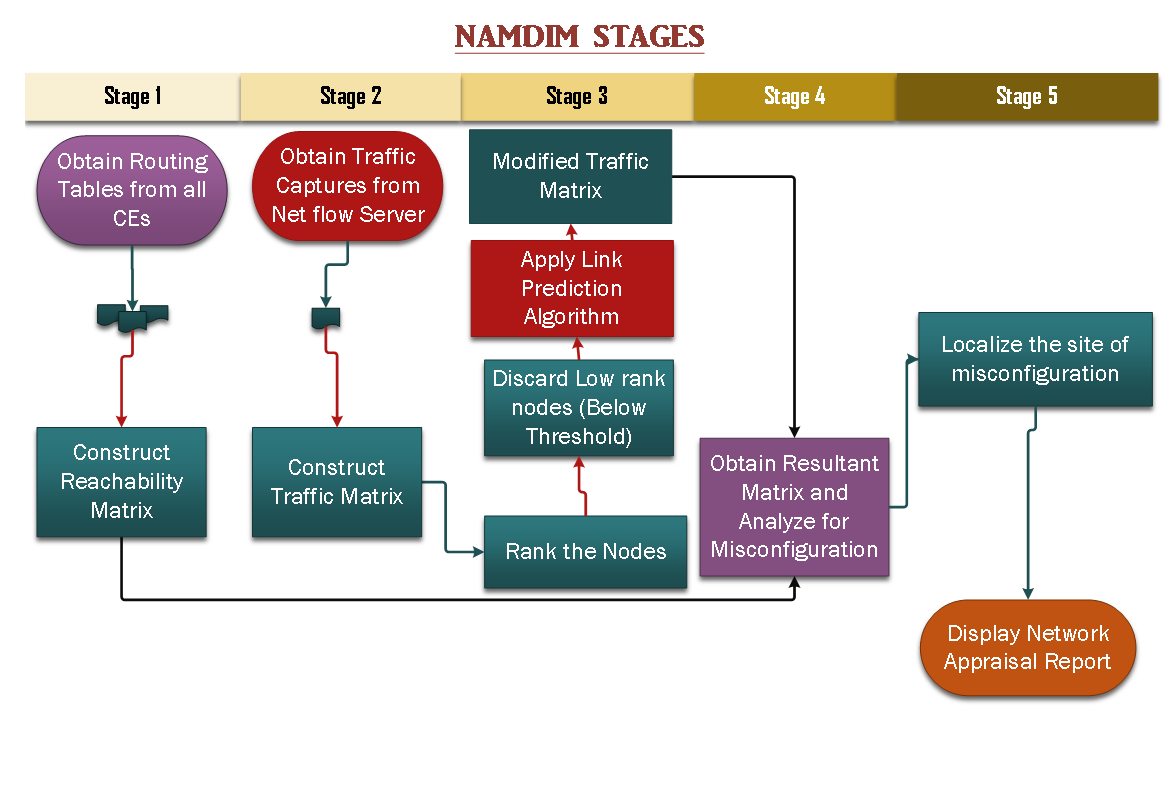
Detection of MPLS L3 VPN Misconfiguration
Misconfigured MPLS L3 VPNs violate customer’s privacy and security. With...
read more...
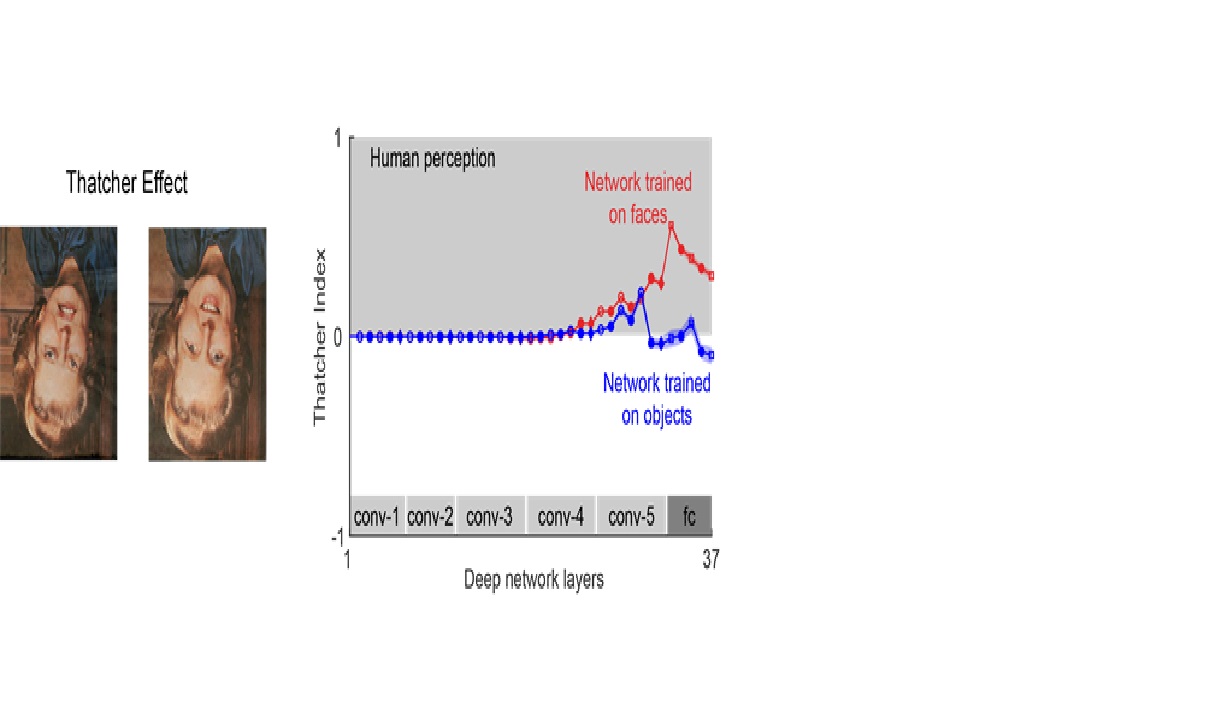
Do deep networks see the way we do?
In the Thatcher Effect (left), two inverted versions of Margaret...
read more...
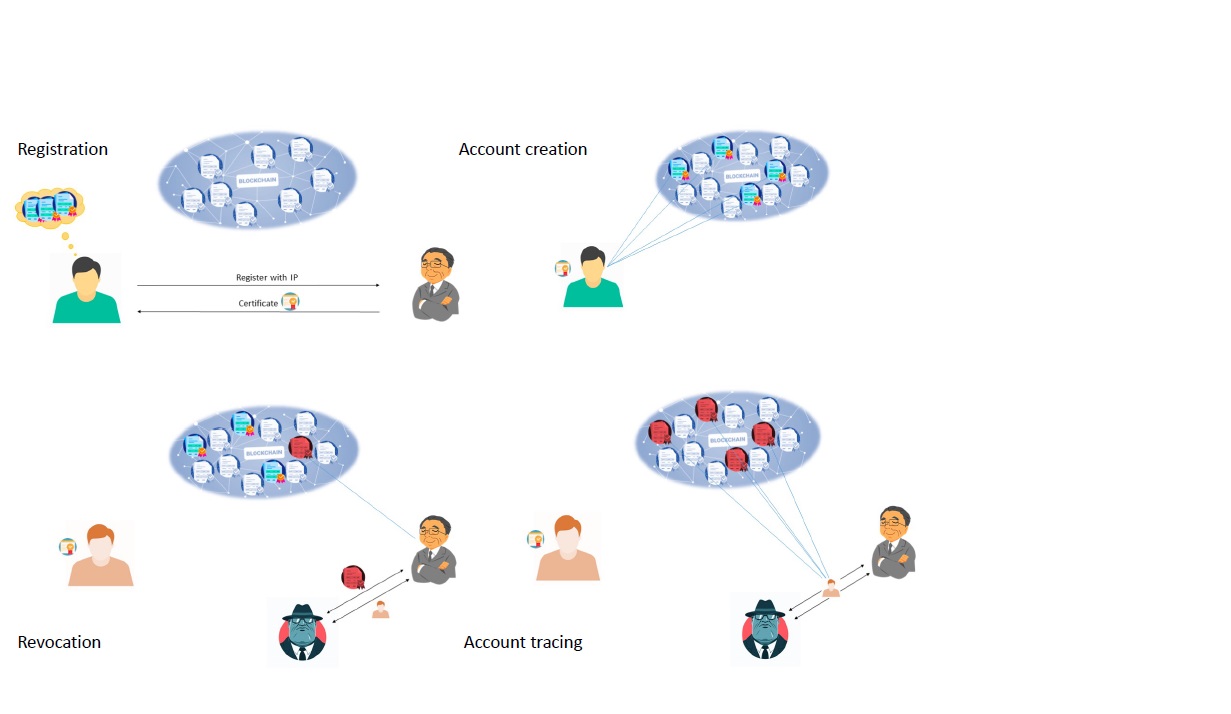
Balancing Privacy and Accountability in Blockchain Identity Management
To overcome the problem of lack of privacy in the...
read more...
ReXPlug: Explainable Recommendation using Plug and Play Language Model
Explainable Recommendations provide the reasons behind why an item is recommended...
read more...
CuBERT: BERT for Source Code Understanding
A significant advancement in natural-language understanding has come with the...
read more...
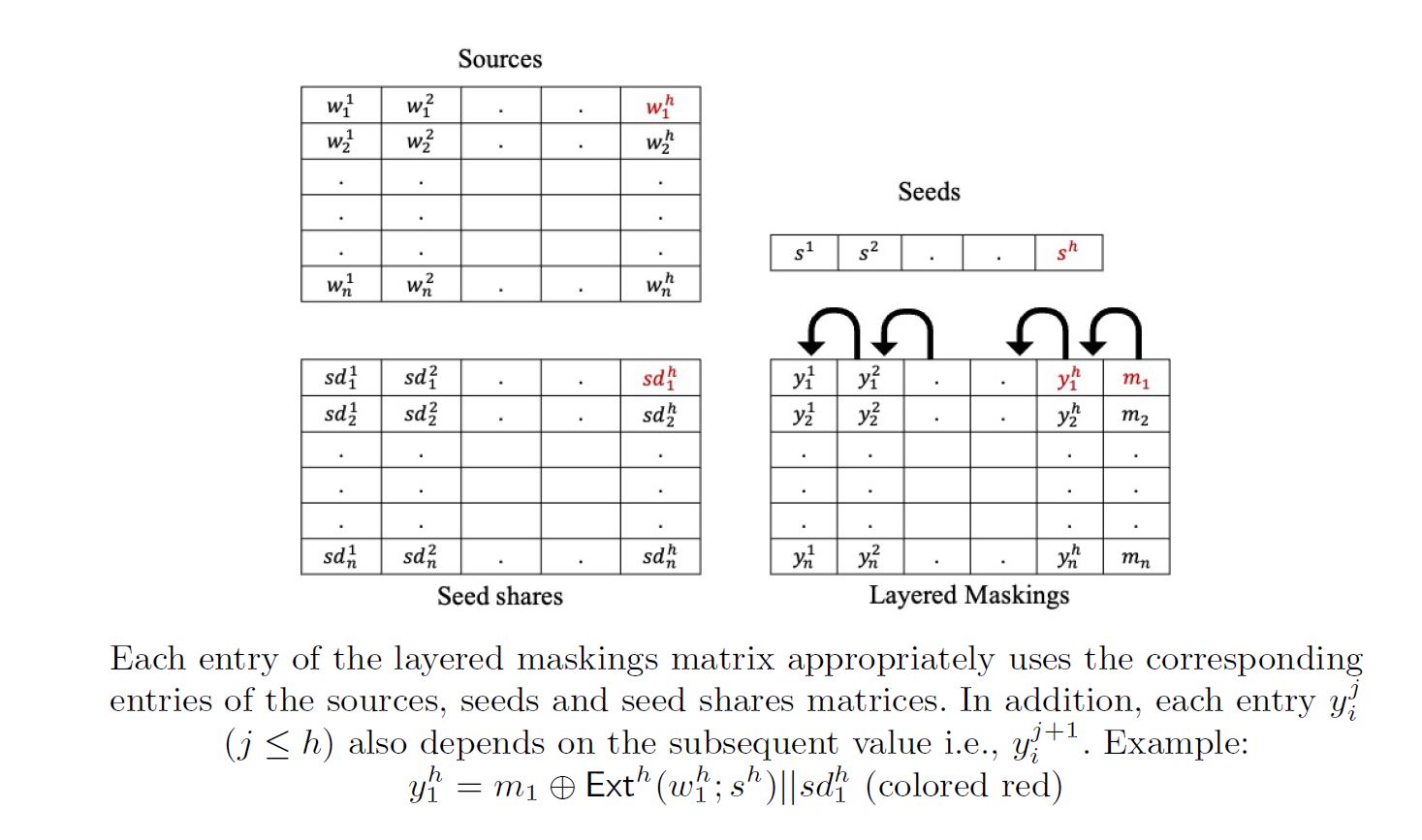
Adaptive Extractors and their Application to Leakage Resilient Secret Sharing
A Leakage Resilient Secret Sharing (LRSS) is a secure secret...
read more...
Soil’s electrical resistivity counters the fury of the lightning current
In addition to its many benign effects, lightning is one...
read more...
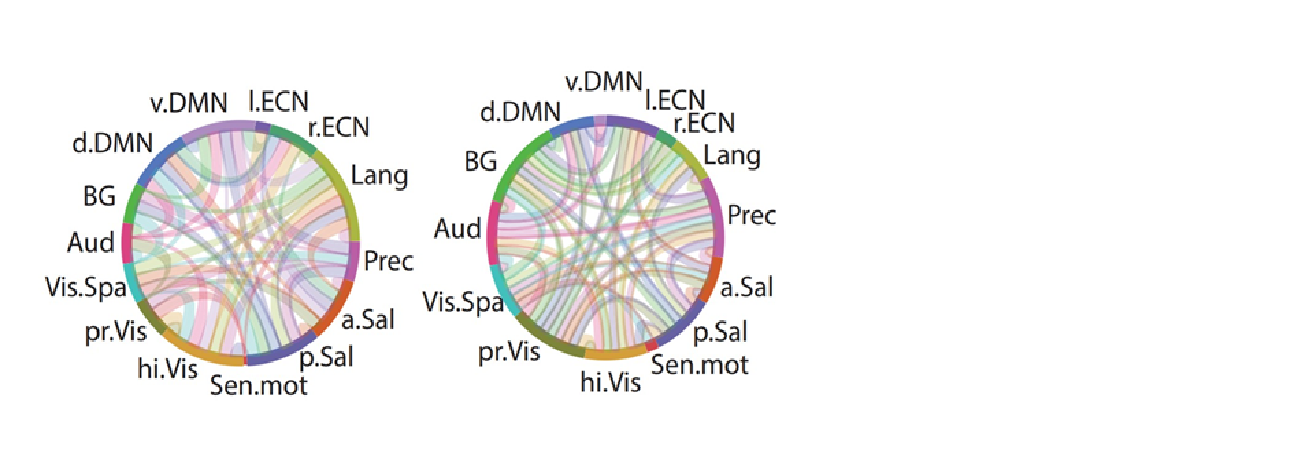
Decoding Task-Specific Cognitive States with Slow, Directed Functional Networks in the Human Brain
Functional MRI (fMRI) is a leading noninvasive technique for mapping...
read more...
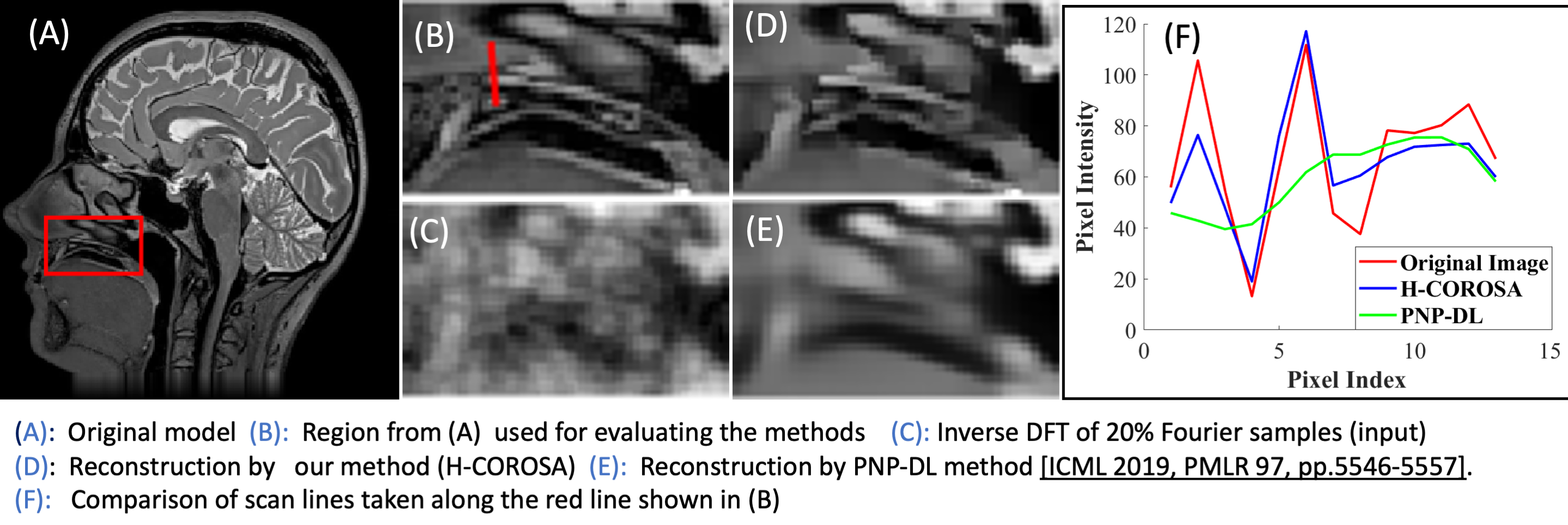
Image reconstruction from sparse Fourier samples using adaptive regularization
Magnetic resonance imaging (MRI) is one of the most important...
read more...
Deep-Interpolation: Fusion of multiple interpolations and CNN to obtain super-resolution
Architectures have been proposed that learn end‐to‐end mapping functions to improve the...
read more...
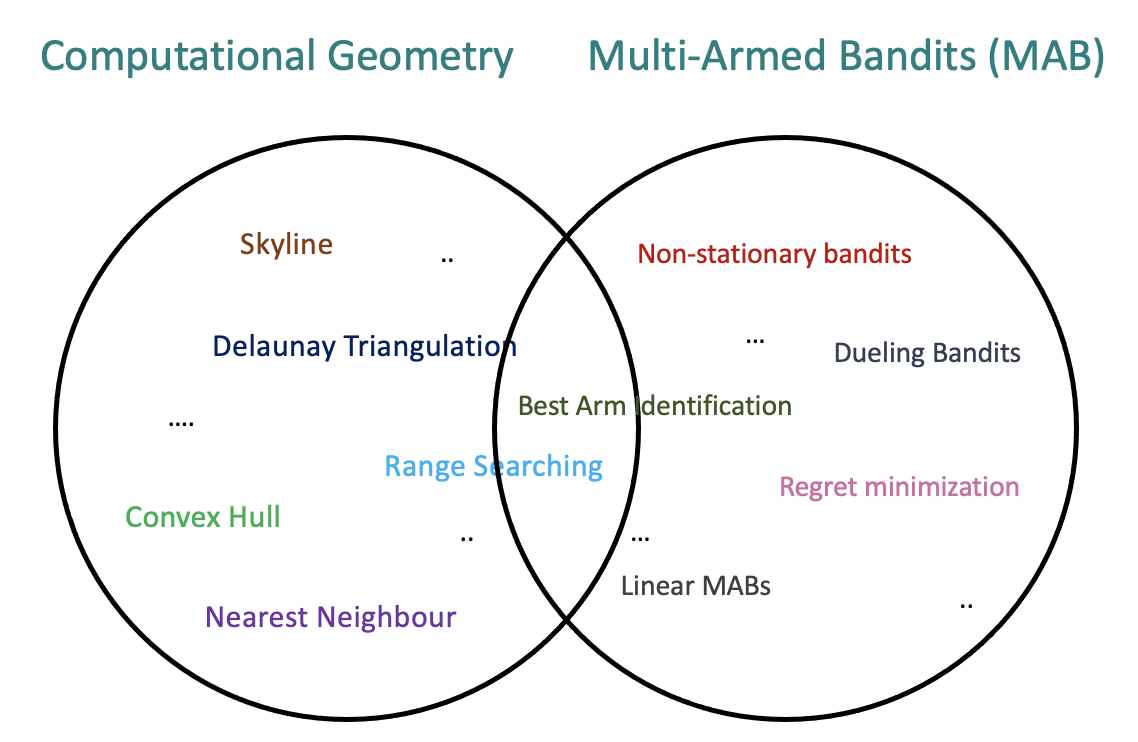
Computational Geometry Meets Multi-Armed Bandits
Computational geometry deals with the design and analysis of algorithms...
read more...
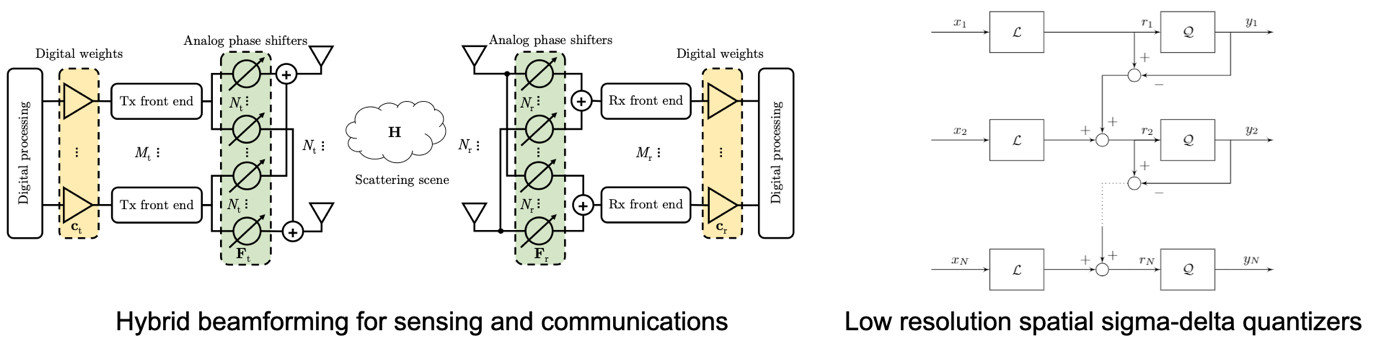
Hybrid Beamforming and Spatial Sigma-Delta Quantizers for mmWave MIMO systems
Sensor arrays are a key technology with several applications in...
read more...
Transient Stability of Grid Connected Photovoltaic Generations
To reduce carbon emissions into the environment, some of the...
read more...
Two-Timescale Stochastic Recursive Inclusions with Markov Noise
Stochastic approximation algorithms aim to find the zeros of an...
read more...
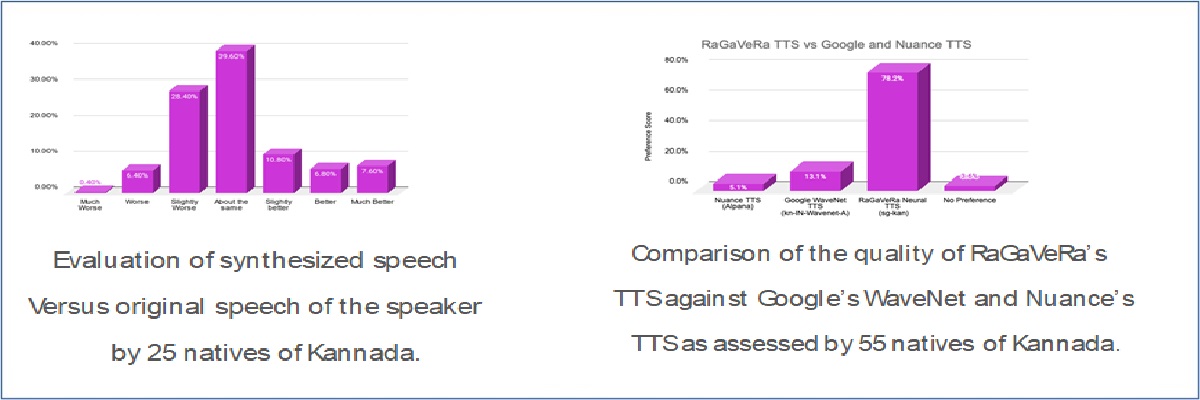
Human-Quality Kannada TTS using Transfer Learning on Tacotron2 and WaveGlow
RaGaVeRa Indic Technologies, a startup conceptualised at IISc by Ramakrishnan...
read more...
How do we make stochastic bandits fair?
Fairness is a key requirement in all decision making settings....
read more...
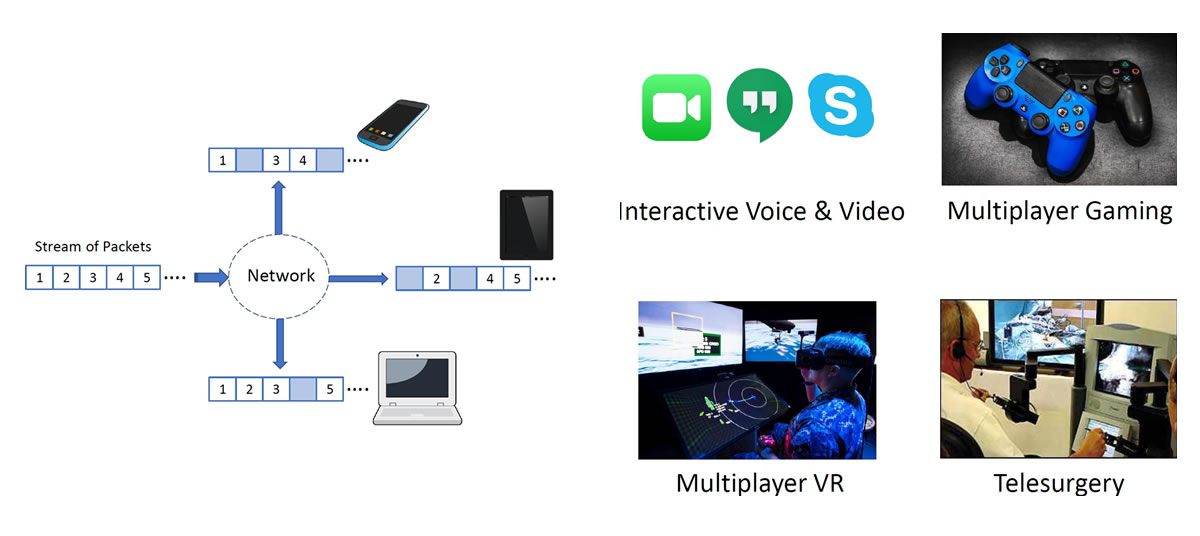
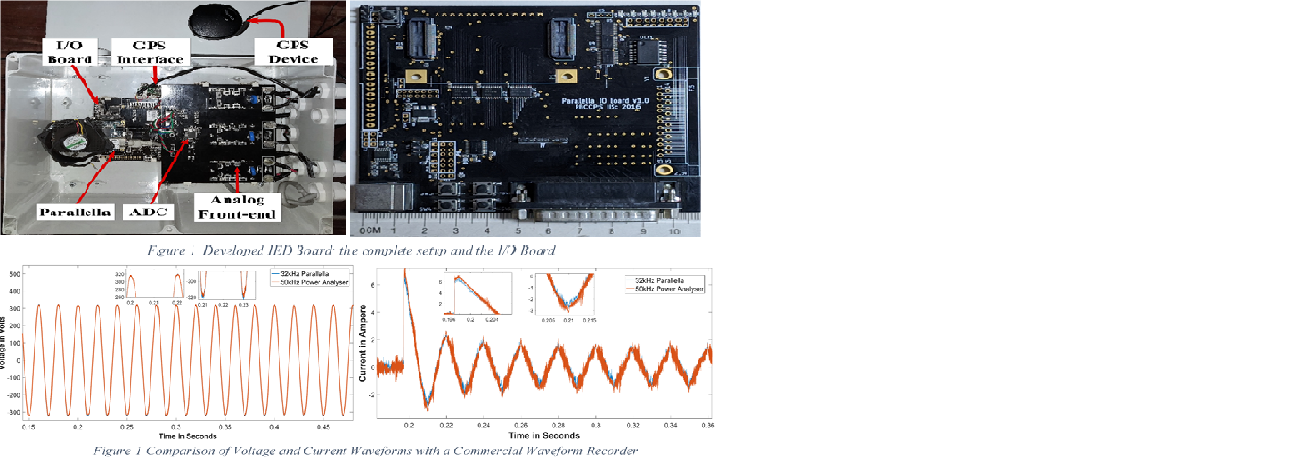
Network Resource Provisioning for Tactile Cyber Physical Systems
Imagine a person remotely controlling a robot at the wheel...
read more...
Platform for Smart Grid Measurements
This work involves design and implementation of a low cost,...
read more...
AI-driven XraySetu for early-Covid interventions over WhatsApp
The project was started by Dr. Geetha Manjunath of Niramai...
read more...
Designing the IZ4 Family of Spreading Codes for the NavIC L1 Signal
Global Navigation Satellite Systems (GNSS) employ periodic sequences having low...
read more...
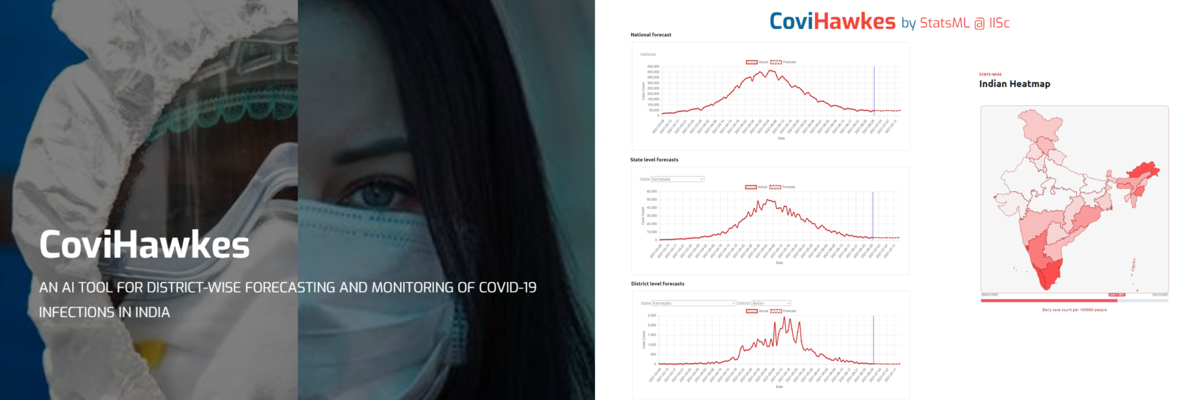
CoviHawkes: An AI tool for Covid-19
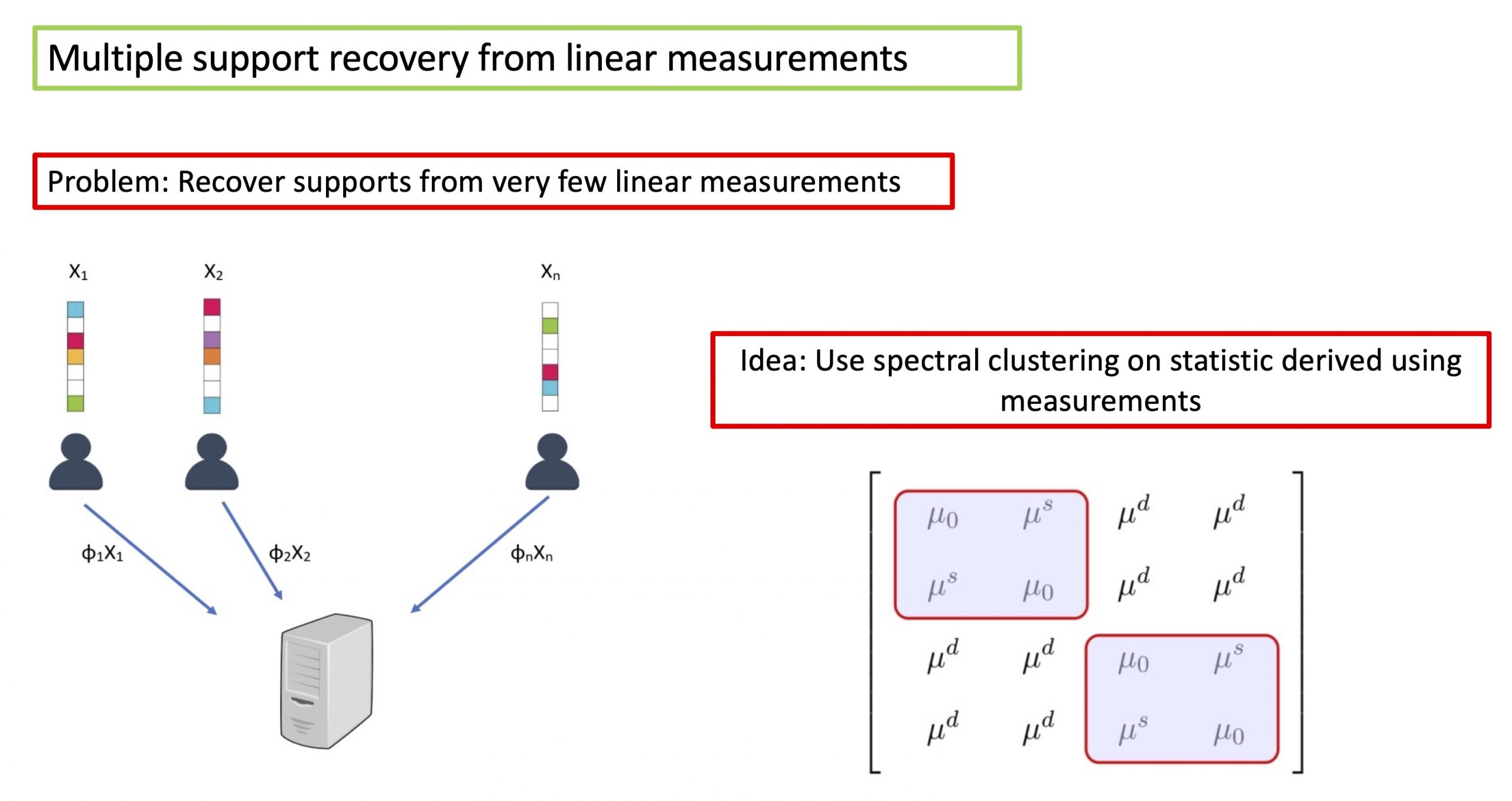
Multiple Support Recovery Using Very Few Measurements Per Sample
We study the problem of multiple support recovery from linear...
read more...
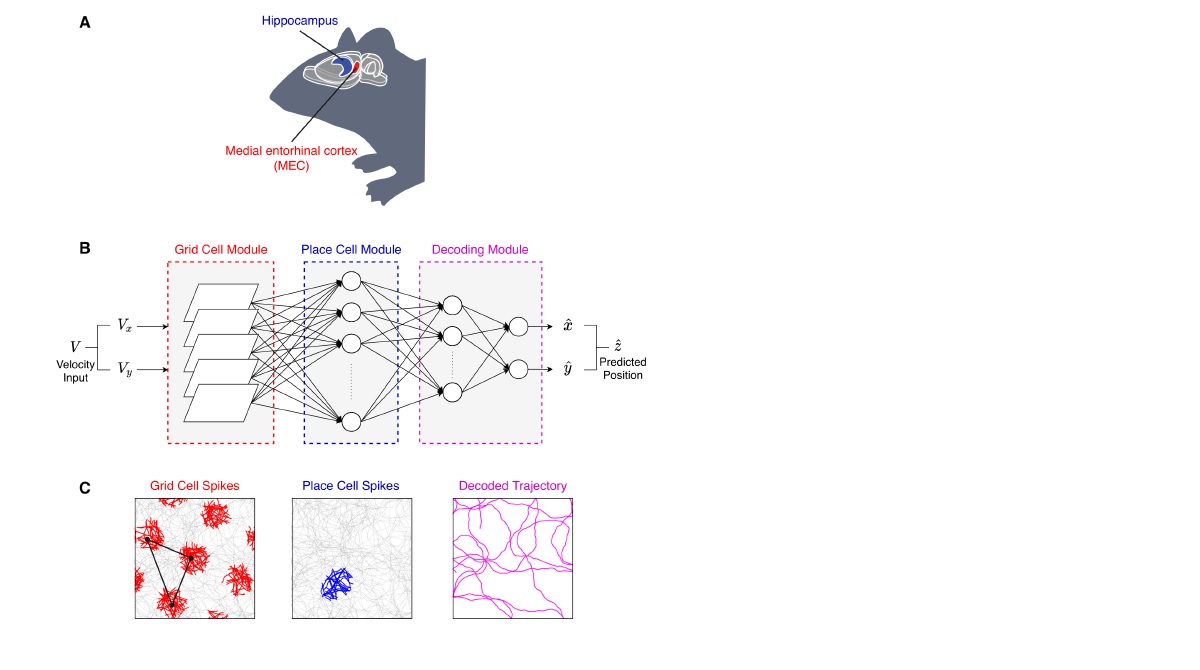
Neuromorphic spatial navigation system with Grid and Place cells
Efficient spatial navigation is extremely essential for the survival of...
read more...
Optimal Design and Control of Dual Active Bridge based Converters
Dual active bridge (DAB) isolated DC-DC converters are now widely...
read more...
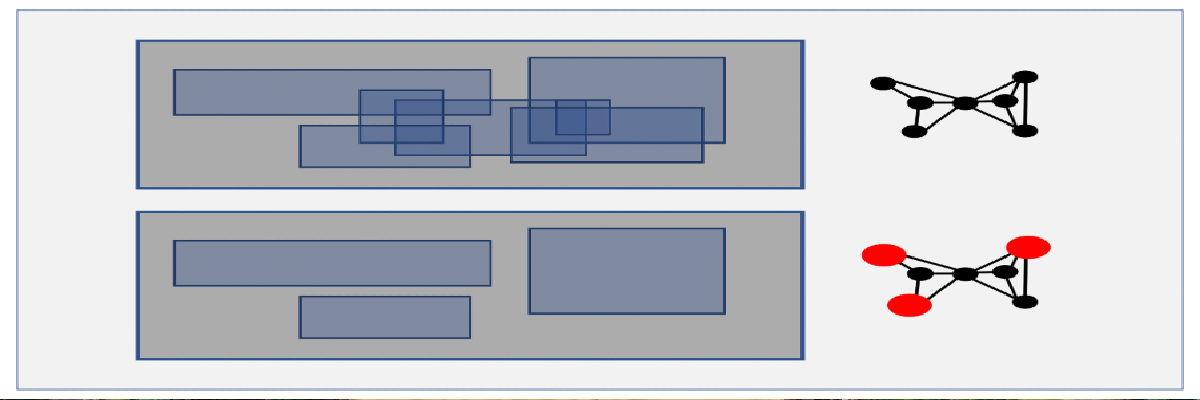
Breakthrough result in computational geometry
Maximum Independent Set of Rectangles (MISR) is a fundamental problem...
read more...
Plug-and-play (PnP)
Plug-and-play (PnP) is a recent paradigm for signal reconstruction from...
read more...
Next Generation Semiconductor Chip Testing with BIST and AI/ML
The semiconductor industry, with $600B+ in annual sales, is crucial...
read more...
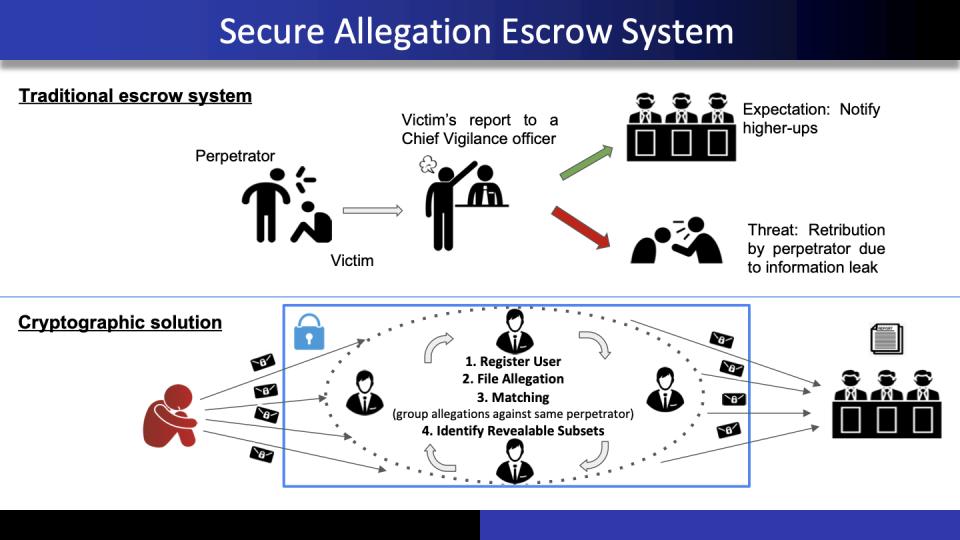
Secure Allegation Escrow System
The rising issues of harassment, exploitation, corruption and other forms...
read more...
How many rounds of conversation needed for Secure Computation?
The round complexity of interactive protocols is one of the...
read more...
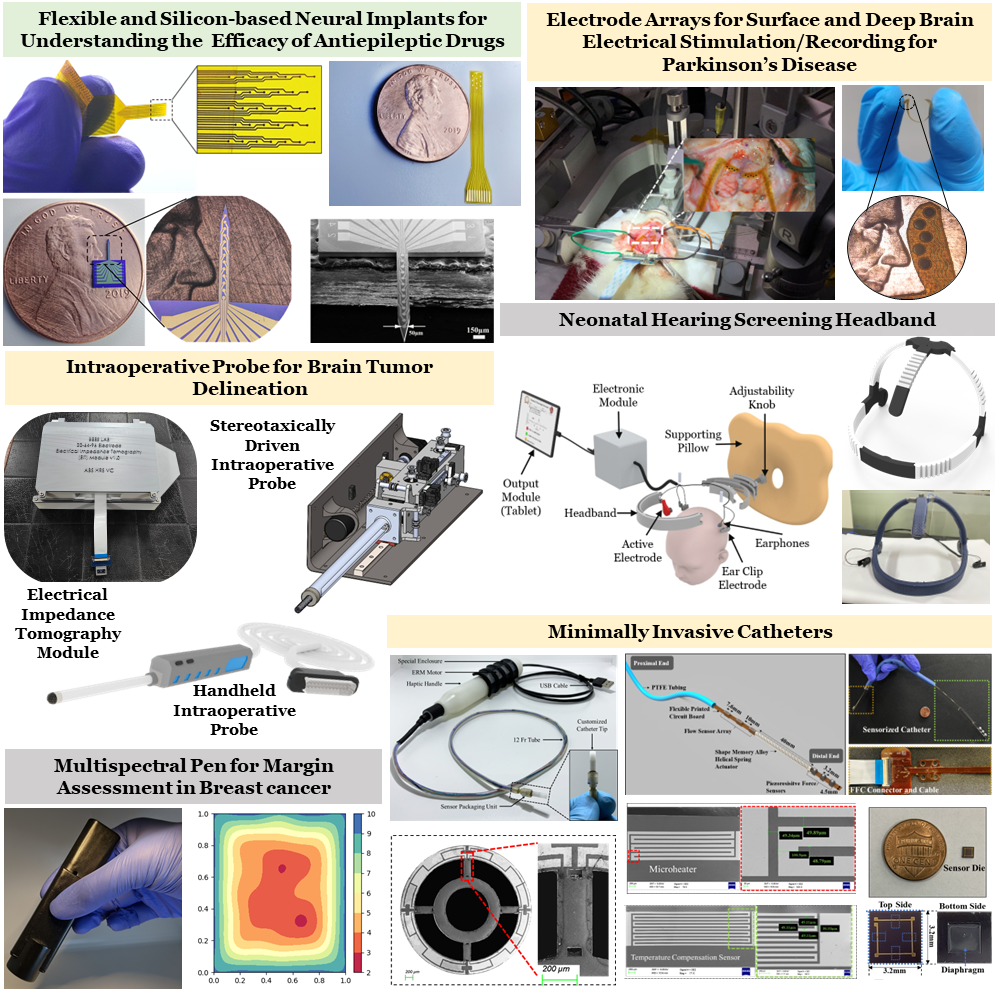
Indigenous Advanced Healthcare Technologies
Biomedical and Electronic (10-6 to 10-9) Engineering Systems (BEES) Laboratory...
read more...
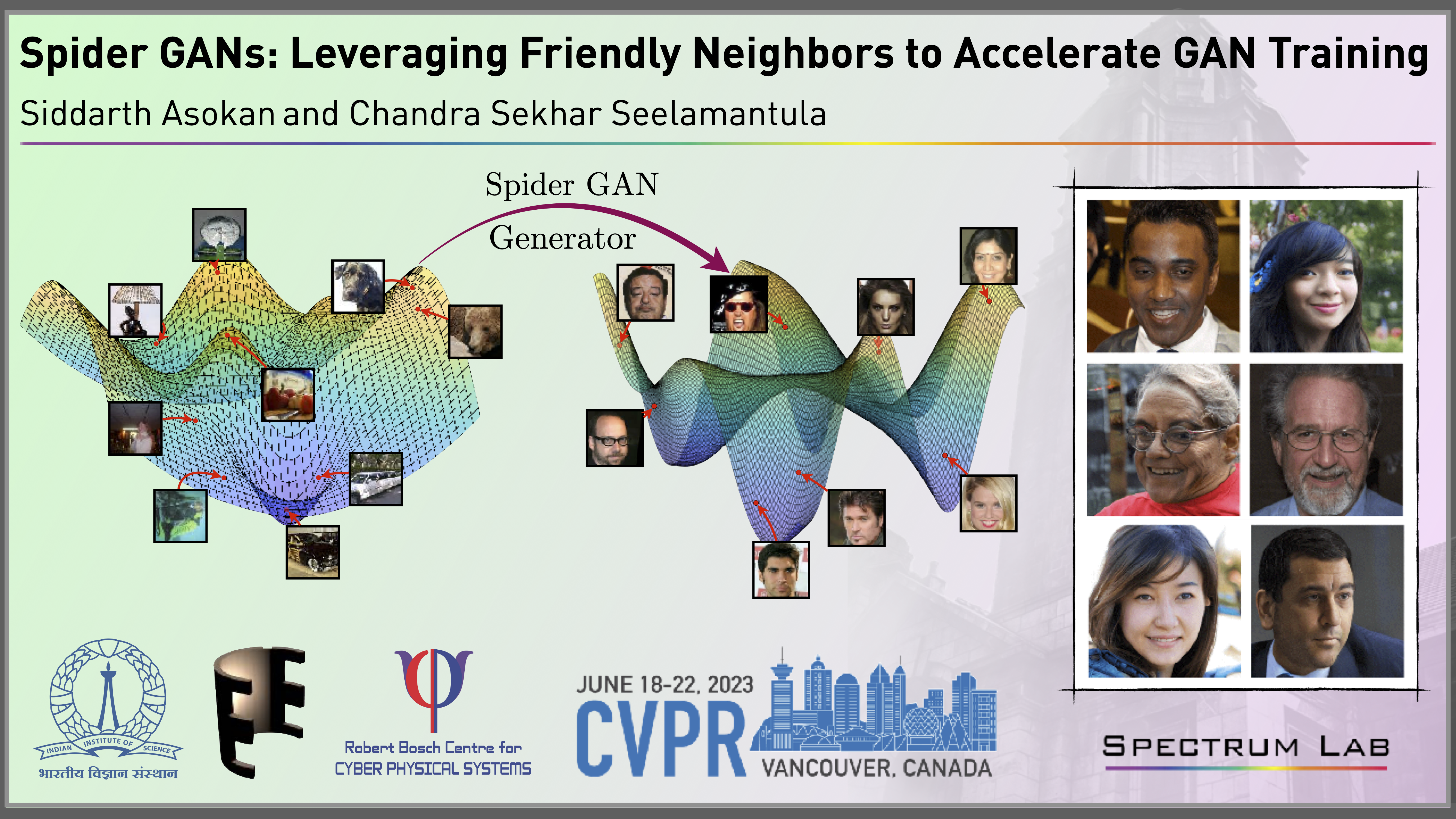
Spider GANs: Leveraging Friendly Neighbors to Accelerate GAN Training
Training Generative adversarial networks (GANs) is a challenging task. The...
read more...
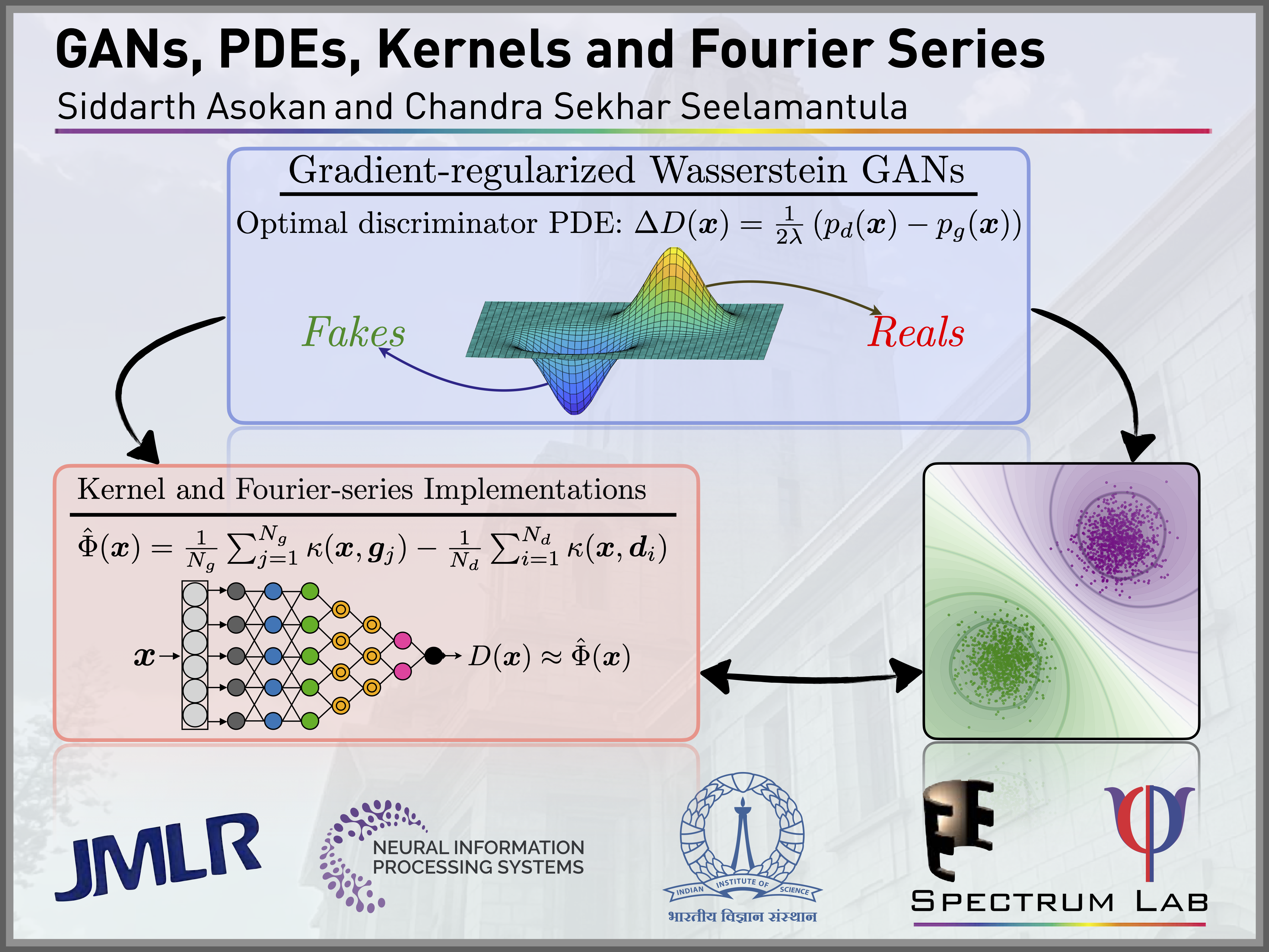
GANs, differential equations, kernels, and Fourier Series
Generative Adversarial Networks (GANs) comprise a generator network, which...
read more...
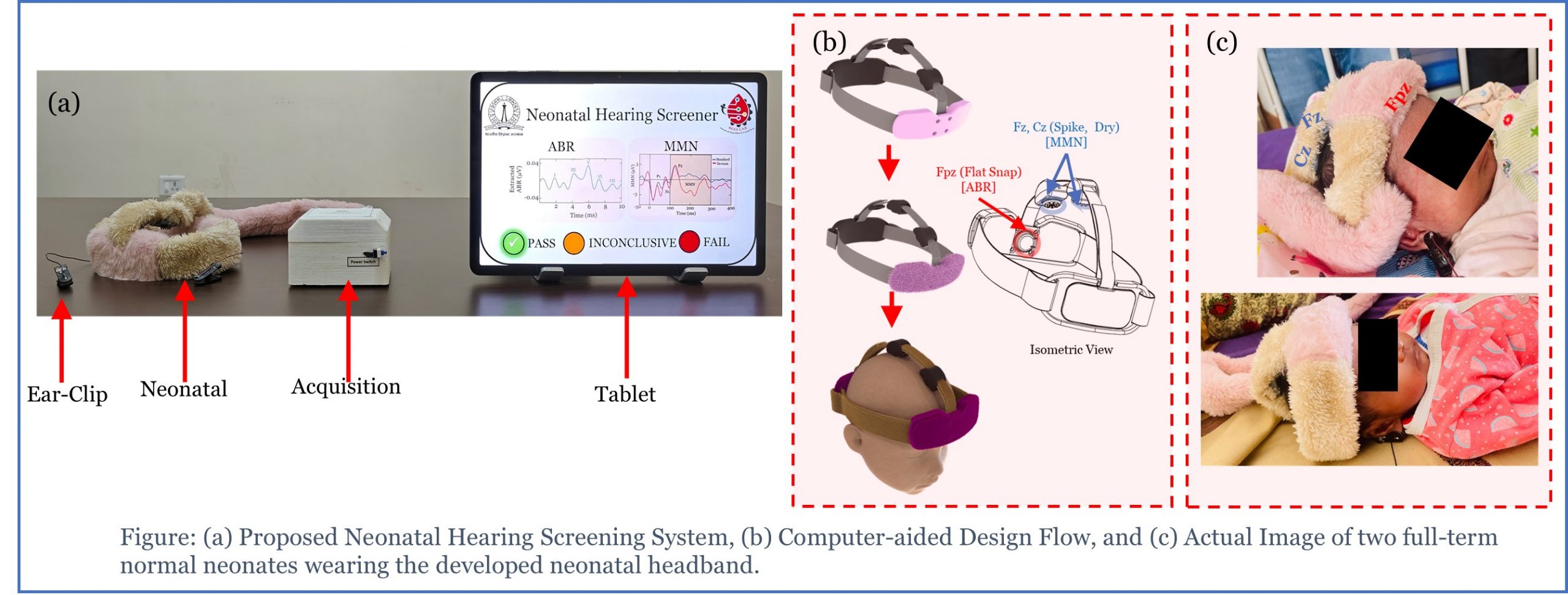
Neonatal Hearing Screening System Development and Validation
The proposed research explains a novel, affordable indigenous solution for...
read more...
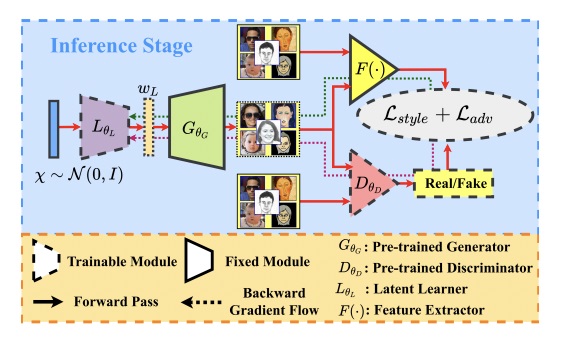
FEW-SHOT CROSS-DOMAIN IMAGE GENERATION
This work proposes a simple procedure to utilize a GAN...
read more...
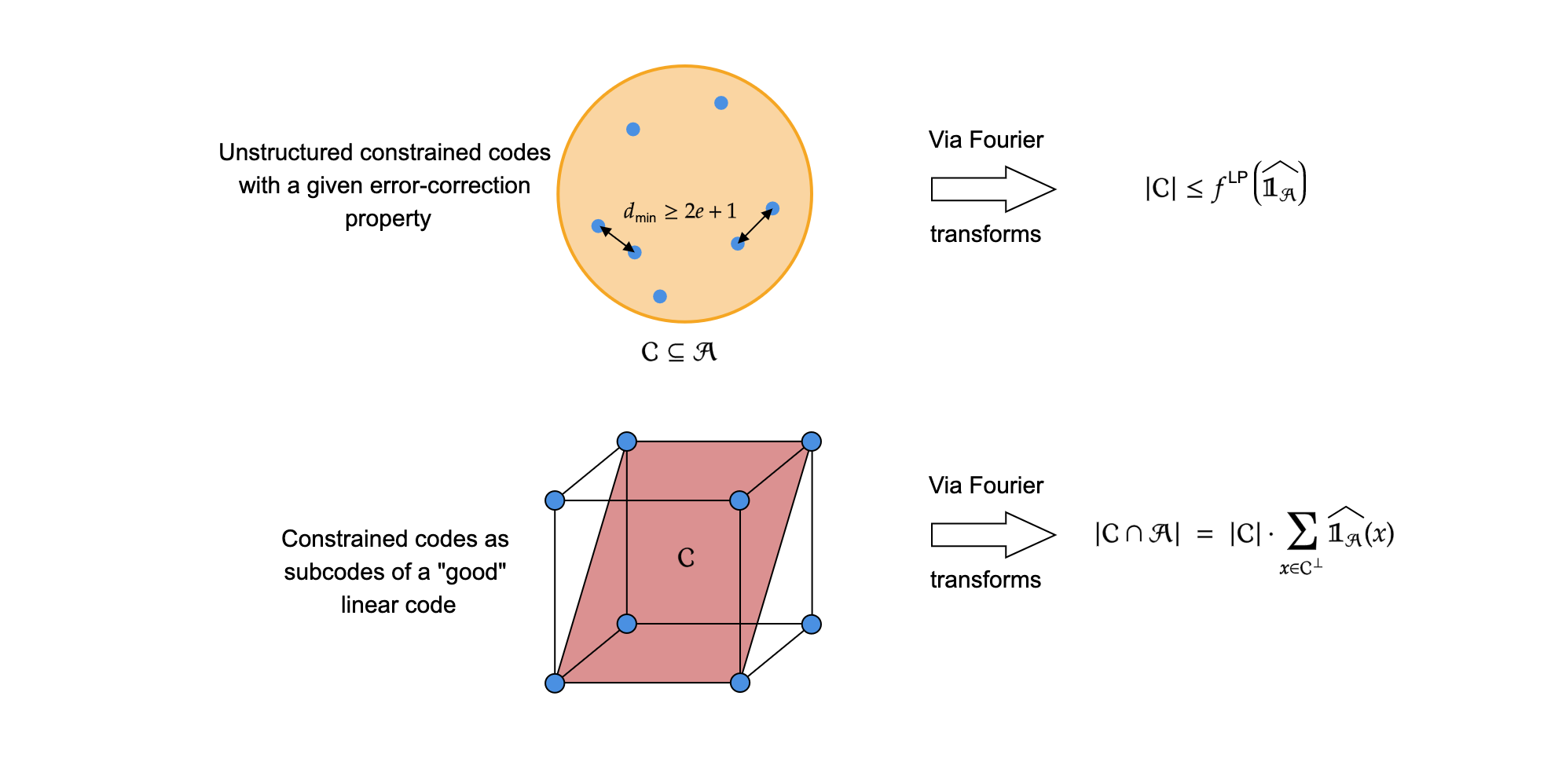
Estimating the Sizes of Error-Correcting Constrained Codes Via Fourier Expansions
In this work, we seek to address the problem of...
read more...
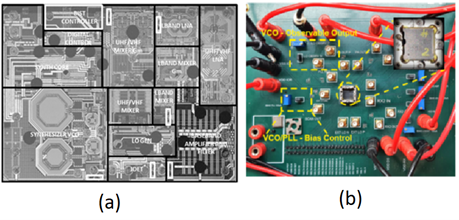
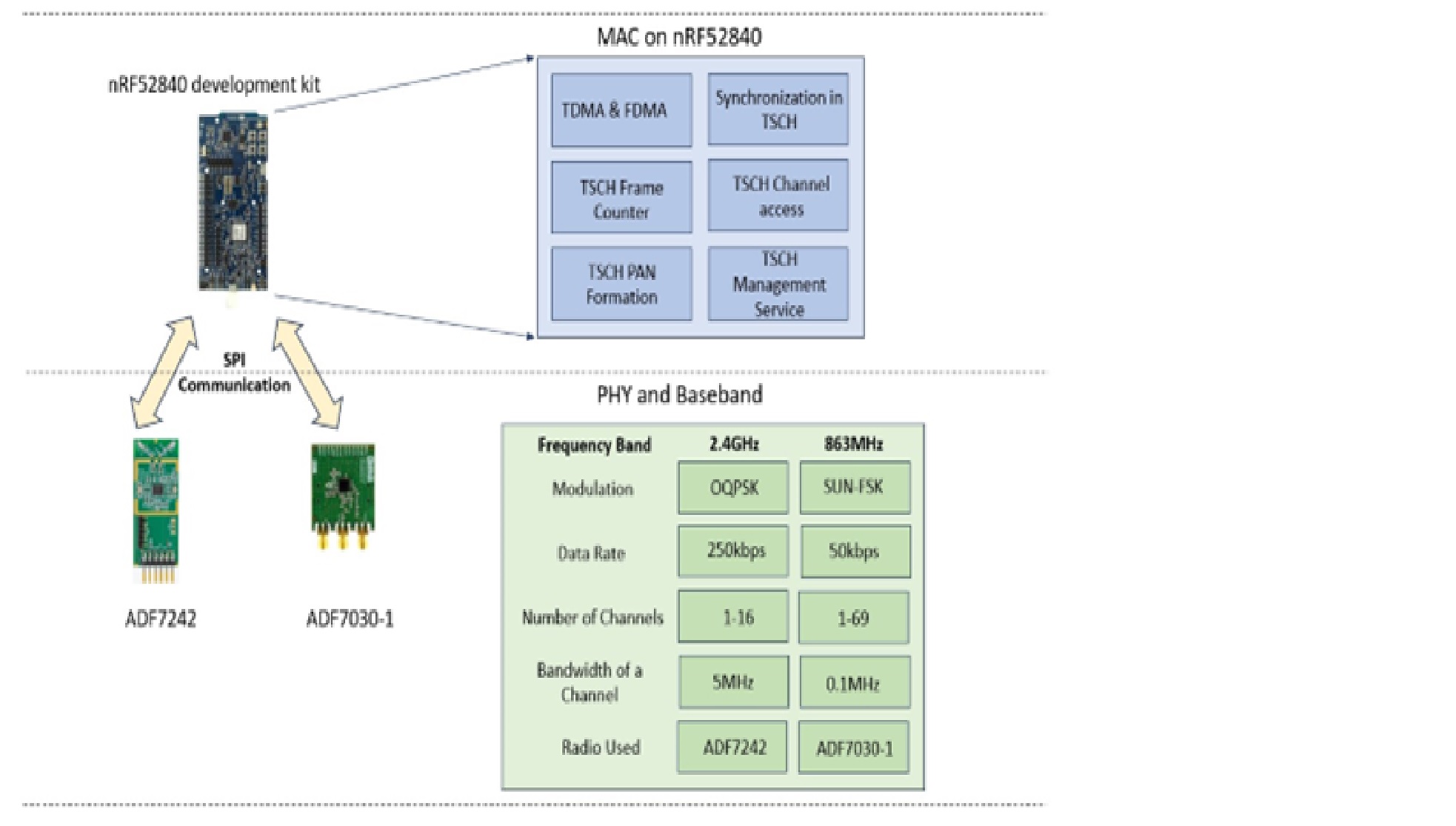
Design of Dynamic MAC and PHY SoC for Low Power and Long-Range Networks
The project aims at developing low power, long-range radios for...
read more...
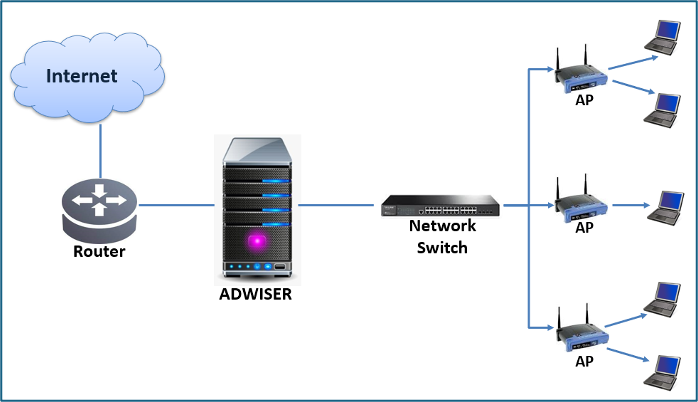
ADWISER: A Controller for Optimum Multi Access Point Coordination and QoS Management in Wi-Fi Networks
We design and implement multi-access point (AP) coordination in a...
read more...
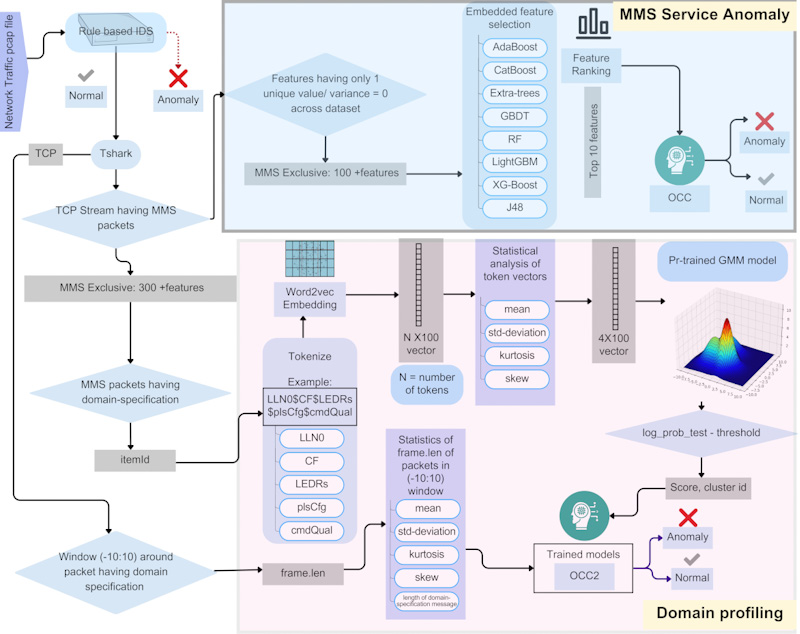
ML based Intrusion Detection System for IEC 61850 MMS
Cyberattacks targeting operational technology (OT) systems, such as power grids,...
read more...
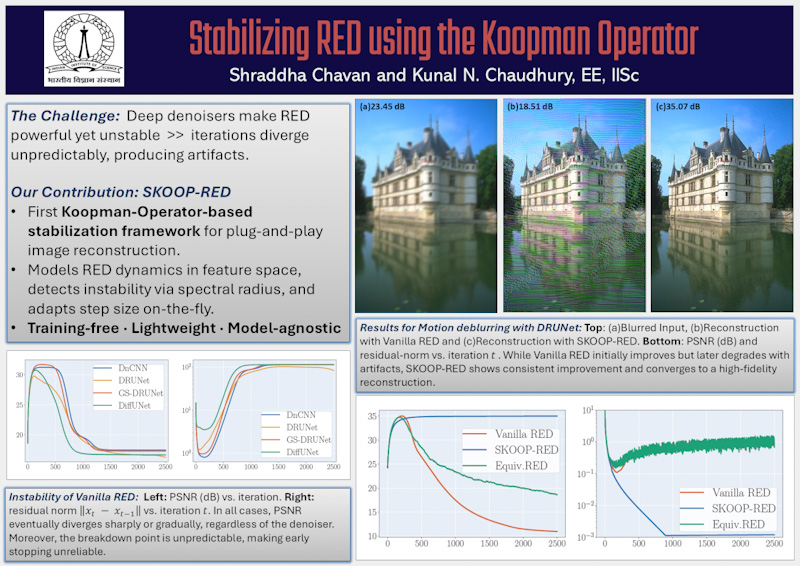
Stabilising RED using the Koopman Operator
Regularization-by-Denoising (RED) leverages pretrained denoisers as implicit priors for solving...
read more...
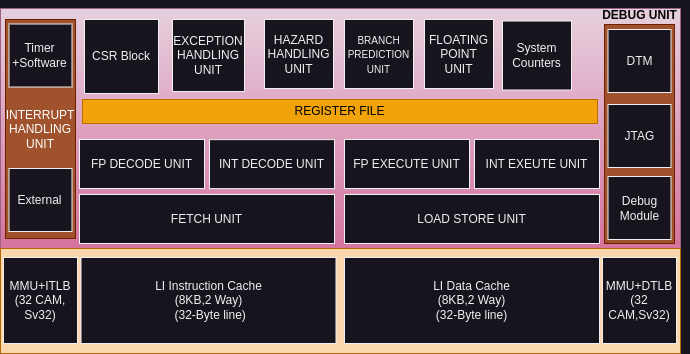
A 32-bit RISC-V ASIC Implementation
This work focusses on the design and development of a...
read more...
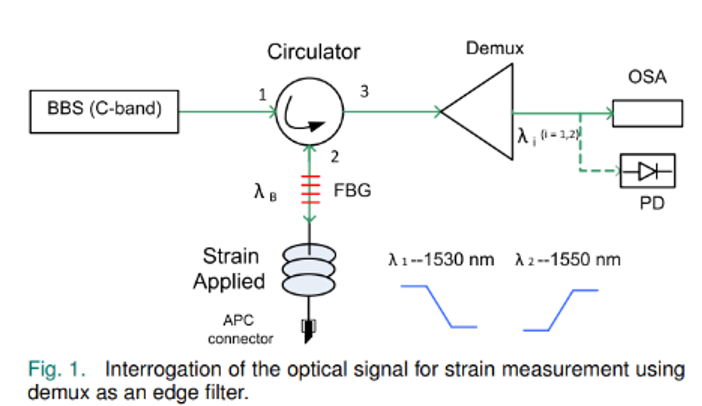
Wavelength to Intensity Conversion based Optical Interrogator
We explore an intensity-based interrogation technique using fused fiber demux...
read more...
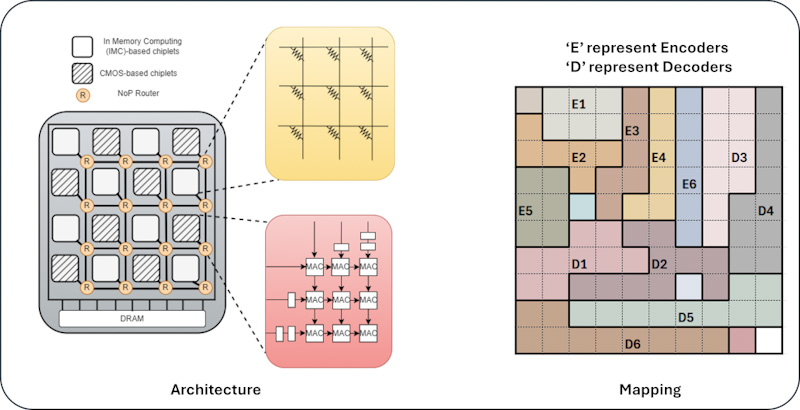
Communication-aware Heterogeneous 2.5 D System for Energy-efficient LLM Execution at Edge
Large language models (LLMs) are used to perform various tasks,...
read more...
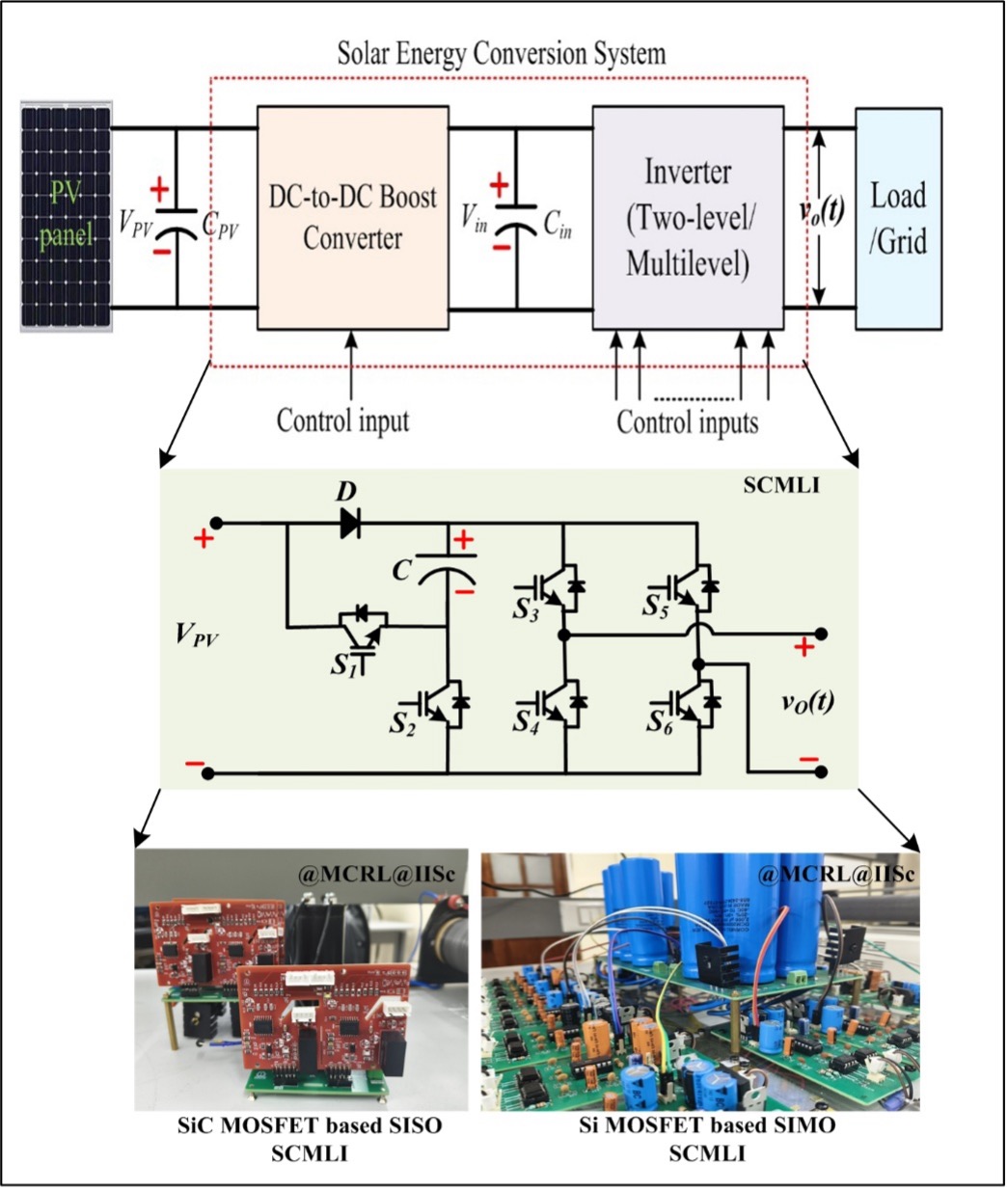
Switched Capacitor Multilevel Inverter (SCMLI): Next-generation DC–AC Power Converter
This work introduces several novel switched capacitor multilevel inverter (SCMLI)...
read more...
Scroll Up